When threats emerge, the Fidelis security Threat Research team (TRT) is ready. Each month, the Threat Intelligence Summary examines the latest threats and trends so you can stay resilient against cyber adversaries.
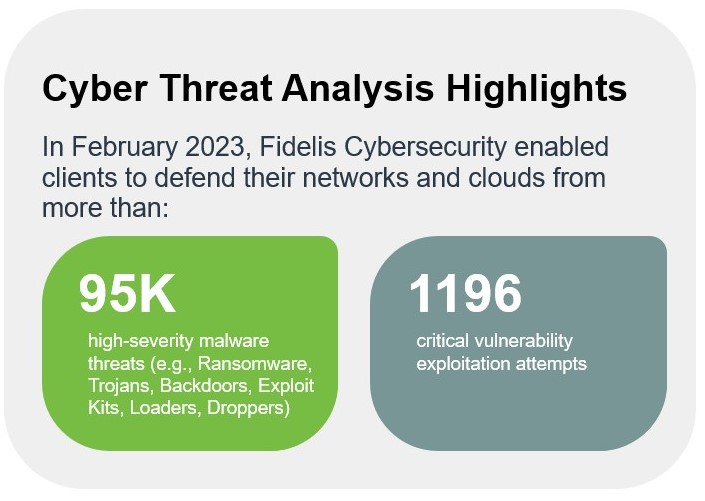
The February 2023 report details the return of a nation-state group’s espionage efforts, new cryptographic standards, a city paralyzed by ransomware, and the never-ending march of more data breaches and compromises. We also provide updates to the metrics and information on the most impactful vulnerabilities and malware strains in the wild today and included information on some of the top phishing sites observed over the month.
Read the February 2023 Threat Intelligence Summary
Top Emerging Vulnerabilities
The Fidelis security TRT’s top-ten vulnerability list for February 2023 includes critical and high severity CVEs that, when exploited, lead to privilege escalation, distributed denial of service attacks (DDoS), arbitrary code execution, and more.
This month’s list includes base scores for each of our top ten vulnerabilities. The base score is a complex calculation that weighs several factors, including exploitability (attack complexity, scope, privileges required, etc.), impact metrics, CVE maturity, and more. The value, from 0 to 10, represents the potential severity of the threat. The higher the number, the more critical the CVE.
These base scores serve as one reliable indicator of threat criticality. However, there are many factors that go into our top ten inclusion. The list presented in our report represents what we have observed as the month’s most credible threats to any organization using unpatched systems or software. Whether a vulnerability is newly discovered, has proofs of concept available, or is being actively exploited, regular patch management is imperative for securing your organization.
Malware Attacks by Industry
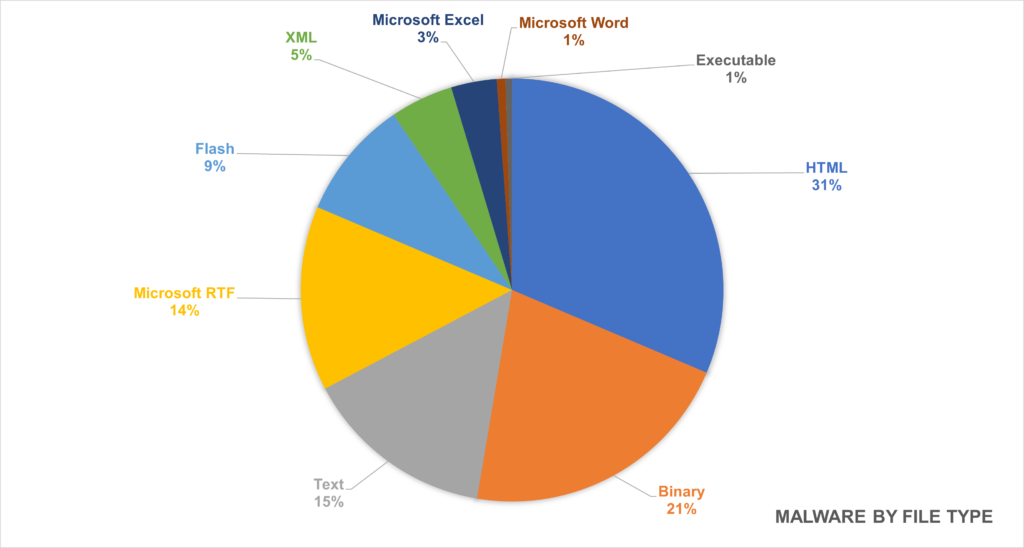
This month, we continued our survey of malware attacks by industry. In the latest report, you’ll see an overview of the top 10 hardest-hit industry sectors during the month of February. We also go into detail about which industries are seeing an increase in malware activity, and how we use this data to better safeguard our customers. We break down all observed malware samples and examine the most prevalent types of files attacked and the most observed malware types. Examining these trends more deeply, we delve into the most prevalent malware families observed both through our telemetry and through open-source reporting.
Top Phishing Domains
The Verizon, 2022 Data Breach Investigations Report indicates that 82% of data breaches stemmed from a user error, including clicking on phishing links. As adversaries grow more skilled, phishing is getting more and more difficult to detect. Breach identification and containment caused by phishing takes an average of 295 days, according to IBM’s 2022 Data Breach Report.
This month’s report contains five extremely active phishing sites observed in the wild right now. While the best defense against phishing is user vigilance, security teams can rely on emerging data like this to help bolster defenses.
See the top phishing domains list >
About the Fidelis Security Threat Research Team
The Threat Research team at Fidelis security researches and analyzes the latest threats and issues. The intelligence we gather from multiple open-source and proprietary sources about our cyber adversaries’ tactics, techniques, and procedures (TTPs) is fed directly into our platforms, products, and services to help our customers detect, neutralize, and eliminate threats before they can harm production systems.
Visit the Fidelis security Threat Research page to read the complete February 2023 Threat Intelligence Summary, along with information on critical threats and resources to help you better prepare for the next attack.



