Cyber-attacks happen fast, leaving the victim with no time to react. It’s a matter of when – not if – an adversary will find a way into your systems. For this reason, you need to be prepared. Deception technology gives the gift of time during an in-progress attack. That time allows you to not only react, but also to study an attacker’s movements, determine the best plan to counter them, and finally, eradicate them before damage is done. And perhaps most importantly, to shut the door so they can’t get back in.
In this blog I will show you how, by using special types of decoys, Fidelis Deception® can distract and slow an attacker’s movements, even before the attacker is detected. Our decoys leverage various techniques to confuse cyber adversaries and lead them to false conclusions, when all they really want to do is discover assets on their victim’s network that they can monetize. You will see examples of TCP and Service Tarpits, special web servers, and endless file systems.
Deception Strategy: Tarpits
A tarpit is a server that purposefully delays incoming connections. The idea of a tarpit is to leverage certain network protocol settings to trap and delay the attacker’s movements.
When a cyber adversary interacts or communicates with a tarpit, they maintain connection, but the server makes their job more difficult, frustrating, and time consuming by slowing down the connection.
Fidelis Deception includes several types of tarpits, such as:
SSH Tarpit
According to SSH RFC (Request for Comments), both sides must exchange identification strings after establishing the TCP connection. The identification string is used to identify the SSH version between the client and the server.
The identification String has the following format:
“SSH-protoversion-softwareversion comments CR LF”
For example:
![]()
![]()
The Secure Shell (SSH) Protocol Request for Comments (RFC) lets the SSH server send additional data before sending the identification string. The RFC doesn’t mention how much data the server can send before the identification string. This feature allows the server to send an infinite amount of data before sending the identification string.
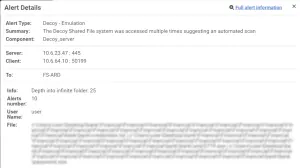
Fidelis Deception leverages this feature to hold the attacker at the point of connection. Attackers who use an automated method of scanning a network will wait indefinitely as the SSH decoy server sends a continuous stream of random data without ever sending the identification string. The system then alerts defenders to the attempted connection, along with salient client and server data for deeper investigation.
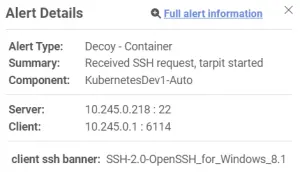
HTTP Tarpit
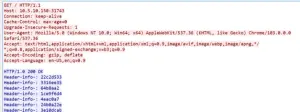
Hypertext Transfer Protocol (HTTP) allows the use of custom headers of any length. Our HTTP server decoy response for any HTTP request with ‘200 OK’ HTTP response. It then sends random custom headers every 10 seconds until the client closes the connection.
Using Chrome or Firefox, the browser will keep the connection open for an average of 8-10 minutes.
Following TCP stream, our server responds with random data, as you can see under ‘Header-info-’. The server traps the client as he waits for a connection attempt that never completes, while simultaneously alerting security operators to an in-progress attempted attack.
TCP Tarpit
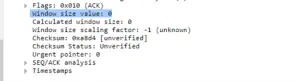
Transmission Control Protocol (TCP) is a streaming-based protocol that has many mechanisms to control the flow of messages between the client and the server. The “window size” field in the TCP header allows the server to indicate how much data it can buffer from the client.
After establishing connection with a TCP tarpit server through a three-way handshake, a client receives responses with zero window size to every subsequent request. The zero window value indicates that the server’s buffer is full, therefore, it cannot process any more data from the client. As a response to the window size response, the client will periodically send TCP “keep alive” messages to check if the window size has increased.
The TCP decoy server continues responding with zero window packets throughout the active session.
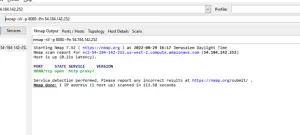
A client will keep the connection open and active depending on client configuration.
From our research, the Chrome browser keeps connections open for two minutes, Nmap for four minutes, and most other clients range between 12 and 24 minutes.
One benefit of the TCP tarpit is the fact that it is implemented on the TCP layer, removing the need for configuration of the application layer on the server side.
Deception Strategy: Infinite File System
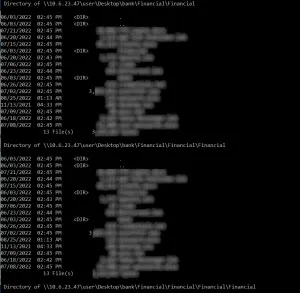
In addition to the delay tactics above that rely on slowing client/server connectivity, decoys can also occupy the attacker’s time and energy by dynamically manipulating the perceived cyber terrain. When using Server Message Block (SMB), File Transfer Protocol (FTP), or SSH, certain directories on Fidelis Deception decoys appear to have an infinite number of sub directories. An attacker using an automated tool endlessly browses these fake directories, causing a significant delay on the attacker’s side.
This type of decoy is extremely relevant in the case of ransomware where the attacker iterates the file system to encrypt the victim’s files. An infinite file system decoy provides defenders with valuable time to respond and stop the ransomware attack before the encryption process begins.
After configuring a decoy SMB server, the decoy leads to an endless number of folders. Therefore, executing a common directory traversal command, such as:
“dir /S \\<remote_decoy_server>”, leads to an endless loop.
Summary
Adding the combined special decoys mentioned above to your network will add a significant layer of security that lets you detect and respond to post-breach attacks faster. For every real server in your network, Fidelis Deception can deploy many decoys with identical protocols. This increases the probability that your cyber adversary will interact with decoys instead of your production assets. Once the adversary advances into your system and slows, you gain the time you need to respond, protect your assets, and close the door on future attacks.
Ready to change the game on your cyber adversaries?
One day, an attacker will evade your defenses. Fidelis Deception puts you back in control by helping you reclaim the advantage over your cyber adversaries. Contact us for more information today!




