Discover the Top 5 XDR Use Cases for Today’s Cyber Threat Landscape
Discover the best defense against ransomware with EDR and NDR technologies. Learn
Is your XDR solution truly comprehensive? Find Out Now!
Ransomware has evolved over the years and is now targeting organizations of all sizes with both file encryption and information exfiltration. In 2024, 59% of organizations experienced at least one ransomware attack, costing them billions in losses from damage, downtime, and data loss.
Though firewalls and antimalware programs have their merits, they alone cannot provide protection from both data encryption and theft. This is why Data Loss Prevention (DLP) solutions are essential in helping organizations combat ransomware.
In 2024, ransomware attacks have become frequent and serious, with the typical ransom demand of more than $1million, while the average recovery cost is over $4 million due to the downtime, investigation, and recovery efforts. Also, attackers usually dwell in a network for several months before being found out. The evolving tactics of ransomware—particularly encrypting and stealing data—make it essential for organizations to consider advanced data protection tools, like DLP, to avoid ransomware attacks.
| Ransomware Impact (2024) | Statistics |
|---|---|
| Average Ransom Demand | Over $1 million |
| Average Recovery Cost | Exceeds $4 million |
| Average Dwell Time | Several months |
| Ransomware-related Data Breaches | 59% so far |
DLP solutions are designed to monitor, protect, and limit the movement of data. This makes it difficult for ransomware to access or steal information.
When it comes to defending against ransomware, Fidelis Network® DLP takes this protection a step further by integrating network and endpoint visibility with advanced content inspection, ensuring sensitive data remains secure across all 65,535 network ports.
This layered approach combines data visibility, behavior analyses, and policy enforcement to reduce the impact of an attack. Here’s how DLP could assist organizations prevent and mitigate the effects of ransomware:
DLP starts by categorizing data based on its sensitivity. This labeling helps the DLP system recognize important data and apply ransomware-specific policies to protect it against unauthorized access.
DLP solutions are equipped with UBA which monitors user behavior to find unusual patterns. This helps security personnel notice suspicious activities like accessing a large number of files all of a sudden or trying to transfer the data.
DLP enforces policies that control who can access data based on their job role and need-to-know basis. These rules can stop people from moving data outside the company, downloading files, or modifying them—typical actions ransomware relies on.
Many DLP solutions also monitor network traffic, spotting potential indicators of ransomware communication or data exfiltration attempts. This feature complements endpoint security, making the overall solution better at identifying ransomware by noticing its network behavior and warning security teams about suspicious activity.
Even with vigorous security measures, ransomware can sometimes go undetected. In such situations, DLP’s data recovery capabilities are crucial. Here’s how DLP solutions help with recovering from ransomware and staying resilient:
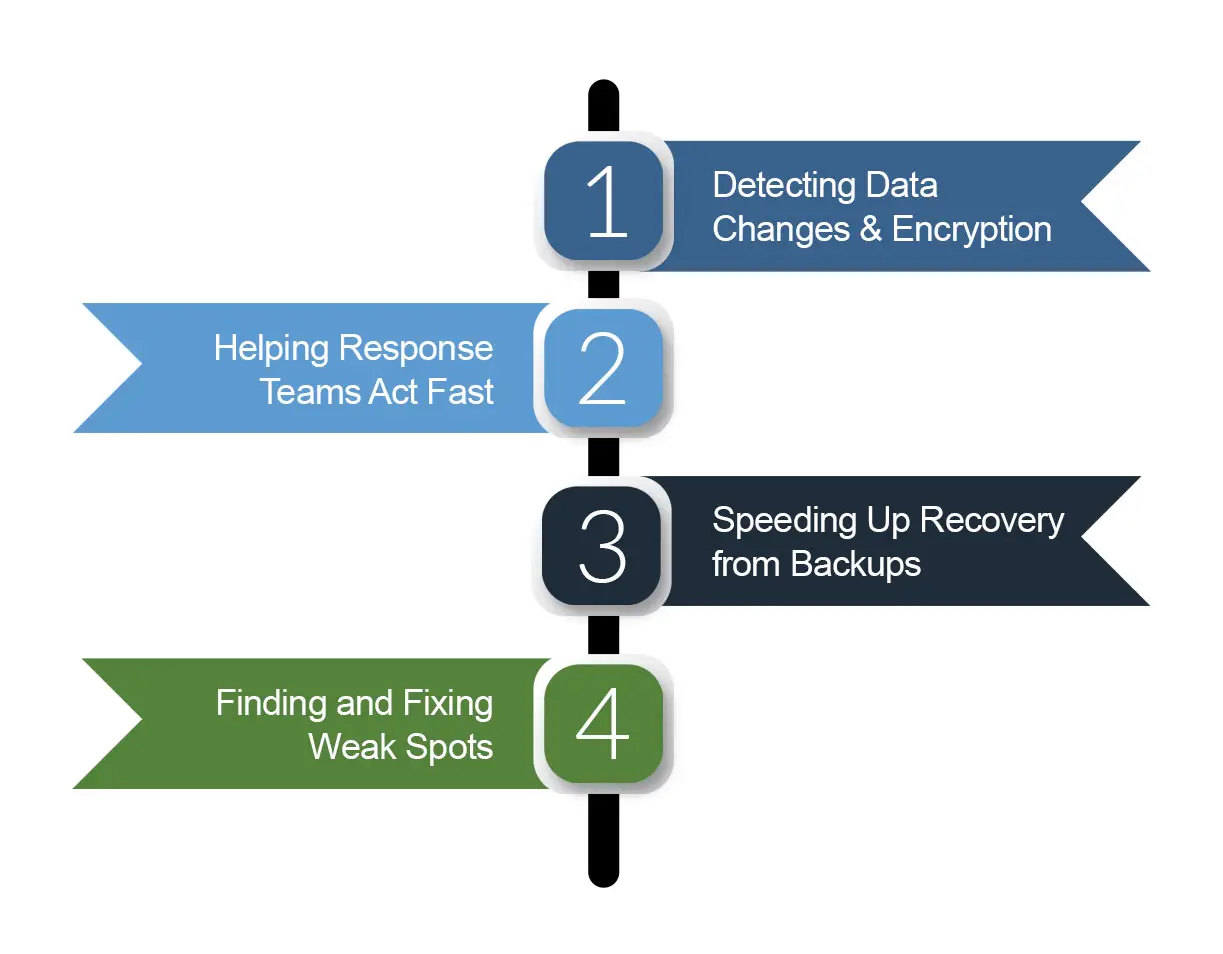
DLP systems are designed to identify large-scale data encryption, which is common in ransomware attacks. When these activities are detected, alerts are sent out, enabling IT teams to quarantine affected systems. This stops ransomware from spreading throughout the network.
DLP maintains logs of all data transfers and modifications, offering valuable insights for incident response. By analyzing these logs, the security team can quickly identify affected data, making sure that ransomware data recovery only targets clean, unaltered data.
Data backups are crucial for preventing ransomware. However, backups may only shield your data to a certain extent; they cannot stop data theft. DLP ensures that only secure, unaltered data is recovered, which speeds up the recovery process and improves efficiency.
DLP solutions are able to detect vulnerabilities in data management policies by analyzing ransomware attacks. Businesses can use this intelligence to eradicate ransomware threats, by updating their policies and strengthening their security systems.
Gain insights into solutions blending detection, deception, and defense against ransomware.
For comprehensive ransomware data protection, organizations need a multi-layered DLP approach:
DLP can segment data across different zones, restricting access based on sensitivity levels. This way, if ransomware affects one segment, it doesn’t necessarily have access to others.
Data segmentation helps prevent ransomware from spreading across the network, limiting its impact.
Automation enables DLP solutions to enforce security policies in real-time. Automated DLP policies can block certain file transfers, downloads, or unusual activities without waiting for human intervention, adding an immediate response layer against ransomware.
By limiting data access to users who need it, DLP minimizes the risk of ransomware impacting highly sensitive data. Granular access controls are essential to stop ransomware from gaining unauthorized entry.
Ransomware usually gets into systems via phishing emails and social engineering. DLP solutions can help by blocking specific risky actions or providing in-app reminders, which lowers the chance of a ransomware attack.
Although DLP plays an important role, it works best when integrated with other robust security solutions. To protect against ransomware, you need a combination of solutions working together to give you strong, multi-layered security.
| Integration | Description |
|---|---|
| DLP and Zero Trust | The Zero Trust model uses strong access rules, which work well with DLP's data security methods. By verifying users and devices each time they try to access something, Zero Trust helps stop ransomware from spreading, even if a device is hacked. Fidelis Network® DLP supports such integration seamlessly, giving organizations better control over network data flows. |
| DLP and EDR | DLP is about safeguarding data, whereas EDR is about identifying and responding to endpoint threats. When brought together, they offer robust protection against ransomware by monitoring endpoint activities to detect malicious activity and ensuring sensitive data remains secure. Fidelis Network®, paired with Fidelis Endpoint®, provides a coordinated defense by linking network-level DLP with endpoint insights. |
| DLP and SIEM (Security Information and Event Management) | A SIEM system provides a centralized view at security events, helping to identify patterns and possible threats. When combined with DLP, SIEM can detect ransomware earlier, prevent it from spreading, and allow for a complete response to threats. Fidelis Network® DLP offers extensive support for SIEM integration, giving a full view of network events and enriching security data with contextual insights. |
Get the essential insights on how Fidelis Network® DLP strengthens your ransomware defenses with
In today’s cyber battlefield, relying on old-school defenses just doesn’t cut it. Data Loss Prevention solutions are important as they provide a layer of protection by:
By integrating DLP with other security solutions like EDR, SIEM, etc., companies can better protect their data from ransomware. In addition to that,
For organizations serious about keeping their data safe and building a strong defense, deploying DLP is a smart decision. With features like,
DLP lets you fight ransomware head-on and maintain control of their most important digital assets.
Fidelis Network® DLP improves this resilience by using deep data visibility, smart automation, and seamless integration with other security tools. Its advanced features not only find and stop ransomware threats but also make sure your important assets stay safe and can be recovered, making your organization’s overall security stronger
Yes, no solution is completely fail-safe, but DLP greatly lowers the risk by monitoring data movement and preventing unauthorized access. When combined with other security measures, DLP enhances the organization’s protection against ransomware.
You should focus on sensitive information such as,
These are frequently targeted in ransomware attacks.
DLP complements tools like SIEM, EDR, and Zero Trust to create a layered defense. This combination enables early threat detection, data protection, and a strong recovery plan.
Sarika, a cybersecurity enthusiast, contributes insightful articles to Fidelis Security, guiding readers through the complexities of digital security with clarity and passion. Beyond her writing, she actively engages in the cybersecurity community, staying informed about emerging trends and technologies to empower individuals and organizations in safeguarding their digital assets.
See Fidelis in action. Learn how our fast and scalable platforms provide full visibility, deep insights, and rapid response to help security teams across the World protect, detect, respond, and neutralize advanced cyber adversaries.