Discover the Top 5 XDR Use Cases for Today’s Cyber Threat Landscape
Discover the power of Extended Detection and Response (XDR) in modern cybersecurity.
Is your XDR solution truly comprehensive? Find Out Now!
When threats emerge, the Fidelis Security Threat Research team (TRT) is ready. Each month, the Threat Intelligence Summary examines the latest threats and trends so you can stay resilient against cyber adversaries.
In May 2023, we saw significant ransomware activity from several different groups, including a shift in tactics for BianLian, Google announced the launch of new consumer security features, and new vulnerabilities, exploits, and attacks targeted both government and private organizations worldwide. We also tracked multiple highly significant and emerging vulnerabilities and highly seismic malware activity in our sandbox environment.
Read the May 2023 Threat Intelligence Summary
The Fidelis Security TRT’s top-ten vulnerability list for May begins with a critical remote code execution vulnerability within the Windows Network File System. We also saw several critical and high impact vulnerabilities against additional Microsoft operation systems, products, and middle-ware layer applications.
We also include the base scores for each of our top vulnerabilities. The base score is a complex calculation that weighs several factors, including exploitability (attack complexity, scope, privileges required, etc.), impact metrics, CVE maturity, and more. The value, from 0 to 10, represents the potential severity of the threat. The higher the number, the more critical the CVE.
These base scores serve as one reliable indicator of threat criticality. However, there are many factors that go into our top ten inclusion. The list presented in our report represents what we have observed as the month’s most credible threats to any organization using unpatched systems or software. Whether a vulnerability is newly discovered, has proofs of concept available, or is being actively exploited, regular patch management is imperative for securing your organization.

Fidelis Security tracks the most prevalent malware threats to keep our detection feeds up to date and our clients secure. In May 2023, Fidelis detected and defended against more than seventy thousand high-severity malware threats. We note this month how some industries can have multiple (and even hundreds) of different types of malware attacks against them that might go unnoticed due to a single malware signature dominating the detection feeds. We discuss how this scenario can benefit the attackers, and what non-IT-focused industries can do to keep themselves protected against the variety of threats against them.
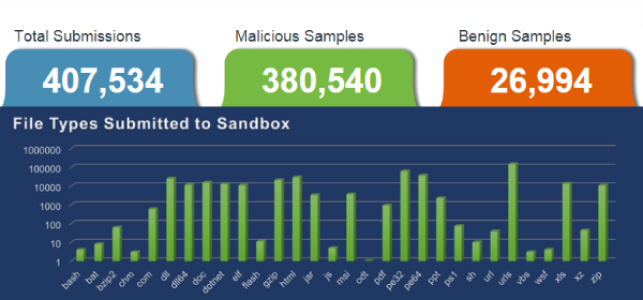
For the May report, we also continued studying sandbox submission metrics for malware samples observed across our customer base. Read the report to see how we curate and evaluate these samples. You’ll also get a deep dive into some of the hardest hit industries over the past month, and details regarding the most prevalent malware threats indicated by open-source reporting.
Each month, our report contains the top five active phishing sites observed in the wild. While the best defense against phishing is user vigilance, security teams can rely on emerging data like this to help bolster defenses.
See the top phishing domains list >
The Threat Research team at Fidelis Security researches and analyzes the latest threats and issues. The intelligence we gather from multiple open-source and proprietary sources about our cyber adversaries’ tactics, techniques, and procedures (TTPs) is fed directly into our platforms, products, and services to help our customers detect, neutralize, and eliminate threats before they can harm production systems.
Visit our cyber threat intelligence research page to read the complete May 2023 Threat Intelligence Summary, along with information on critical threats and resources to help you better prepare for the next attack.
Jon Belanger is a seasoned Sr. Analyst in Threat Research with a passion for unraveling the intricate world of cybersecurity. Over the years, Jon has honed his skills through hands-on experience and a commitment to staying ahead of the ever-evolving threat landscape.
See Fidelis in action. Learn how our fast and scalable platforms provide full visibility, deep insights, and rapid response to help security teams across the World protect, detect, respond, and neutralize advanced cyber adversaries.