What is Data Loss Prevention (DLP)?
Data Loss Prevention (DLP) is crucial to ensure that data is not lost, misused or accessed by unapproved individuals. Data loss prevention solutions monitors, detects and potentially blocks sensitive data exfiltration while the data is in use, in motion or at rest. It is largely driven by regulatory compliance as enterprises today must be able to demonstrate adequate care has been taken to avert the loss or theft of confidential and sensitive information on their networks.
How does DLP Security Work?
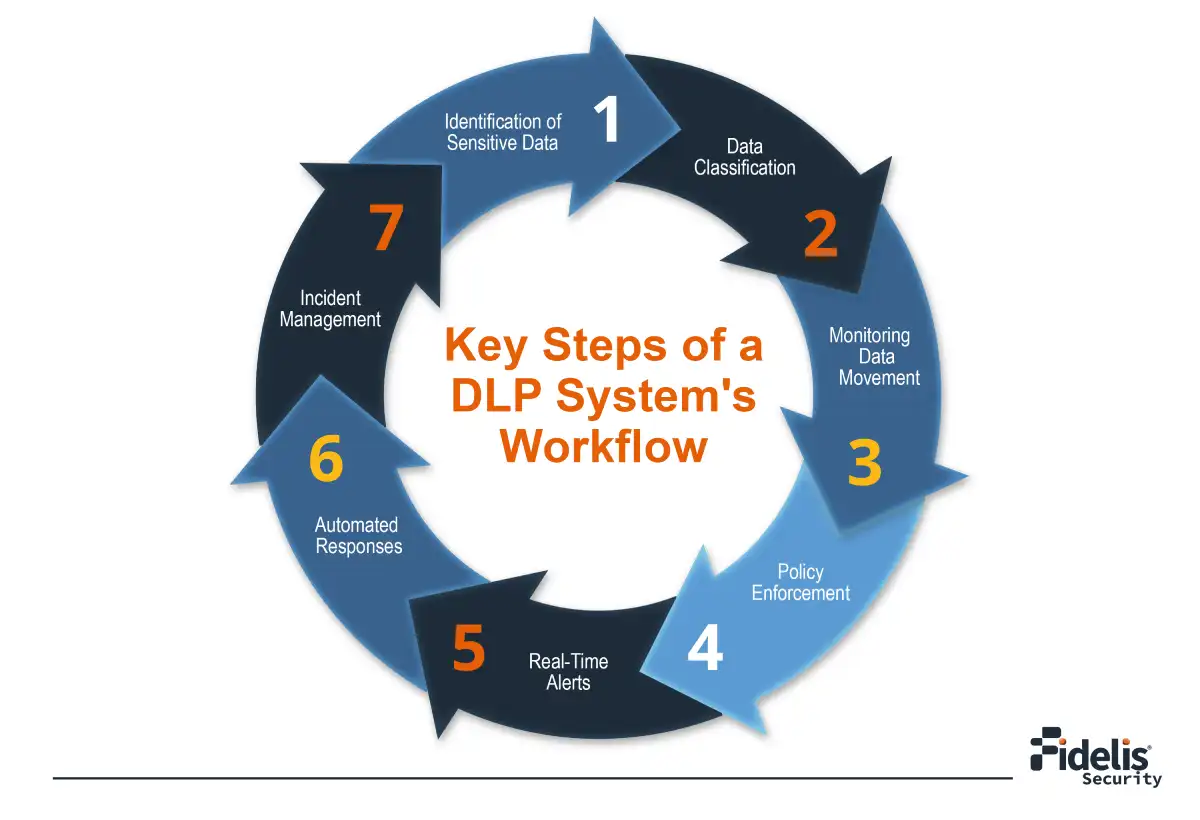
Data Loss Prevention (DLP) is a proactive approach used to protect sensitive information within an enterprise, irrespective of its location. The core steps involved in the working of DLP security solutions include:
Discovery & Categorization: DLP security identifies and categorizes your sensitive data. This can involve keywords, file types, or fingerprinting specific data patterns. Imagine it like a librarian meticulously sorting documents based on their confidentiality.
Detection: Once data is classified, DLP monitors data movement. This includes activities like copying files, emailing documents, or uploading data to cloud storage. This allows it to proactively watch out for data seekers.
Action through Monitoring and Response: DLP solutions continuously monitor data movement and user activities to detect policy violations in real time. When DLP detects a potential violation of your organization’s security policies, it takes pre-defined actions such as notifying security teams, blocking access, or encrypting data.
Why Data Loss Prevention (DLP) is Important?
The ability to detect and ultimately provide data leakage protection or theft aversion is core to cybersecurity defense – after all, that’s what most attackers are ultimately after. DLP solutions are deployed to combat the threat of data theft or leakage from these personas:
External Malicious Actor
This adversary is typically well-funded and very sophisticated. Security teams must have visibility into all activity, highlighted by data loss prevention solutions, anomalous and suspicious behavior detection, cyber threat hunting tools, and rapid and automated response capabilities.
Malicious Insider
This adversary is also well-funded and smart, but they have already been granted access to the network. For the malicious insider/external actor, it’s critical to have data loss detection and prevention policies that are enforced to prevent sensitive data from being stolen.
Uninformed Employee
This person inadvertently provides information to the malicious actor. Security tools must detect and respond to not only attacks that target employees, but risky also actions that employees perform to circumvent security policies and controls.
To dive deeper into effective data protection strategies and ensure your organization is prepared, check out this comprehensive guide on how to prevent data loss.
What are the Different Types of Data Loss Prevention Solutions?
DLP (Data Loss Prevention) solutions are not a one-size-fits-all. They come in different formats, each designed with specific aspects of data protection in mind. Let’s dive deeper and know about the different solutions.
Network DLP
Protecting Data in Motion: Network data loss prevention solutions concentrate on finding and stopping sensitive data from moving across a company’s network. This covers data sent through email, web apps, and other means of communication. These solutions do this by monitoring network traffic to detect and block data transfers that should not occur and bar critical information from leaving the firm without authorization.
Challenges in Network DLP: As more companies embrace digital transformation, they face the challenge of handling data in various network settings. Traditional data loss prevention systems often don’t work well in these changing environments.
Examples of Network DLP in Action: For instance, a Network DLP solution can spot and halt efforts to send sensitive client information via email outside the company, making sure that data protection rules are obeyed. Additionally, it can keep an eye on and block unauthorized uploads of files to websites outside the company, ensuring that important information stays safe inside the firm.
- Why is it crucial?
- Key Features
- Best Practices
- Adapting to Threats
Endpoint DLP
Securing Data on Devices: Endpoint DLP solutions protect sensitive information on endpoint devices like laptops, desktop machines, and mobile phones. These solutions monitor data in use; the employees shall not be able to duplicate, share, or move critical information without getting warned. Endpoint DLP is very important for companies that have their employees work remotely or that allow employees to use their own devices at work.
Challenges in Endpoint DLP: As people work remotely and use personal devices, keeping information safe on all kinds of devices is getting harder. Endpoint DLP helps solve this problem by always monitoring and making sure data safety rules are followed, so important information is kept safe on any device, whether it’s owned by the company or an individual.
Examples of Endpoint DLP in Action: For example, an Endpoint DLP solution prevents an employee from transferring sensitive files to a USB drive or sending crucial documents via unapproved apps. It also protects data that is accessed using a personal device, lowering the risk of data breaches in scenarios where people work from home or use a combination of home and office environments.
Storage DLP
Protecting Data at Rest: Data Loss Prevention (DLP) for storage systems is made to protect important information kept in places like databases and file servers. These systems keep an eye on data that’s not being used, making sure that people who shouldn’t see it can’t get to it by using methods like encryption and other safety steps. Storage DLP is important for companies with lots of important information, like customer details or money stuff, giving them strong protection even when the data isn’t being used now.
Challenges in Storage DLP: As companies collect more data, keeping it safe in different storage places gets harder. Traditional ways might not be enough to stop people from getting in without permission or to prevent data from being stolen. Storage DLP helps with these problems by using constant checks, making data unreadable without the right key, and controlling who can get to the data. This makes sure that important data stays safe no matter where it’s stored.
Examples of Storage DLP in Action: For instance, a Data Loss Prevention tool for storage can automatically encrypt data in a database, stopping unauthorized access. It can also check access records for unusual behavior, like trying to get sensitive files without the right permissions, thus keeping important data safe from both internal and external risks.
Cloud DLP
Securing Data in the Cloud: Cloud Data Loss Prevention (DLP) solutions are made to protect sensitive information that is kept and used in cloud environments. As more businesses use cloud services because they are flexible and can grow, keeping data safe in these places is very important. Cloud DLP systems watch over and control data on various cloud platforms like AWS, Azure, and Google Cloud. They make sure that data security rules are followed and stop data from being shared or taken without permission.
Cloud Adoption Challenges: The growth of cloud computing has brought up new challenges for keeping data safe. Old DLP systems have trouble giving the right oversight and management in cloud settings, which can be complicated and always changing. Cloud DLP tackles these problems by offering constant monitoring, data locking, and rule application for setups that use both different clouds and a mix of clouds and local systems. This makes sure that important data stays safe, no matter where it’s kept.
Examples of Cloud DLP in Action: For example, a Cloud DLP solution can automatically find and hide important information, like credit card numbers or social security numbers, before it is shared in online tools for working together, such as Google Drive or Microsoft 365 apps like OneDrive. Also, Cloud DLP can make sure that only people who are allowed can see or change important information in the cloud.
Types of Threats DLP Solutions can Defend
By proactively identifying and controlling data flow, DLP helps safeguard against the following key threats:
External Attacks: DLP protects against external threats from cybercriminals seeking to infiltrate organizational networks and steal sensitive data. This includes a range of threats like ransomware, phishing and more.
Intellectual Property Theft: Data Loss Prevention solutions help safeguard intellectual property (IP) and proprietary information from theft or unauthorized disclosure. These assets are often valuable to competitors and adversaries.
Compliance Violations: Regulations such as GDPR, HIPAA, PCI DSS, and others mandate the protection of crucial personal information. DLP security solutions are required to maintain compliance and regulatory standards.
By implementing robust Data Loss Prevention solutions and policies, organizations can strengthen their security posture and safeguard their most valuable assets from unauthorized access or disclosure.
What are the Key Aspects of a Network Data Loss Prevention (DLP) Solution?
There are three critical components of an overall network data loss prevention solution:
- Detect and block sensitive data in motion from leaving through network traffic.
- Monitor data in use on endpoints and block unauthorized attempts to steal data.
- Monitor all data at rest within a storage location where if accessed or manipulated to exfiltrate data, a blocking action should occur.
Recommended Reading
DLP Best Practices – Checklist
- Create a strong plan for sorting and organizing data.
- Use tools that automatically label data to help find it quickly.
- Conduct training for employees to teach them about keeping data safe.
- To help employees learn more about recognizing scams, create fake phishing attempts.
- Control who can access important data.
- Use multi-factor authentication for extra protection.
- Establish ongoing data tracking and alert mechanisms.
- Perform routine checks to evaluate how well data protection methods are working.
- Make a detailed plan for what to do if data gets into the wrong hands.
- Carefully examine data breaches to find out why they happened and take steps to fix the problems.
Fidelis Network Data Loss Prevention Solution
Fidelis Security’s Patented Deep Session Inspection® technology gives you the ability to examine potential threats at a very detailed level and terminate any sessions that violate policies, while additionally allowing an administrator to view the details about who sent data, to whom and what type of data was sent.
Data security with Fidelis prevents network data loss for your enterprise by:
- Extracting metadata and monitoring 300+ different attributes: The Fidelis Network DLP solution keeps an eye on all the data moving through a network, looking at details and checking more than 300 different features. This detailed approach helps companies understand how their data is being used and spot possible dangers before they become bigger problems.
- Providing increased data visibility: It provides complete visibility over data no matter where it is stored. That visibility gives insight into what is being accessed, and it is key to identifying unauthorized attempts to access the data. It also helps organizations comply with data protection regulations.
- Investigating how and why your data moves: The Fidelis Network DLP system provides a detailed analysis of data mobility, allowing businesses to understand how and to what extent their data is being accessed. Such information is immensely helpful in identifying patterns of behavior that could indicate a potential threat.
- Preventing data theft or unauthorized sharing: The Fidelis DLP technology can discover and deter attempts to steal or disclose sensitive data without authorization by observing all data movement in real-time. This proactive technology allows organizations to prevent data breaches before they happen.
- Safeguarding IP and business reputation: Both intellectual property and business reputation are valuable assets that should be protected. The Fidelis DLP solution secures these assets and enables firms to maintain a competitive advantage and mitigate the negative repercussions of a data breach.
- Ensuring compliance: With ever-increasing stringent data protection requirements, firms place a higher priority on compliance. The Fidelis DLP solution enables firms to comply with regulatory requirements by providing a comprehensive data protection approach and ensuring that all data handling processes are compliant with industry standards.
Conclusion
Data Loss Prevention (DLP) is a key part of a strong cybersecurity plan. By understanding different DLP tools and following good practices, companies can greatly lower the chance of data leaks and keep important information safe. Fidelis Security’s Network Data Loss Prevention Solution has advanced features that help companies see, manage, and protect their data, which is important in our world where threats are getting more complicated.
Frequently Asked Questions
How does DLP help in assuring compliance with data protection regulations?
DLP solutions make organizations comply with regulations like GDPR, HIPAA, and PCI DSS. It makes them handle data as per legal requirements, not allowing any unauthorized access, and auditing trials.
What is the difference between Data Loss Prevention and Data Breach Detection?
DLP solution’s focus is to prevent data loss and theft by making organizations comply with security policies, while data breach detection looks into whether and when the breach has occurred. Thus, DLP is proactive whereas breach detection is reactive.
Is it possible to integrate DLP solutions with cloud services?
Yes, Cloud DLP solutions were designed to integrate with cloud platforms such as AWS, Azure, and Google Cloud to secure data when maintained and processed in the cloud.




