On May 31, 2023 Progress Software disclosed a SQL injection vulnerability (CVE-2023-34362) in the MOVEit Transfer that could lead to escalated privileges and potential unauthorized access to the environment. Progress emphasized to its customers that it is extremely important to take immediate action.
Affected versions
MOVEit Transfer before 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1)
MOVEit Vulnerability Details
The SQL injection vulnerability found in the MOVEit Transfer web application allows an unauthenticated attacker to gain access to MOVEit Transfer’s database. Depending on the database engine being used (MySQL, Microsoft SQL Server, or Azure SQL), an attacker may be able to infer information about the structure and contents of the database and execute SQL statements that alter or delete database elements. The vendor added that this is exploited in the wild in May and June 2023. Exploitation of unpatched systems can occur via HTTP or HTTPS. All versions (e.g., 2020.0 and 2019x) before the five explicitly mentioned versions are affected, including older unsupported versions.
The CVSS Base score for this vulnerability is 9.8 and the vector is below:
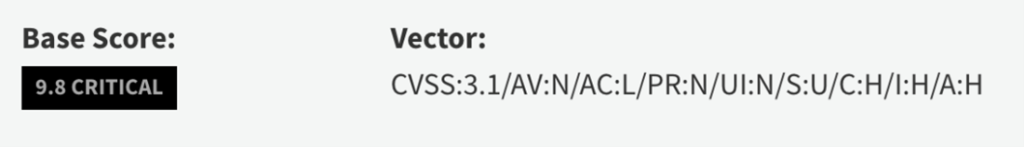
The above CVSS vector indicates that it’s a remotely exploitable network vulnerability. The access complexity is low meaning that an attacker can expect repeatable success when attacking the vulnerable component. There are no special privileges required and therefore an unauthorized attacker without any special access can successfully exploit this issue. The vulnerable system can be exploited without interaction from any user. No one needs to click on open any file or perform any other action. The vulnerability is wormable. And lastly, there is a complete compromise of confidentiality, integrity, and availability of the impacted system.
On June 2, CISA added this vulnerability to the Known Exploited Vulnerabilities (KEVs) Catalog
On June 7, The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) released a joint Cybersecurity Advisory to disseminate known CL0P ransomware IOCs and TTPs identified through FBI investigations. According to the report beginning on May 27, 2023, CL0P Ransomware Gang, also known as TA505, began exploiting a previously unknown SQL injection vulnerability which was later disclosed by the vendor on May 31.
Fidelis Security Response
Fidelis security has released detection for various indicators of compromise and indicators of attacks. Customers should patch immediately or deny HTTP/HTTPs traffic to the MOVEit transfer environment. Customers should review Fidelis alerts and act accordingly to delete any instances of human2.aspx and delete all APP_WEB_[random].dll files. Fidelis’ threat research team is continually tracking this and other emerging and evolving threats to ensure our customers are protected against the latest threats.
Customers should also review various remediation instructions from the vendor and the CISA advisory. If you are unable to follow the recommended mitigation steps, then taking the below security steps to help reduce risk to your MOVEit Transfer environment from unauthorized access. Please see here for MOVEit Security Best Practices.
- Update network firewall rules to only allow connections to the MOVEit Transfer infrastructure from known trusted IP addresses.
- Review and remove any unauthorized user accounts. See Progress MOVEit Users Documentation
- Update remote access policies to only allow inbound connections from known and trusted IP addresses. For more information on restricting remote access, please refer to SysAdmin Remote Access Rules and Security Policies Remote Access
- Allow inbound access only from trusted entities (e.g., using certificate-based access control).
- Enable multi-factor authentication. Multi-factor authentication (MFA) protects MOVEit Transfer accounts from unverified users when a user’s account password is lost, stolen, or compromised. To enable MFA, please refer to the MOVEit Transfer Multi-factor Authentication Documentation.
Read the press release on CISION PR Newswire.
Conclusion
CVE-2023-34362 has been leveraged by the Cl0p ransomware threat actor to compromise multiple organizations for data exfiltration and other malicious activities. The vulnerability has gained public attention and we expect other threat actors to also leverage this vulnerability. New attempts at exploitation will be accelerated. There is an official patch from the vendor, and we strongly urge customers to patch and review their XDR alerts.
Be sure to subscribe to the Threat Geek blog to stay up to date with the impact of this new vulnerability over the coming weeks.