In the previous blog, we described how to catch attackers targeting Active Directory (AD) in the reconnaissance stage, which is one of the earliest stages of the attack. We mainly focused on LDAP protocol, flagging suspicious queries.
In part two, we describe how to detect more advanced Active Directory attacks that are based on DCE/RPC protocol.
In an AD environment, DCE/RPC protocol-based attacks can have severe consequences. They can compromise domain controllers, escalate privileges, or facilitate lateral movement within the network. Active Directory leverages the RPC mechanism for various operations, making it an attractive target for adversaries.
We will focus on detecting the following Active Directory attacks using Network Traffic Analysis (NTA): DCSync, DCShadow and Extraction of domain DPAPI backup key from Domain Controllers.
DCSync Attack
About DSCync
Mitre: T1003.006
Attack name: DCSync
Common attacking tools: Mimikatz, Impacket
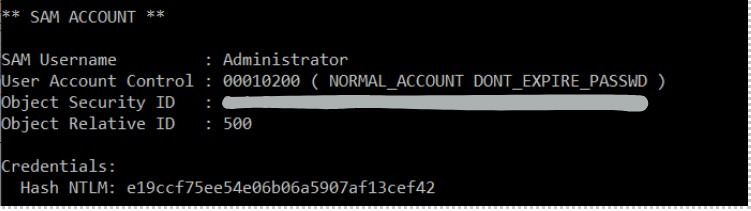
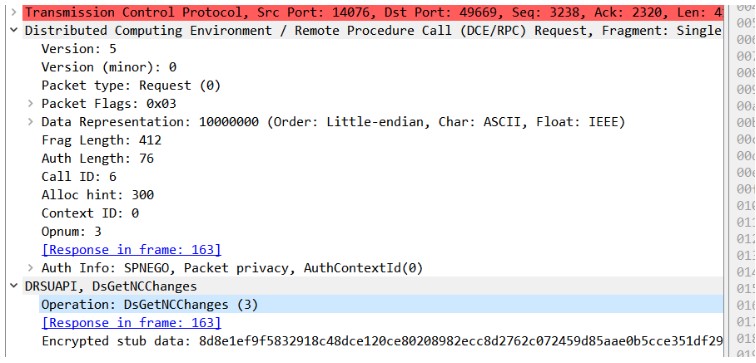
An attacker who compromised AD user account can pretend to be a Domain Controller (DC) and ask for sensitive information, provided the compromised account has the following permissions: Replicating Directory Changes, Replicating Directory Changes All. The attacker will leverage the Directory Replication Service Remote Protocol, which is used for replication between domain controllers. In particular, they will use the DSGetNCChanges function, which retrieves data updates from the DC.
While the attacker typically uses Mimikatz in these attacks, they can use other tools as well. Regardless, the tool will ask the DC for user and computer NTLM hashes stored at the AD database file (NTDS.DIT). After the attacker gets the hashes, they can try to brute force attack offline and determine passwords. Or, if using krbtgt service account hash, the attacker can perform a golden ticket attack.
How to detect DCSync Attack?
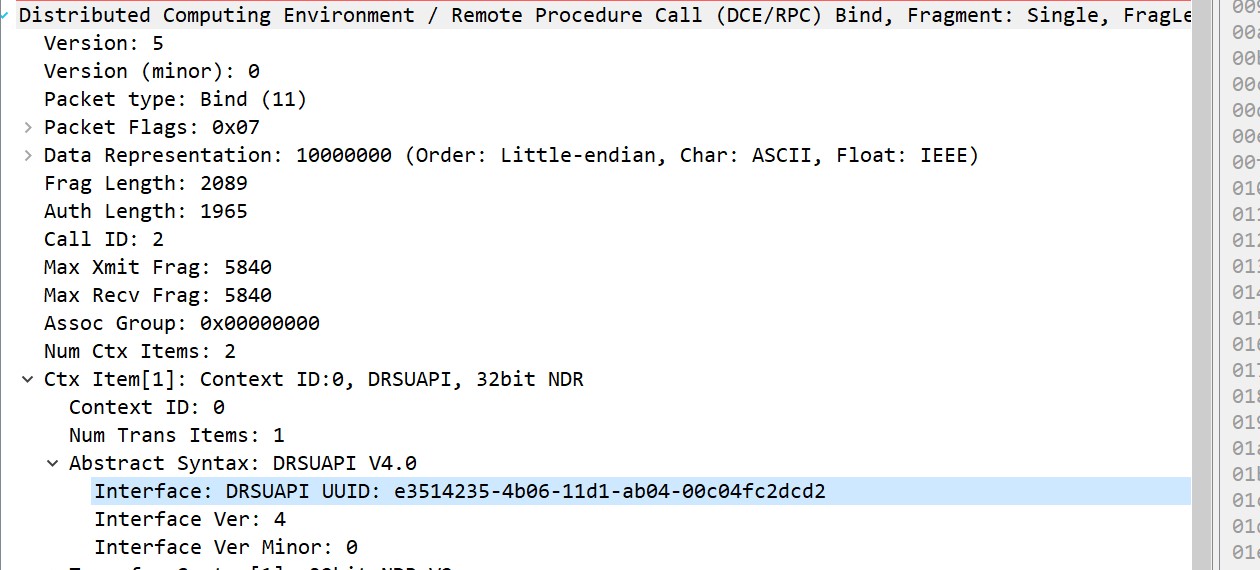
When using DCE/RPC protocol, the client specifies which RPC interface they want to connect to. After the connection is done, the client specifies which RPC procedures they want to use. When using DCSync attack, the attacker will send a bind request for DRSUAPI interface, and after the binding process is complete, they will send DSGetNCChanges request to the server, which is a request for AD objects updates. Detecting those packets from a non-DC to a DC will help us catch the DCSync attack in real time.
To detect a DCSync attack, we will analyze traffic between non-DC and a DC. We will capture the following packets for the detection:
1. DCE/RPC bind request for DRSUAPI interface:
2.DRSUAPI packet with DsGetNCChanges request:
DCSHADOW Attack
About DCSHADOW
Mitre: T1207
Attack name: DCShadow
Common Attacking tools: Mimikatz
In DCShadow attack, the attacker registers a machine as a DC, allowing the attacker to push changes to AD environment through replication between his rogue DC to the other DCs. The attacker will need to compromise a Domain Admin or Enterprise Admin account to perform the attack.
After registering the rogue DC, an attacker can change any AD object attributes in the domain.
The attack has a lot of similarities to DCSync attack. However, while DcSync gives the attacker the ability to read information from the DC, DCShadow allows the attacker to write and update the DC.
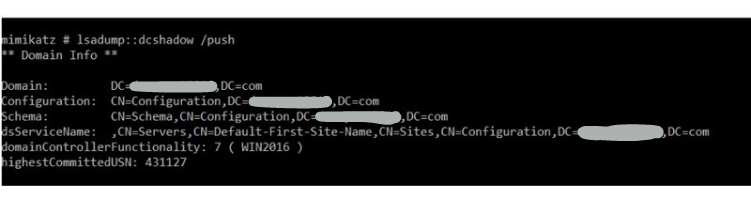
Detection Techniques for DCShadow
Like DCSync, In DCShadow attack, DRSUAPI interface is used. DCShadow using the following RPC procedures as part of his attack: –
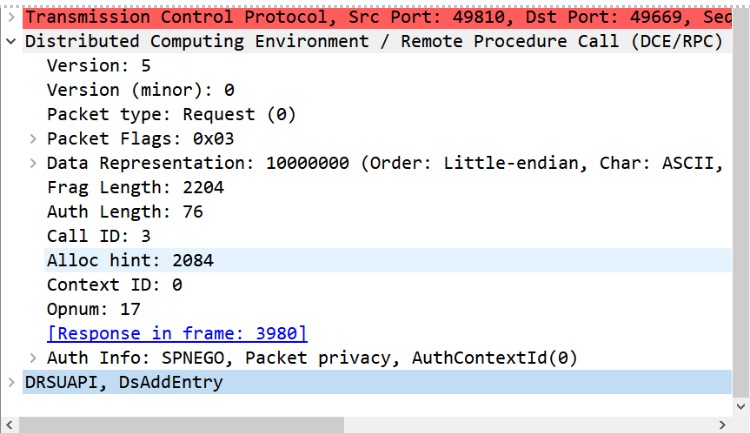
- DrsAddEntry: the attacker alters the spn of his rouge DC to “GC/*” in the domain Configuration partition.
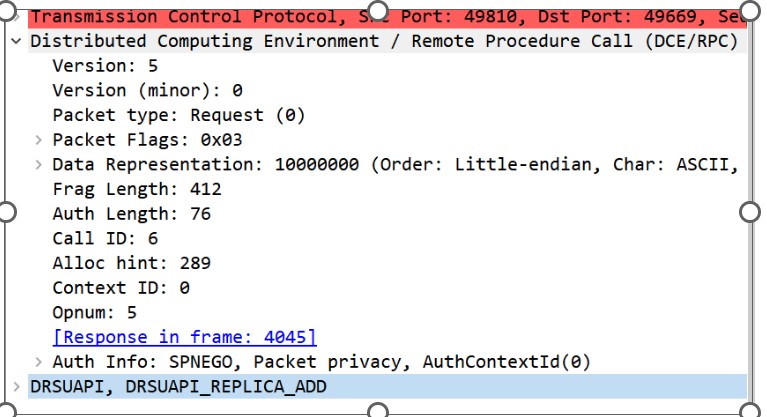
- DrsReplicaAdd: the attacker pushes the malicious Active Directory objects he changed to the DC.
To detect DCSync, we will catch a bind request for DRSUAPI interface, and RPC procedure requests for DrsAddEntry and DrsReplicaAdd. If the request originates from a non-dc to a dc we will alert.
To detect DCSync attack, we will analyze traffic between non-DC to A DC. We will capture the following packets for the detection:
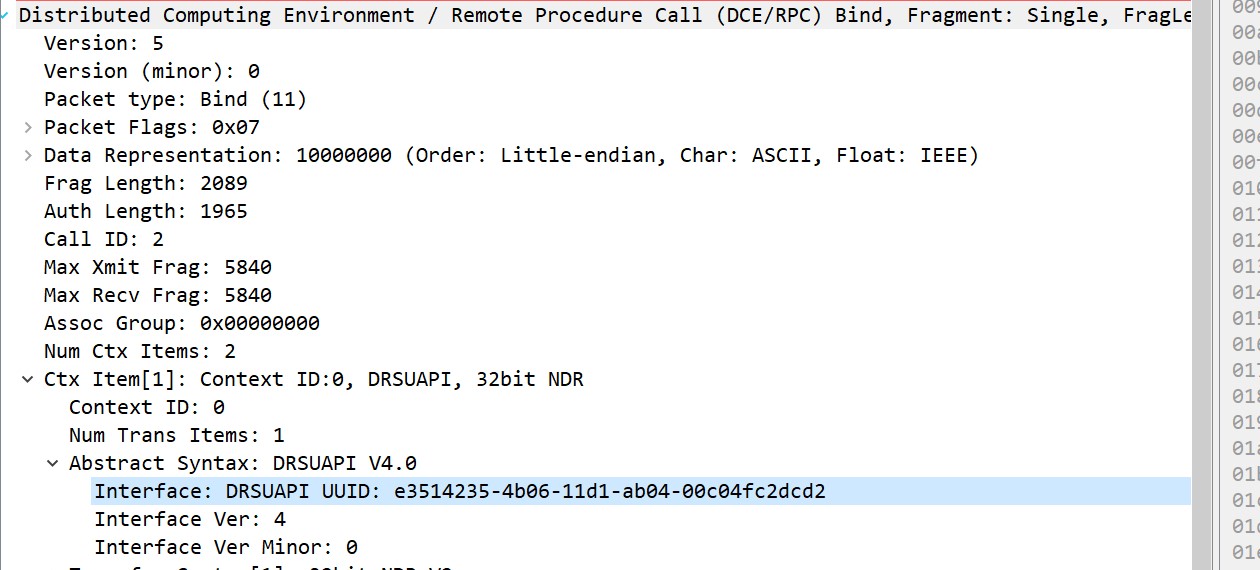
1. DCE/RPC bind request for DRSUAPI interface:
2. DRSUAPI packet with DrsAddEntry request:
3. DRSUAPI packet with DrsReplicaAdd request:
Reading Domain DPAPI BACKUP KEY FROM DOMAIN CONTROLLER
Mitre: T1555.003
Attack name: Domain DPAPI backup key extraction
Common Attacking tools: Mimikatz, SharpDPAPI, Impacket
Windows provides a mechanism for protecting asymmetric private keys, passwords, and confidential data. The mechanism, called DPAPI, performs symmetric encryption of data. Data Protection API (DPAPI) allows developers to encrypt data without the need for implementing the underlying encryption algorithm. Every windows user will have a DPAPI master key he can use to encrypt and decrypt data.
Common uses of DPAPI encryption include:
- Network passwords in Credential Manager
- Google Chrome cookies and login data
- Users pin and fingerprint in Windows 8
- WIFI passwords
- VPN passwords
- Email Account passwords
In an AD environment, the DPAPI master key is encrypted with the user domain password. Decryption of the DPAPI master key will allow attackers to read all the data protected by DPAPI. The domain controllers have a backup mechanism to recover domain users master keys (for the case of lost passwords). For every domain, the domain controllers have one pair of public and private keys associated with DPAPI. The clients in the domain use the domain DPAPI backup public key to encrypt their master key. If an attacker gains access to the domain DPAPI backup private key, he can decrypt any domain user’s DPAPI master key, allowing him to reveal all the confidential data encrypted with the DPAPI master key. The attacker will require admin privileges to extract the domain backup key from domain controllers.
Detecting DPAPI attack
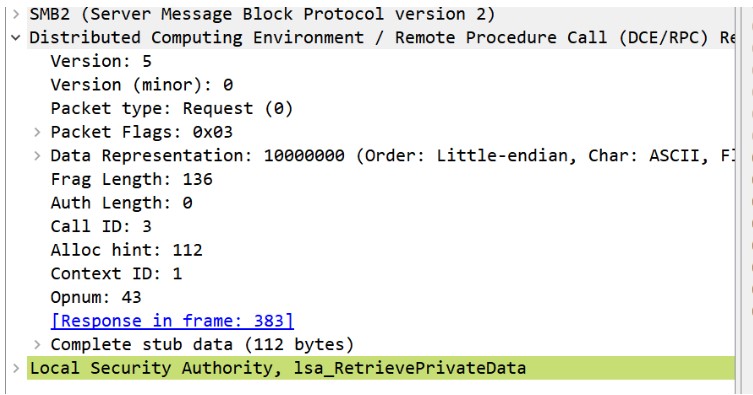
Attackers will use the LsaRetrievePrivateData function of the LSARPC interface in order to request the domain backup key from the DC. To detect the attacks, we will capture a DCE/RPC bind request for LSARPC interface, and a request for LsaRetrievePrivateData function from the DC.
To detect domain DPAPI backup key extraction attack, we will analyze all the traffic going into the DC.
We will look for attempts to get the domain DPAPI backup key from the DC.
We will capture the following packets for the DPAPI detection:
1. DCE/RPC bind request for LSARPC interface:
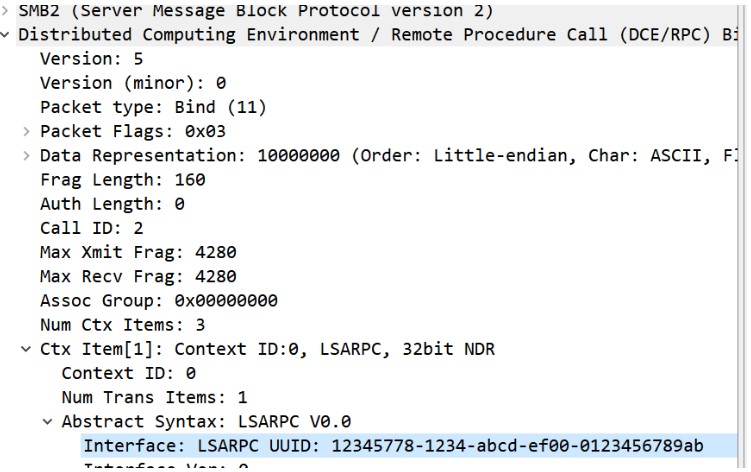
2. LSARPC packet with LsaRetrievePrivateData API request:
Conclusion
Cyber threat actors continually innovate, creating new and novel techniques to gain access to confidential information. Utilizing Active Directory attacks will allow adversaries to elevate privileges and move laterally on a compromised network, which may lead to a domain compromise. Applying detection rules helps catch the attackers early on before any damage is done.
To ensure the safety of your organization, it’s essential to keep your systems up to date and install an automated detection system like Fidelis Elevate®. Renowned for its comprehensive protection, spanning network, endpoint, and Active Directory security, Fidelis Elevate® helps proactively defend against cyber threats and active attacks.
Subscribe to the Threat Geek blog for the latest updates, threat research, and industry insights from the professionals at Fidelis Security. To see first-hand how the Fidelis Security platforms help security teams worldwide protect, detect, respond, and neutralize even the most advanced cyber adversaries across network, endpoints, and cloud, schedule a free demo.