Extended Detection and Response (XDR) has revolutionized how enterprises approach cybersecurity. Within this framework, Active Directory (AD) security deserves special attention. Most Fortune 1000 companies rely on Active Directory for identity and access management, making it a critical component of enterprise security. Active Directory Domain Services, a crucial component of AD, assists IT administrators in managing permissions and network access.
The merging of AD security with XDR platforms is not just a passing trend. It is a response to the reality that attackers consistently target AD while it continues to serve as the backbone of corporate identity systems. We will explore why this integration matters, how it helps fight current threats, and what you should know when implementing AD security in your XDR strategy.
Understanding the Modern Threat Landscape for Active Directory Domain Services
Why Attackers Target Active Directory
Hackers love going after Active Directory for several practical reasons. Attackers often examine IP addresses assigned to devices as part of their strategies while identifying vulnerabilities within the cyber-attack kill chain. It is the central authentication hub for most companies; compromise AD, and you potentially control everything. AD’s hierarchy creates multiple paths for attackers to climb from regular user accounts to domain admin privileges. Attackers can use AD components like service accounts, GPOs, and trust relationships to maintain persistent access. The rise of hybrid setups connecting on-site AD to cloud services has created even more attack vectors.
According to the U.S. Department of Defense, Active Directory remains a primary target for cyber threats due to its extensive permissions and complex relationships, making its security crucial.
Evolution of AD-Focused Attacks
The ways attackers target AD have gotten much more sophisticated. They use legitimate Windows tools to move through AD environments, making their activities hard to spot with standard security tools. Microsoft Defender is a comprehensive security solution focused on identity monitoring and threat detection, enhancing security by correlating data across various domains. Supply chain attacks inject malicious code into trusted software that specifically targets AD infrastructure. Beyond stealing passwords, attackers manipulate Kerberos tickets, exploit directory replication, and use NTLM relay attacks.
Ready-made tools for AD reconnaissance and exploitation have made these attacks accessible to less technical attackers. Recent cybersecurity reports indicate that attackers are compromising Active Directory environments faster than ever, with breach timelines shortening significantly year over year.
The Convergence of Active Directory Security and XDR
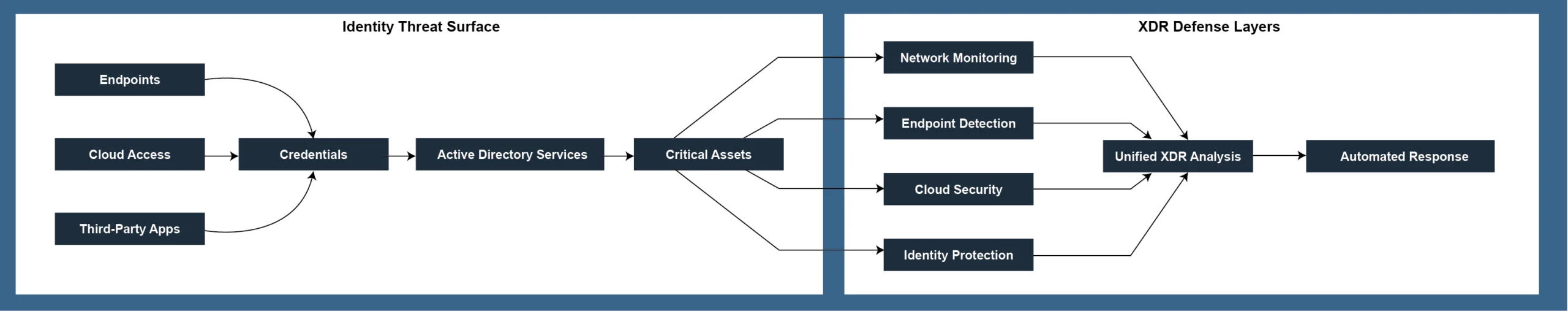
What XDR Brings to Active Directory Security
XDR platforms extend visibility beyond endpoints. Effective security management requires integration and automation to reduce risks and optimize resource allocation. For AD security, this approach offers major benefits. XDR connects the dots between AD security events and activities across networks, endpoints, and cloud services; this context is impossible with standalone monitoring tools. The behavior analytics in modern XDR solutions establish normal AD activity patterns and flag anomalies that might slip past traditional security. When AD threats appear, XDR can automatically respond, isolating systems or resetting compromised credentials. XDR platforms integrate threat intelligence specific to AD attack methods, helping security teams stay ahead of emerging threats.
Active Directory Security Challenges Addressed by XDR
XDR tackles several tough challenges in securing AD environments. Standard security tools often miss AD-specific attack techniques; XDR platforms with AD security focus monitor directory changes, authentication patterns, and privilege adjustments. AD attacks are complex and often go undetected for long periods. XDR’s cross-domain correlation catches subtle signs of compromise that might otherwise be missed.
Responding to AD breaches typically requires specialized expertise. XDR platforms include response playbooks specifically for AD threats. Attackers frequently exploit trust relationships between domains or with cloud services; XDR solutions monitor these trust boundaries. Security studies suggest that strengthening AD security within XDR can lead to substantial reductions in breach-related costs, improving overall cybersecurity resilience.
Stay ahead of attackers with advanced AD threat detection and deception. Key Insights Inside:
- How Fidelis AD Intercept™ detects hidden threats
- Role of deception technology
- Importance of real-time monitoring
How Fidelis Active Directory Intercept™ Is an Important Part of Fidelis XDR
Fidelis Elevate®, the company’s XDR platform, integrates powerfully with Fidelis Active Directory Intercept™ to provide comprehensive protection for this critical infrastructure. This integration demonstrates the ideal approach to AD security within an XDR framework.
Fidelis Active Directory Intercept™ combines AD-aware network detection and response with integrated deception technology and foundational AD log monitoring. This multi-layered approach gives security teams contextual intelligence about how, where, and how deeply adversaries have penetrated AD environments.
The solution’s AD-specific capabilities strengthen Fidelis Elevate’s overall XDR platform by providing full visibility into AD objects for deeper insight across organizational resources and access paths. It offers early warning of AD misconfigurations and indicators of compromise before they escalate. The solution delivers robust defense through network sensors combined with AD configuration monitoring. It enables real-time response capabilities through automation and forensic analysis tools.
Active Threat Detection for AD-Specific Threats
Fidelis Network®, a core component of the solution, delivers AD-focused threat detection capabilities. Active Threat Detection correlates alerts and provides high-confidence detections that map attempted AD attacks directly to MITRE ATT&CK tactics, techniques, and procedures. Deep Session Inspection finds threats to AD hidden within nested and obfuscated files as they move across the network. In-line or out-of-band encrypted traffic analysis catches attacks that might otherwise remain hidden.
Contextual intelligence provides comprehensive details about attacker movements before, during, and after an attack.
Integrated Deception Technology for AD Protection
Fidelis enhances its XDR capabilities with intelligent deception specifically designed for AD environments. Terrain mapping and risk profiling help understand where attackers are likely to strike. Automated deployment of convincing decoys, including AD objects in both on-premises and Azure AD environments, leads attackers away from real assets. Strategic placement of breadcrumbs throughout the network directs attackers away from legitimate AD users and domains.
Deception technology gives defenders time to study threats while keeping adversaries distracted, a critical advantage when protecting Active Directory. High-confidence, actionable alerts definitively identify active network threats in real time.
Comprehensive AD Monitoring and Detection
Fidelis Active Directory Intercept™ expands XDR visibility with specialized AD monitoring. It provides a hierarchical view of the entire AD environment with detailed information on all Active Directory entities such as users, computers, groups, and domains. The solution detects AD misconfigurations that create security vulnerabilities before attackers can exploit them. Real-time detection of malicious activity with automated response capabilities speeds incident resolution.
This specialized AD monitoring enables detection of sophisticated attacks that traditional security tools miss, including Active Directory reconnaissance, Kerberoasting, LLMNR poisoning, DCSync attacks, DCShadow attacks, and brute-force authentication attempts.
- Fidelis Elevate® integrating with AD security
- Power of XDR in detecting and mitigating AD-specific threats
- Use cases of Fidelis Elevate®
Key Components of Active Directory Security in XDR
Identity Threat Detection and Response (ITDR)
ITDR sits at the heart of AD security within XDR, focusing on identity-based threats. Malicious users can compromise a user account, often remaining undetected and causing significant damage, which emphasizes the importance of monitoring and securing these accounts. It monitors authentication events to catch anomalies like impossible travel scenarios or brute force attempts. It tracks privilege escalation and permission changes within the directory. It detects suspicious modifications to the directory service database in real-time.
It connects with dark web monitoring to identify when company credentials have been exposed. An increasing number of organizations recognize ITDR as a vital component of their security strategy, with adoption rates growing steadily over the past year.
Active Directory Threat Hunting Capabilities
Effective XDR includes specific AD threat hunting tools. Attack path analysis automatically maps potential routes through AD infrastructure, helping teams address vulnerabilities proactively. Continuous scanning catches common AD misconfigurations before attackers can exploit them. Specialized detection mechanisms identify Kerberos ticket manipulation attacks.
Monitoring flags unauthorized changes to Group Policy Objects that might signal malicious activity. Threat-hunting initiatives focused on Active Directory have revealed multiple hidden compromise scenarios each month, underscoring the need for proactive monitoring.
Active Directory Protection in XDR Response Workflows
Beyond detection, XDR platforms include AD-specific response capabilities. These include automated credential reset for potentially compromised accounts and temporary privilege downgrading when suspicious activity appears. Emergency protocols to isolate compromised domains from trusted ones can prevent lateral movement. Streamlined processes to restore AD to a known-good state after compromise minimize recovery time.
Implementation Considerations for AD Security in XDR
Integration Requirements
Successfully integrating AD security into XDR requires attention to several key points.
- The XDR solution needs appropriate access to monitor AD events without creating security risks through excessive permissions.
- Windows Event Forwarding must be properly configured to ensure all relevant AD security events reach the XDR platform.
- In hybrid environments, XDR must connect with both on-premises AD and cloud identity services.
- Integration with Privileged Access Management solutions helps the XDR platform monitor privileged account activities.
Common Deployment Challenges
Companies implementing AD security within XDR typically face several hurdles.
- Comprehensive AD monitoring can strain domain controllers; XDR solutions must minimize this performance impact.
- Distinguishing between legitimate admin activities and actual threats requires careful tuning of detection rules.
- Legacy AD deployments may have compatibility issues with modern XDR solutions.
- Certain industries face specific compliance requirements for identity monitoring that must be addressed.
The Future of Active Directory Security in XDR
Emerging Trends
Several trends are shaping how AD security fits into XDR platforms. Next-gen XDR solutions use AI to build detailed behavioral models of normal AD activity, enabling more accurate anomaly detection. XDR platforms increasingly incorporate zero trust principles, continuously validating access attempts against risk assessments.
As multi-cloud strategies grow, XDR solutions are evolving to protect identities across on-premises AD, Microsoft Entra ID, and third-party providers. In response to supply chain attacks, XDR platforms are developing ways to verify the integrity of software interacting with AD.
Measuring Success: KPIs for AD Security in XDR
Organizations should track several metrics to gauge the effectiveness of their AD security within XDR. These include mean time to detect AD compromises and directory change detection rate.
False positive rate for AD alerts and privilege escalation detection coverage are also important metrics to monitor.
Conclusion
Integrating Active Directory security with XDR has become essential for modern enterprises. This approach recognizes that identity systems are central to security architecture and frequently targeted by sophisticated attackers. Companies that build comprehensive AD security into their XDR strategy gain significant advantages in threat visibility, detection, and response.
Solutions like Fidelis Active Directory Intercept™ demonstrate how specialized AD protection can enhance XDR platforms through a multi-layered approach. By combining network traffic analysis, intelligent deception, and comprehensive AD monitoring, these solutions give security teams both the intelligence and time needed to respond effectively to threats.
Looking forward, we will see more sophisticated AI applications distinguishing between legitimate and malicious directory activities. There will be tighter integration with zero trust approaches and better cross-platform identity protection. Security teams should evaluate their XDR implementations against these trends to ensure their AD security approach matches the critical importance of this infrastructure.
Frequently Ask Questions
Is AD Security with XDR Relevant for Small and Medium Businesses?
While Fortune 1000 companies are obvious targets due to their complex AD infrastructures, businesses of all sizes face similar threats. Smaller organizations face a double challenge, they’re targeted frequently but typically operate with lean security teams and constrained budgets. Integrating AD security with XDR provides these companies with force-multiplying capabilities.
The automated detection and response features effectively extend security team capabilities, allowing them to identify and remediate sophisticated threats that previously only larger enterprises could defend against. Recent security trends indicate attackers increasingly view smaller businesses as soft targets for AD-focused breaches.
How Do Organizations Balance Robust AD Security with Seamless User Experience?
Finding the sweet spot between security and usability isn’t easy, but modern approaches offer several practical solutions. Risk-based authentication can intelligently challenge users only when their behavior deviates from established patterns, reducing unnecessary friction. For sensitive operations, step-up authentication proves more effective than constant verification, creating security boundaries without disrupting workflow. Just-in-time privilege management has emerged as a particularly effective strategy, providing administrative rights only when needed and automatically revoking them after use.
Properly tuned XDR platforms play a critical role by minimizing false positives—reducing both alert fatigue for security teams and unnecessary authentication challenges for legitimate users.
What Legal and Compliance Considerations Come with AD Monitoring in XDR?
The regulatory landscape significantly impacts how organizations implement AD monitoring within XDR solutions. Privacy regulations require transparent notification practices regarding employee monitoring. Security teams must implement data minimization principles, collecting only information essential for threat detection.
Establishing appropriate retention periods for security logs helps balance security needs with compliance requirements. Particularly in regulated industries, specific requirements for identity monitoring must be carefully integrated into the XDR implementation strategy. Leading organizations are addressing these challenges by creating cross-functional teams that include legal, compliance, and security stakeholders to develop AD monitoring frameworks that satisfy both security objectives and regulatory obligations.



