In today’s digital age, businesses trust their information systems with a lot of sensitive data. Be it financial records, intellectual property, or personally identifiable information (PII) of customers and employees. Protecting this data is crucial for smooth business operations, financial stability, and to keep customer trust. However, an emerging cyber threat known as data exfiltration is quietly undermining these foundations.
Data exfiltration involves the unauthorized removal of sensitive information from a system. Unlike a disruptive ransomware attack that encrypts data and demands a ransom, data exfiltration operates stealthily. Attackers can compromise networks and exfiltrate data for weeks or even months without detection. By the time the breach is discovered, the damage may be irreversible. Data exfiltration attacks pose significant risks, including the loss of sensitive information and reputational damage. Cybercriminals are constantly evolving their tactics, making it essential for organizations to adopt comprehensive cybersecurity strategies to mitigate these risks effectively.
What is Data Exfiltration and how does it affect Enterprises?
Data exfiltration is the intentional, unauthorized transfer of sensitive data from a system or network. Unlike more overt cyber-attacks, data exfiltration operates stealthily, allowing attackers to extract sensitive data without being detected. This type of cyber-attack can be executed through various means, including phishing, spear phishing, and social engineering. The goal is to transfer data out of the organization, often for malicious purposes such as financial gain, espionage, or intellectual property theft.
Why Data Exfiltration Should Be a Top Security Concern for Organizations?
Data exfiltration is a serious threat to organizations. Protecting sensitive corporate data from exfiltration is crucial, as malware is often designed specifically to seek out and steal such data. It can trigger a chain reaction of severe consequences like:
Financial Losses
Exfiltrating sensitive financial data, such as credit card numbers, bank account information, or trade secrets, can result in massive financial losses. Attackers can use this information for several malicious purposes, including:
- Making fraudulent transactions
- Embezzling money or financial information
- Steal identities and impersonate individuals to open new accounts, get loans, or participate in other fraudulent actions.
Reputational Damage
Exfiltration can have lasting effects on an organization’s reputation, resulting in:
- Customer churn: Should customers sense a vulnerability in data handling they may migrate to competitors whom they perceive to offer heightened data protection.
- Amplified through social and traditional media, information about data breaches can become widespread attracting negative publicity towards the organization.
- Organizations will start losing business opportunities as it'll be challenging to gain new partners or investor's trust.
Regulatory Fines
Different industries have different data privacy regulations, and these regulations mandate specific data security requirements. Businesses that fail to protect personal information and experience a data breach often face substantial fines.

- The biggest challenges in securing regulated and sensitive data
- Key DLP compliance requirements
- Modern DLP technologies that help prevent costly security incidents
What are the types of Data Exfiltration?
There are several types of data exfiltration, each with its own methods and implications:
- Insider Threats: Insider threats occur when an authorized individual, such as an employee or contractor, intentionally or unintentionally exfiltrates sensitive data. This can happen due to human error, malicious intent, or physical access to sensitive data. Insider threats are particularly challenging to detect because they involve individuals who already have legitimate access to the data.
- Data Leakage: Data leakage happens when sensitive data is unintentionally exposed to unauthorized individuals. This can occur through email attachments, cloud storage services, or file transfer protocol (FTP). Data leakage often results from inadequate security measures or human error, making it a significant risk for organizations.
- Data Breach: A data breach is a broader term that refers to any incident where unauthorized access to data occurs. Data exfiltration is a specific type of data breach where data is illicitly transferred out of the organization. While all data exfiltration incidents are data breaches, not all data breaches involve data exfiltration.
- Data Theft: Data theft involves an attacker intentionally exfiltrating sensitive data for malicious purposes, such as financial gain or espionage. This type of data exfiltration is often carried out by external attackers who infiltrate the organization’s network and transfer data to an external location.
Preventing data exfiltration requires a comprehensive approach that includes implementing robust security protocols, conducting regular security audits, educating employees on data security best practices, using data loss prevention (DLP) tools, and monitoring network traffic for suspicious activity. By understanding the different types of data exfiltration and taking proactive measures, organizations can better protect their sensitive data from unauthorized transfer and potential breaches.
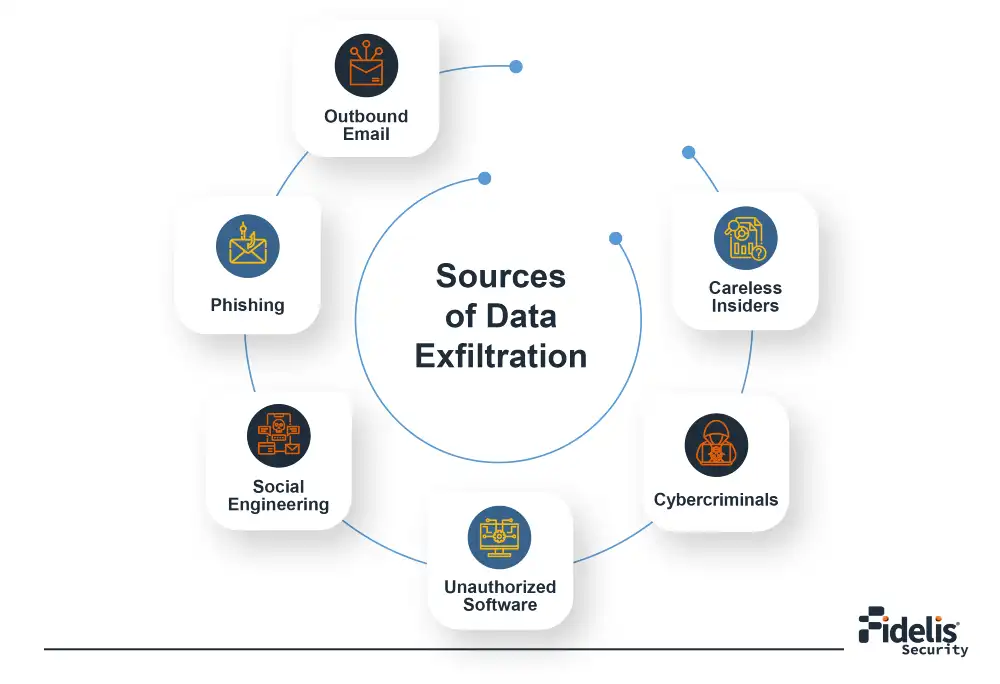
How Data Exfiltration Occurs: A Multifaceted Threat Landscape
A variety of methods are used by malicious actors to break through an organization’s security and get hands on the sensitive data. Here’s a closer look at some of the most frequent attack techniques:
Exfiltrated data can include source code, intellectual property, and customer information, all of which can lead to significant financial losses and security threats.
These won’t only impact individuals’ financial position but also have legal ramifications for the organization due to a data breach.
1. Malware
Malicious software remains a common threat vector for data exfiltration. Attackers can use various types of malwares, including:
- Keyloggers record keystrokes that can give away user’s login passwords, financial information, or other sensitive data.
- Data Stealers are designed to steal data like credit card information, PII, or intellectual property, from compromised systems and send it to an attacker-controlled remote server.
- Remote Access Trojans (RATs) give attackers remote access to a system. After that attackers can use it to look into files, steal data, and transfer it.
Malware can be used for exfiltrating data by transferring sensitive information from a compromised system to an attacker-controlled server.
This method uses human psychology to trick individuals into disclosing sensitive information. Common tactics include:
- Phishing emails that might appear to be from valid sources.
- A malicious attachment that once opened can download malware to one's system.
- Malicious Links can be used to redirect one to fake sites and then steal their credentials or other sensitive information once entered on to that fake page.
3. Exploiting System Vulnerabilities
Attackers target unpatched vulnerabilities in systems, including:
- Operating systems and applications
- Firmware and network devices
- Attackers can install malware by exploiting vulnerabilities.
- They can have long-term access to the system and steal data without being noticed.
4. Insider Threats
Insider threats are initiated by individuals who have authorized access to sensitive information, including:
- Employees who may steal data for personal benefit.
- Careless employees cause accidental exposure by mishandling the data.
- Employees who use their access to steal and sell the data to competitors or use it for unauthorized purposes.
Now that we know why exfiltration is a serious problem for organizations and in what ways it can be carried out, it’s time to look at the ways to prevent it from happening.
Comprehensive List of Strategies to Prevent Data Exfiltration
Data exfiltration is a big challenge that requires a sophisticated defense strategy. Data exfiltration prevention is a critical component of cybersecurity strategies aimed at protecting sensitive data from unauthorized transmissions. So, let’s jump into it without a delay and strengthen your security posture and prevent data exfiltration attempts:
1. Deploying a Best-in-Class Data Loss Prevention (DLP) Solution
Fidelis’ Network DLP is one of the solutions that comes in handy in protecting sensitive data against exfiltration. It is a core component of the Fidelis Network® platform. It uses Deep Session Inspection to monitor data movement across network and offers:
- Advanced threat detection feature which uses machine learning to identify exfiltration attempts.
- Content inspection & control feature to block unauthorized sharing of data.
- Automated response streamlines threat response.
Fidelis Network® DLP solution empowers organizations to have deep visibility into data movement, prevent data breaches, and ensure compliance with data privacy regulations.
- Integrated Features
- Ability to Stop and theft
- Accurate Inspection
- Enterprise Architecture Friendly

2. Cultivating a Security-Savvy Workforce
Teaching your employees about new trends in security domain and about emerging threats will help them fight against:
- Phishing attempts
- Social engineering tactics
- And identify suspicious activities
3. Maintaining Vigilance Through Patch Management
If you have unpatched vulnerabilities in your system, then attackers can take advantage of them. Here’s how regular maintenance improves your defenses:
- Regular vulnerability scanning helps in identifying the potential vulnerabilities before attackers can exploit them and steal data.
- Prioritize patching vulnerabilities that offer the highest risk of exploitation.
- Consider automating patch deployment processes as it'll help in lowering the possibility of human error and enables timely patching throughout your entire IT infrastructure.
3. Network Traffic Monitoring
Monitor network traffic for unusual or suspicious activities. This can help you gain vital information about potential data exfiltration attempts. Monitoring for unauthorized data transfer is crucial to prevent sensitive information from leaving your organization. Here are some practices that can help in improving network monitoring:
- Set baseline for your network traffic pattern. The baseline will be used as a reference point to spot deviations that may indicate unauthorized activities.
- Implement anomaly detection systems that will detect unexpected surges in network traffic. These can alert security personnel about probable exfiltration attempts in real time.
- Network segmentation can help limit attackers’ lateral movement within the system.
4. Enforcing Strong Password Policies and Multi-Factor Authentication (MFA)
Using weak passwords and the lack of MFA makes it easier for attackers to gain access and steal sensitive data. So, enforce strong password policies and Multi-Factor Authentication.
Data Exfiltration Incident Response: Mitigating Damage and Regaining Control
Even with robust preventative measures data exfiltration can still happen. You should have a well-defined data incident response plan to minimize damage, recover fast, and remain compliant with privacy policies. Here’s a step-by-step guide for data exfiltration incident response:
Identify and Contain the Breach: Time is of the Essence
- Use security tools and network monitoring to detect any suspicious behavior like unusual network traffic patterns, unauthorized access attempts, or DLP notifications.
- Once a potential threat is detected, isolate the compromised system or user account by quarantining compromised devices, restricting network access, or suspending user accounts.
- Depending on how bad the breach is, you need to take other containment measures such as password resets, taking away access privileges, or freezing affected systems.
Investigate the Incident
- Conduct a thorough forensic investigation to identify how bad and far spread the breach was, if any data was stolen, and what was the source of the breach. Look into log files, system activity, and other available evidence to find details about the breach.
- Create a thorough timeline of events to better understand the attacker's actions through your system. This will help in determining the point of entry, what attackers did, and when they stole the data.
- Look into all the details to figure out the weak point in your system. This will help in fixing the problem and prevent similar attacks in the future.
Remediate the Vulnerability: Building Stronger Defenses
- Fix the vulnerabilities that were exploited by attackers. Deploy security patches to your systems and software. Prioritize patching vulnerabilities with the highest risk.
- Strengthening your security measures by introducing extra security controls based on whatever you've learned for the investigation. This could mean strengthening access controls, evaluating and updating security rules, or deploying new security tools to fill in any gaps.
Notify Stakeholders: Transparency and Compliance
- Inform all internal stakeholders about the incident, including management, legal teams, and possibly affected departments. Be open about the problem, actions that are being taken, and what could be the consequences for the company.
- Depending on the incident and where the organization is located, you may be legally obligated to inform regulatory authorities, or law enforcement agencies about it. Consult with the legal team to make sure you are complying with all applicable data privacy regulations.
Recovery and Post-Incident Review: Learning from the Experience
- If backups are available, start the data recovery process as soon as possible to fix any damaged systems and data.
- Conduct a thorough post-incident review to assess what you did well and what can be improved. This should include all key stakeholders and making changes to your incident response plan and security procedures.
By following these steps, you will be able to handle such incidents better, minimize damage, and improve the organization’s overall data security posture. Remember, a well-rehearsed incident response plan and ongoing improvement are important for your organization to fight against cyberattacks.
- What data has been potentially exposed?
- Incursion detection and Persistence detection
- How should I respond?

Conclusion
Data exfiltration is a big problem that companies. Laying down proper plan will greatly minimize the risk of data exfiltration and secure their valuable data by identifying the dangers, deploying preventive measures such as Fidelis Network DLP, and maintaining a robust incident response plan.



2. Social Engineering