Breaking Down the Real Meaning of an XDR Solution
Read More As data travels across networks, it becomes vulnerable to interception. To safeguard
Want to stay ahead of threats in 2025? This research report is all you need to stay updated.
Picture this, you are trying to protect a chest full of treasure and have no idea what lurks in the shadows, waiting to take it all away. Scary, isn’t it? Fear should be the same when it comes to running a network without proper security.
How you’ll guard your treasure with everything you’ve got, network security solutions do the same. It protects your organization’s critical information from cyber threats. With time, attackers are upskilling, and the threats are becoming more sophisticated. So, the conclusion is finding the right security solutions that fit your requirements is crucial no matter what size your business is.
Protecting your data, maintaining client trust and your reputation should be top priorities.
Network security basically includes the policies, practices, and technologies to protect computer networks, devices, and data from unauthorized access, misuse, and impairment. A computer network facilitates communication and information sharing among multiple users, making network security essential to safeguard against threats. It consists of many different technologies, apparatus, and processes working hand-in-hand to provide multi-layer protection against cyber-attacks.
The purpose of network security is to ensure 3 fundamental principles:
Confidentiality: Making sure only authorized personnel have access to sensitive information.
Integrity: Making sure that the data is correct and not corrupted during transmission or storage.
Availability: Data should be accessible only to the authorized users when needed.
| Component | Description |
|---|---|
| Firewall | Acts as a line of defense between reliable internal networks and untrusted external ones. |
| Intrusion Detection Systems (IDS) | Monitors network traffic for suspicious activities. |
| Virtual Private Networks (VPNs) | Encrypts data during the process of transmission across the internet. |
| Antivirus Software | Protects against malicious software that could compromise network security. |
| Intrusion Prevention System (IPS) | Monitors network activities to identify and block malicious actions in real time. |
As businesses rely more on digital technology, the value of network security solutions cannot be emphasized. Cyber threats keep increasing the risk of and financial losses, plus the vast damage to reputation in a successful attack. Network security solutions help take on the bulk of the following security challenges:
Defending against network security attacks is crucial, and proactive strategies such as Intrusion Prevention Systems (IPS), effective monitoring, segmentation, and continuous training are essential to mitigate risks associated with cyber threats.
It is obvious from the ever-growing complexity of cyber threats that using a single security solution is enough. If you want complete protection then you’ll need a layered approach to security, use multiple solutions that complement each other.
To properly protect networks and data, enterprises must employ a wide range of network security solutions. Each of these network security solutions is aimed at certain aspects of network security. The result is that together they can provide very strong security against cyber-attacks.
Managed Security Service Providers (MSSPs) play a crucial role in enhancing an organization’s security posture without the significant investment required to build an in-house security operations center. MSSPs offer benefits such as cost savings and access to specialized security expertise, allowing organizations to manage their security needs more effectively while paying a predictable monthly fee for services.
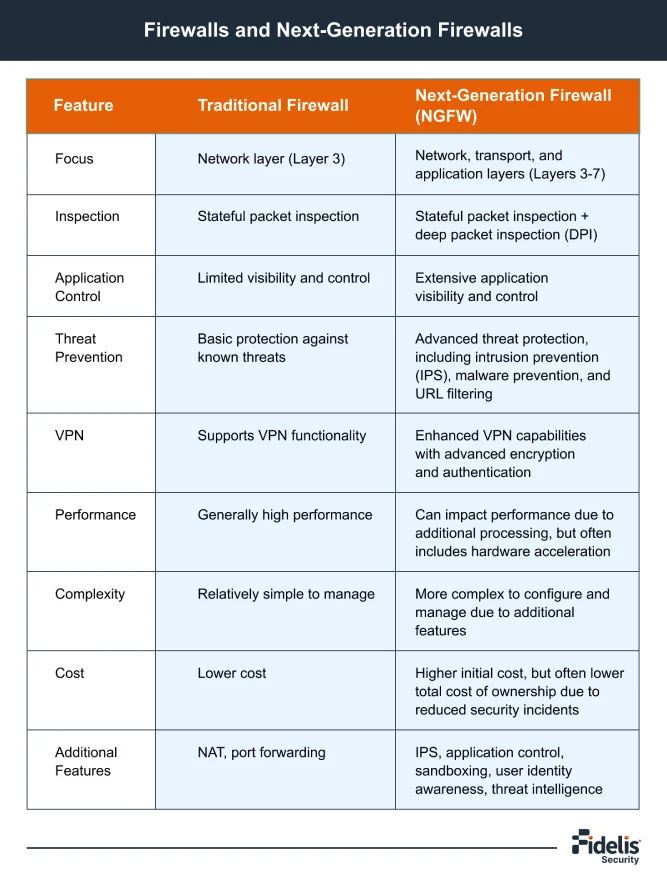
One of the most important components of any network security is undoubtedly a firewall. It acts as a shield and protects the trusted internet network from the untrusted one. And prevents unauthorized access and cyberattacks by constantly monitoring all incoming and outgoing traffic.
Next-generation firewalls (NGFWs) are the advanced version of the traditional firewall. It comes with advanced features like deep packet inspection, intrusion prevention, and application awareness. These features allow firewalls to detect and block complex network threats. Additionally, next-generation firewalls include features like intrusion prevention systems (IPS) for detecting and blocking various threats, such as network attacks and vulnerabilities, enhancing overall network security.
Intrusion Detection and Prevention Systems monitor the incoming and outgoing traffic over the network in real-time and analyses the data packets for signs of malicious activity. This is intended to provide intrusion detection and prevention against unauthorized access to network systems. It reviews packets of data as they flow over the network, which would readily allow it to block any such system based on the type of threat detected and issue an alert to network administrators. An intrusion prevention system (IPS) is a critical component of network security, monitoring network activities to identify and block malicious actions in real time.
There are two major types of IDPS:
NDR is a next-generation security solution, explicitly developed to complement any standard Intrusion Detection and Prevention Systems (IDPS). It provides total visibility, advanced threat detection, and real-time response capabilities, hence making it resilient and proactive for network security. NDR complements intrusion prevention systems (IPS) by providing advanced threat detection and real-time response capabilities, enhancing overall network security.
Consider NDR as your diligent custodian for the network ecosystem. Working on machine learning algorithms, this solution monitors network traffic, assesses behavioral patterns, and estimates threats continuously. In case of suspicious behavior, NDR can execute appropriate responses automatically to help protect your network from evolving cyber threats.
Fidelis NDR (Network Detection and Response) is a cornerstone of our network security offerings exceptional protection for your organization’s data, networks, and systems. As cyber threats grow, Fidelis NDR provides increased capabilities for detecting, analyzing, and responding to these threats in real time, ensuring your network’s security.
| Feature | Description |
|---|---|
| Advanced Threat Detection | Fidelis NDR employs sophisticated machine learning and behavioral analysis to detect advanced threats across your network, finding anomalies and potential breaches before they do harm. |
| Automated Response | Fidelis NDR uses automated threat response capabilities to quickly eliminate threats, minimizing response time and limiting potential damage. |
| Scalability | Fidelis NDR is built to scale with your organization, adapting to your network's changing security requirements without sacrificing performance. |
| Compliance Support | Fidelis NDR assists your firm in meeting industry-specific compliance requirements, ensuring that your network security adheres to regulatory standards. |
Fidelis NDR effortlessly integrates with your existing infrastructure, delivering a powerful, layered defense approach that protects every component of your network. Whether you are dealing with internal weaknesses or external threats, Fidelis NDR provides the total protection you require to keep your organization safe.

NAC solutions are all about making sure only authorized users and devices have access to network resources. Basically, the NAC system enforces security policies at the access point of a network; therefore, any unauthorized device would be unable to join a network and compromise its security. Secure access to corporate networks is crucial for protecting sensitive information transmitted over these networks, especially when remote access is involved.
NAC solutions authenticate users and devices to be connected to a network. The user’s identity, the device’s security posture, and whether both follow company regulations can be used as factors in authentication. Remote access plays a vital role in maintaining productivity and security for employees using personal devices and public Wi-Fi, ensuring they can securely connect to corporate networks from outside their offices.
Endpoint security solutions offer protection to certain specified devices, like a computer, a laptop, a mobile phone, etc., against security threats. Endpoint security has never been more critical considering the higher usage of mobile devices and remote work. This solution includes anti-virus software, encryption, and EDR systems. Remote access VPNs play a crucial role in providing secure network connections for individual clients or mobile users, utilizing encryption and multi-factor authentication to enhance data privacy and integrity.
EDR systems are very effective, especially due to the real-time monitoring and analysis of endpoint activity. If there is a sign of some suspicious activity, then the endpoint will be isolated, and the threat will not get a chance to spread. Remote access VPNs create private, encrypted connections that safeguard critical resources, enhancing productivity while protecting data from potential threats.
For instance, Fidelis Endpoint Detection and Response is like a personal bodyguard to endpoints. It provides real-time protection and visibility to devices over threat like malware, ransomware, etc. This visibility is achieved by continuous monitoring and fast reaction, which in turn helps in mitigating the impact of any security problem.
DLP solutions work to prevent the loss of sensitive information. Basically, DLP solutions monitor and control the flow of data over the network such that sensitive information is not delivered to unauthorized parties. This might be very important, even more so to firms dealing in sensitive information like financial data, personal information, and intellectual property.
DLP systems identify sensitive data in motion over a network and enforce policies regarding how this data should be accessed, used, or shared. For instance, it blocks sensitive data from being sent via e-mail or prohibits access to certain files by unauthorized users.
Fidelis Network Data Loss Prevention solution enable extended monitoring and control of data flow. It empowers an enterprise with a means to protect its sensitive information and prevent any breaches, while also meeting the many compliance requirements imposed by law. DLP puts your most valuable assets under protection from unwanted access and data breaches.

Network segmentation is breaking down a network into smaller independent segments to enhance security and performance. By fragmenting resources, an organization minimizes potential damage from breaches and spreads to core systems. Segmentation enhances network efficiency by minimizing congestion and optimizing traffic flow.
Zero Trust Network Access (ZTNA) questions the traditional network security concept, which depends on confidence within the network perimeter. Through a rigorous enforcement of authentication and permissions criteria, ZTNA significantly reduces the chances of unauthorized access and instances of data breaches.
Network monitoring tools are important in maintaining visibility across the network. These technologies will continue to scan network data for any unusual patterns that may indicate a security breach. Monitoring tools enable firms to quickly notice threats and reduce their impact by responding quickly; they are often used together with other security measures for complete protection.
Access control and authentication are critical components of network security, ensuring that only authorized individuals and devices can access network resources.
Access control involves the process of granting or denying access to network resources based on user identity, role, or other factors. This can be achieved through various methods, including:
Authentication and authorization are two related but distinct processes that work together to ensure secure access to network resources.
By implementing robust access control and authentication measures, organizations can ensure that only authorized users and devices can access their network resources, thereby enhancing overall network security.
Network security technologies are designed to protect computer networks from various types of threats, including unauthorized access, malware, and denial-of-service attacks.
Secure Access Service Edge (SASE) is a cloud-native security framework that converges networking and security functions to provide secure access to applications and services. SASE combines the benefits of software-defined wide-area networking (SD-WAN) and security as a service (SaaS) to offer a comprehensive solution for modern network security challenges.
SASE provides several benefits, including:
SASE is particularly useful for organizations with remote workers, branch offices, or cloud-based applications, as it provides a secure and scalable solution for accessing these resources. By adopting SASE, organizations can enhance their network security posture while also improving operational efficiency and reducing costs.
Network security is one of the most important organizational cybersecurity strategies in an organization. Now that you know about the many options in network security, implementation for these could prove very effective in securing your network from various forms of attacks. offers comprehensive state-of-the-art solutions for keeping your network secure to take your business forward with confidence.
Not having a strong network security plan today, in this fast-moving digital landscape where cyber threats keep evolving, is not feasible. With Fidelis Security, you’ll be better prepared to protect yourself against current and future threats so that you can rest easy and focus on what really matters: Your Business!
It depends on the needs of your organization; there is no one-size-fits-all solution. When selecting a solution, many criteria must be kept in mind. These include the size of an organization, network complexity, threat landscape, and regulatory compliance—in addition to technical capabilities and budget—and most importantly, the type of data you handle.
Most of the firms combine solutions such as firewalls, IDS/IPS, NDR, EDR, and DLP to secure their network. Additionally, a virtual private network (VPN) plays a crucial role in securing connections between devices and networks, particularly for remote access scenarios.
However, before choosing a solution, ensure that it is based on parameters like the vendor record, usability of the solution, and scalability with your network.
Checking your network security involves several steps:
Sarika, a cybersecurity enthusiast, contributes insightful articles to Fidelis Security, guiding readers through the complexities of digital security with clarity and passion. Beyond her writing, she actively engages in the cybersecurity community, staying informed about emerging trends and technologies to empower individuals and organizations in safeguarding their digital assets.
See Fidelis in action. Learn how our fast and scalable platforms provide full visibility, deep insights, and rapid response to help security teams across the World protect, detect, respond, and neutralize advanced cyber adversaries.