Defining Network Data Loss Prevention (DLP)
Network Data Loss Prevention (DLP) software monitors, detects, and potentially blocks sensitive data exfiltration while the data is in motion. Network DLP prevents the transfer of critical information outside of a corporate network and is mandated as a compliance requirement in some regulated industries to ensure that measures taken by organizations are able to demonstrate due care in avoiding loss or theft of confidential/sensitive data.
How Does Network DLP Work?
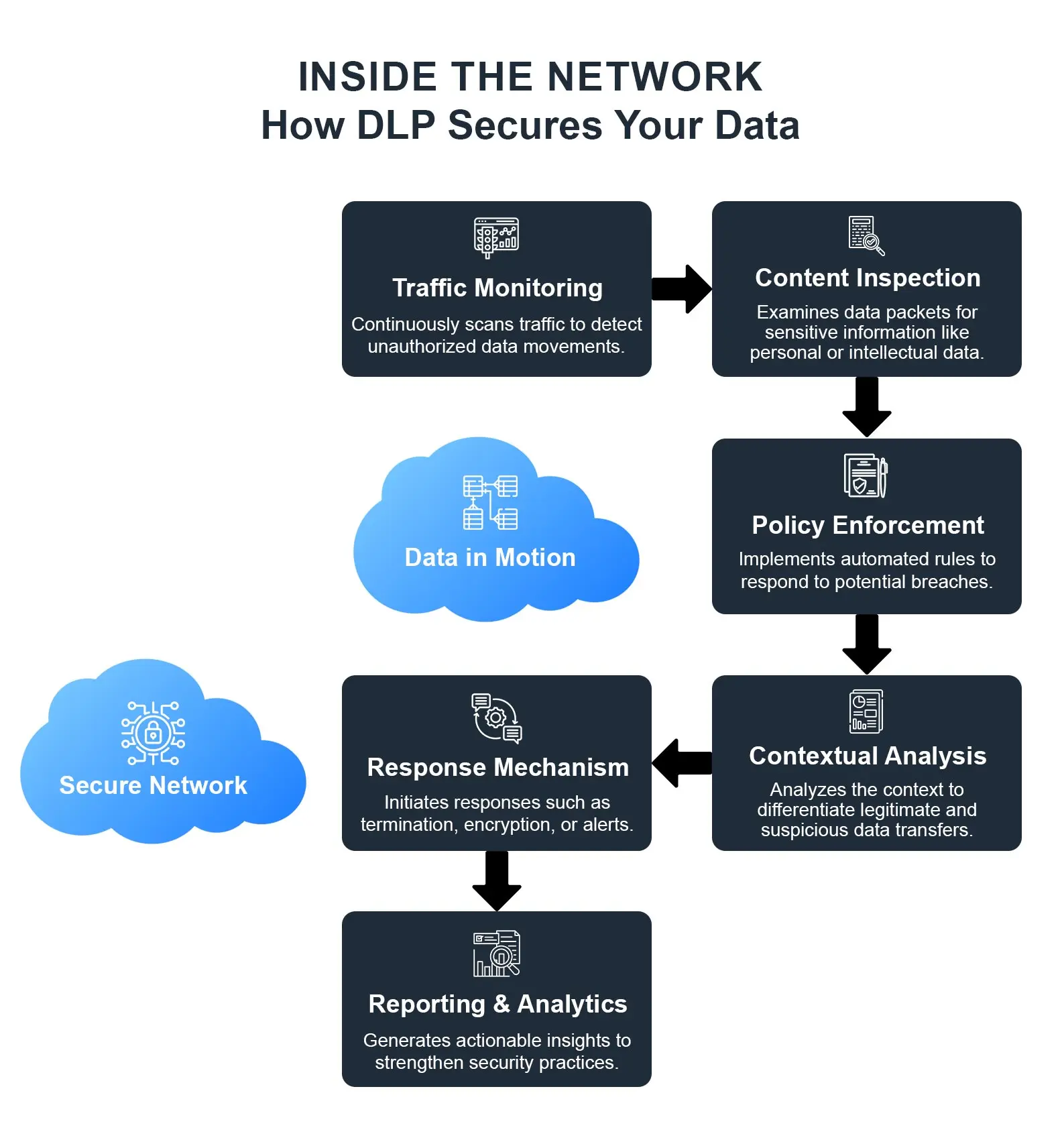
Network DLP solutions are designed to monitor, detect, and prevent unauthorized data transfers across a network. It acts like a digital security scanner, but with more advanced capabilities. Here’s a breakdown of its functionalities:
- Traffic Monitoring: Constantly scans the traffic, to make it possible to identify data movements. It is, in fact, one important aspect of network security with DLP. It can monitor data packets crossing the network and identify patterns that could suggest unauthorized data transfers.
- Content Inspection: Involves inspecting data packets for sensitive data such as social security numbers, credit card information, or intellectual property. Content inspection can be applied to any form of data: email, files, and attachments.
- Policy Enforcement: It allows policies to be set up so that they may automatically respond to potential data breaches, constraining data transfers, encrypting data, or sending alerts for further follow-up investigation. These concede that any activity in violation of preset regulations is alerted immediately and taken up by the hand.
- Contextual Analysis: Analyze the contexts in which data is moved with the aim of helping establish legitimacy. For example, sending a document with customer information to one of your trusted partners may be a normal and allowed move but will raise an alert if such a document is moved to a personal address. This helps in differentiating legitimate data transfers from those that are suspicious.
- Response Mechanism: Offers mechanisms for responding to policy violations, terminating transfers, encryption, and sending alerts. This, in turn, ensures that there is an immediate course of action to be adopted to stop the breach of data.
- Reporting and Analytics: Develops meaningful reports that are used in the analysis of data traffic patterns and identifies potential security threats, in the process beefing up data loss prevention monitoring in general. These reports help in providing insights into how data really flows in an organization, fine-tuning the security policies and practices.
Why is Network Data Loss Prevention (DLP) Important?
Network DLP capabilities are important in compliance support, intellectual property protection, and enhancement of security awareness among employees. Network DLP provides one with visibility and controls that detect and prevent accidental data loss and stop the malicious insider who intends to exfiltrate data from the corporate network.
Organizations use network DLP capabilities to support the following use cases:
- Support regulatory compliance efforts around data protection where network DLP is used to detect and prevent compliance policy violations around data movement – and ultimately preventing sensitive data from being transferred out from the corporate network.
- Protect intellectual property from being exfiltrated from the corporate network.
- Visibility of sensitive data and augment employee security awareness. Unintentional policy violations can result in a notification to the user with an explanation to help train proper behavior.
Fidelis Network® Data Loss Prevention amplifies these capabilities by offering deep session inspection and actionable insights into data movements. Its technology ensures enhanced protection and compliance for organizations.
Don’t Let Sensitive Data Slip Through: Secure Your Network Now!
The ultimate guide to choosing the right Network DLP solution for 2024. What’s Inside the Guide?
- Decision-Making Insights
- RFI Checklist
- Implementation Best Practices
What are the Key Aspects of a Network Data Loss Prevention (DLP) Solution?
While detection is clearly an important role in network DLP, being able to prevent sensitive data from leaving the network is the ultimate goal.
- Conduct session-level (not packet-level) inspection of network traffic across all 65,535 network ports. Given most human-readable data in an enterprise is not in plain text formats, visibility requires knowledge beyond an individual packet for network DLP decisions.
- Provide visibility into the protocols, channels, and applications in use on the network. Network data loss prevention solutions need to understand a wide variety of network traffic to determine how people are communicating and extract information for analysis.
- Ability to extract enterprise human-readable content and related metadata contained within sessions as well as any attachments and compressed files for analysis.
- Provide multiple sophisticated content analysis technologies to detect sensitive and/or protected information for accurate content recognition.
- Provide a policy engine to implement rules to determine network sessions that violate policy. Policy-based enforcement maps rules to an organization’s content disclosure or network use policies.

Benefits of Network DLP
Here are the benefits of a network DLP solution:
- Comprehensive Data Protection: This feature ensures that the sensitive data is protected from unauthorized access and exfiltration.
- Regulatory Compliance: Real-time compliance with PCI DSS and other related regulations is achieved by the surveillance of data flows.
- Improved Security Posture: It detects and mitigates potential threats.
- Employee awareness: Regularly notify and clarify policies which helps in increasing employee awareness on best practice to handle data.
- Intellectual Property Protection: Prevents unauthorized access and distribution of intellectual property.
- Real-time Threat Detection: Detects suspicious activities happening in real-time and takes immediate actions.
- Policy Enforcement: Automates the enforcement of data protection policies, minimizing human error.
- Cost Savings: No data breaches mean no costs incurred from losing data or lawsuits.
- Adaptable: Keeps up with changing data landscapes—including cloud and remote work environments.
- Integration with Other Security Tools: Enhances security strategy through integration with other tools.
- Fewer Insider Threats: Identifies and limits insider threats by monitoring all activities of employees.
- Data Classification: Categorizes the data with respect to sensitivity and applies protection measures accordingly.
- Incident Response Support: Provides activity logs and reports for incident response support, if an incident has occurred.
- User Behavior Analytics: Detects anomalies and potential security incidents through behavior analysis.
What are the key threats that Network DLP can Defend?
Network DLP fortifies your cyber territory against a variety of threats that could result in the loss of confidential data. Here are some of the key areas it helps protect:
-
Emerging Threat Landscapes
In the evolving digital ecosystem, network DLP is more important than ever. As more people are working from home and are opting for cloud-based services, they are facing more advanced cyber threats. Companies need strong data lose prevention measures to protect their data from being lost or stolen over networks.
-
Malicious Insider Threats
Sensitive information may be stolen or leaked by resentful workers or those acting maliciously. Data Loss Prevention Monitoring staff behavior and identifying questionable efforts to transmit sensitive data are two ways that network DLP might be helpful.
-
Cloud Misconfigurations
To prevent sensitive data from being unintentionally exposed due to misconfigurations, network based DLP can assist by monitoring data flows to and from cloud services.
-
External Intrusion
Cybercriminals and hackers frequently target networks to steal sensitive data. By identifying efforts to exfiltrate data via malware, phishing emails, or illegal access points, network data loss prevention (DLP) can be an essential line of defense.
-
Advanced Persistent Threats (APTs)
Modern network DLP solutions are now equipped to detect and mitigate Advanced Persistent Threats. These sophisticated, long-term cyberattack campaigns often involve multiple stages of infiltration and data exfiltration. Network DLP can:
- Detect unusual data transfer patterns
- Monitor lateral movement within networks
- Identify potential command and control (C2) communication
- Prevent staged data aggregation before exfiltration
-
Supply Chain and Third-Party Risk
With increasing interconnectedness, network DLP now plays a crucial role in managing risks associated with supply chain and third-party vendor interactions:
- Monitor data exchanges with external partners
- Enforce strict data sharing policies
- Prevent unauthorized data transfers through vendor networks
- Maintain compliance across complex ecosystem interactions
Evolution of Network DLP: Implementation Strategies for 2025
As cyber threats become increasingly sophisticated, network Data Loss Prevention (DLP) solutions must continuously adapt and innovate. The landscape of data protection is rapidly changing, driven by technological advancements and emerging security challenges. Organizations are now looking beyond traditional security measures to implement more dynamic, intelligent approaches to network data protection.
Embracing Zero Trust Architecture
The traditional perimeter-based security model has become obsolete in today’s distributed computing environments. Network DLP solutions are now integrating Zero Trust architecture, a security paradigm that fundamentally transforms how organizations approach data protection:
- Continuous Verification: Unlike legacy systems that trust users once authenticated, Zero Trust mandates continuous verification of every data access request. This means each interaction is scrutinized regardless of its origin or previous trust status.
- Micro-Segmentation: Network resources are now divided into highly granular segments, limiting potential breach impacts. This approach ensures that even if one network segment is compromised, the entire network remains protected.
- Context-Aware Policy Enforcement: Modern network DLP goes beyond binary allow/deny decisions. Policies are now dynamically adjusted based on multiple factors:
- User identity and role
- Device health and security posture
- Data sensitivity classifications
- Real-time contextual information
AI and Machine Learning: Transforming Network DLP
Artificial Intelligence and Machine Learning are revolutionizing network data loss prevention, moving from reactive to predictive security models:
- Predictive Threat Detection: AI algorithms can now analyze historical data patterns to anticipate potential breach scenarios before they occur, offering a proactive approach to data security.
- Intelligent Policy Development: Machine learning enables the creation of more nuanced, context-aware policies that adapt to evolving organizational needs and threat landscapes.
- False Positive Reduction: Advanced AI techniques help distinguish between genuine security threats and benign activities, significantly reducing alert fatigue for security teams.
- Automated Threat Response: Instead of merely detecting threats, modern network DLP solutions can now automatically respond to potential data exfiltration attempts, implementing predefined mitigation strategies in milliseconds.
Frequently Ask Questions
What industries benefit most from Network DLP solutions?
Network DLPs benefit the most in highly regulated industries, like finance, healthcare, and the government sector.
How does Network DLP handle encrypted traffic?
Network DLP solutions often have decryption capabilities for inspecting encrypted traffic to assure sensitive data is not hiding within encrypted communications.
What is the difference between Network DLP and Endpoint DLP?
Network DLP monitors and safeguards data in motion across a network, whereas Endpoint DLP performs the same functions for data at rest or in use on specific devices.
Can Network DLP solutions be customized for specific organizational needs?
Yes, Network DLP solutions can be configured to feature policies and rules customized to suit any data security requirement of an organization and its business processes.
How does Network DLP improve employee security awareness?
Network DLP improves security awareness among employees by notifying and describing accidental policy violations, thus educating employees on how to handle the data properly.
About Fidelis Network Data Loss Prevention Solution
Fidelis Security’s Patented Deep Session Inspection technology gives you the ability to investigate threats and stop sessions that violate policies with details about who is sending and receiving data and what type of data is being sent. DLP security with Fidelis prevents data loss for your enterprise by:
- Extracting metadata and monitoring 300+ different attributes.
- Providing increased data visibility
- Investigating how and why your data moves
- Preventing data theft or unauthorized sharing
- Safeguarding IP and business reputation
- Ensuring compliance



