When threats emerge, the Fidelis Security Threat Research team (TRT) is ready. Each month, the Threat Intelligence Summary examines the latest threats and trends so you can stay resilient against cyber adversaries.
In June 2023, we saw ongoing instances of non-compliance with CISA Directives related to MOVEit vulnerabilities, indicating persistent patching issues that pose significant risks to non-compliant organizations. Additionally, we’ve identified Russian state-sponsored threat actors leveraging PowerShell USB malware to deploy backdoors. Another concerning development is the emergence of Akira Ransomware targeting ESXi servers. Furthermore, several new high and critical vulnerabilities have surfaced, including one affecting MOVEit Transfer.
Read the June 2023 Threat Intelligence Summary
Top Emerging Vulnerabilities
The Fidelis Security Threat Research Team has identified several critical vulnerabilities that demand immediate attention. Notably, the MOVEit vulnerability has been actively exploited in the wild throughout May and June, posing significant risks to systems. Additionally, vulnerabilities in WordPress Social Login and Register, Microsoft SharePoint, and Windows Pragmatic General Multicast (PGM) have also been classified as high-priority due to their potential for exploitation.
We also include the base scores for each of our top vulnerabilities. The base score is a complex calculation that weighs several factors, including exploitability (attack complexity, scope, privileges required, etc.), impact metrics, CVE maturity, and more. The value, from 0 to 10, represents the potential severity of the threat. The higher the number, the more critical the CVE.
These base scores serve as one reliable indicator of threat criticality. However, there are many factors that go into our top vulnerability inclusion. The list presented in our report represents what we have observed as the month’s most credible threats to any organization using unpatched systems or software. Whether a vulnerability is newly discovered, has proofs of concept available, or is being actively exploited, regular patch management is imperative for securing your organization.

Malware Attacks by Industry
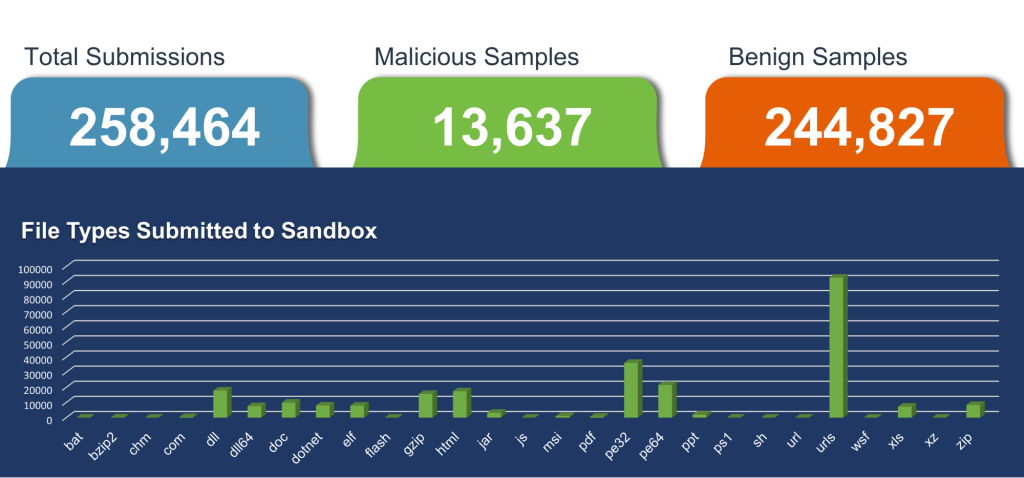
Fidelis Security tracks the most prevalent malware threats to keep our detection feeds up to date and our clients secure. In June 2023, Fidelis Security detected and defended against more than seventy thousand high-severity malware threats. Certain industries, identified as prime targets, faced escalated risks.
For the June report, we also continued studying sandbox submission metrics for malware samples observed across our customer base. Read the report to see how we curate and evaluate these samples. You’ll also get a deep dive into some of the hardest hit industries over the past month, and details regarding the most prevalent malware threats indicated by open-source reporting.
Top Phishing Domains
Each month, our report contains the top five active phishing sites observed in the wild. While the best defense against phishing is user vigilance, security teams can rely on emerging data like this to help bolster defenses.
See the top phishing domains list >
About the Fidelis security Threat Research Team
The Threat Research team at Fidelis security researches and analyzes the latest threats and issues. The intelligence we gather from multiple open-source and proprietary sources about our cyber adversaries’ tactics, techniques, and procedures (TTPs) is fed directly into our platforms, products, and services to help our customers detect, neutralize, and eliminate threats before they can harm production systems.
Visit the Fidelis security Threat Research page to read the complete June 2023 Threat Intelligence Summary, along with information on critical threats and resources to help you better prepare for the next attack.



