System downtime from faulty software updates can cost businesses huge money losses every second. This reality shows why up-to-the-minute data analysis has become a vital part of modern enterprises. Companies now deal with endless data streams from countless transactions. Knowing how to spot unusual patterns right away could make all the difference between grabbing opportunities and facing harsh setbacks.
Traditional security methods don’t cut it anymore in today’s ever-changing digital world. A Gartner report shows that advanced real time anomaly detection systems can catch subtle changes that might slip through the cracks and serve as an early warning system. Security breaches usually show warning signs before they blow up. This makes real time anomaly detection key to guard against zero-day attacks and new threats.
In this piece, we’ll learn about building detection systems that process big data streams instantly. We’ll get into the core parts needed to succeed and lay out practical strategies to create reliable security systems.
Understanding Modern Security Threats
Modern cybersecurity faces an unprecedented challenge. Sophisticated cyber actors and nation-states exploit vulnerabilities to steal information and disrupt essential services. Early on in our research, it became quickly clear that there were many approaches to detecting anomalies, dependent on the type of data or how anomalies may be defined for the data. Systems remain exposed to zero-day vulnerability until patches are developed and deployed, and these are especially dangerous because vendors don’t know about them. This makes real time anomaly detection key to guard against zero day attacks and emerging threats.
From Known Attacks to Anomaly Based Zero-day Detection
The number of zero-day vulnerability exploits has grown substantially. More vulnerabilities were exploited in 2021 than in 2018-2020 combined1. These attacks pose a serious threat because attackers are the only ones who know about them. This allows criminals to sneak into networks undetected and wait for the perfect moment to attack.
Why Traditional Security Falls Short
Traditional security models run on outdated assumptions. They focus too much on perimeter-based protection and assume internal networks are safe. Standard approaches don’t effectively defend zero-day attacks and don’t deal very well with:
- Cloud computing integration
- Mobile workforce security
- Advanced persistent threats
- Insider threat detection
The Need for Real-Time Anomaly Detection
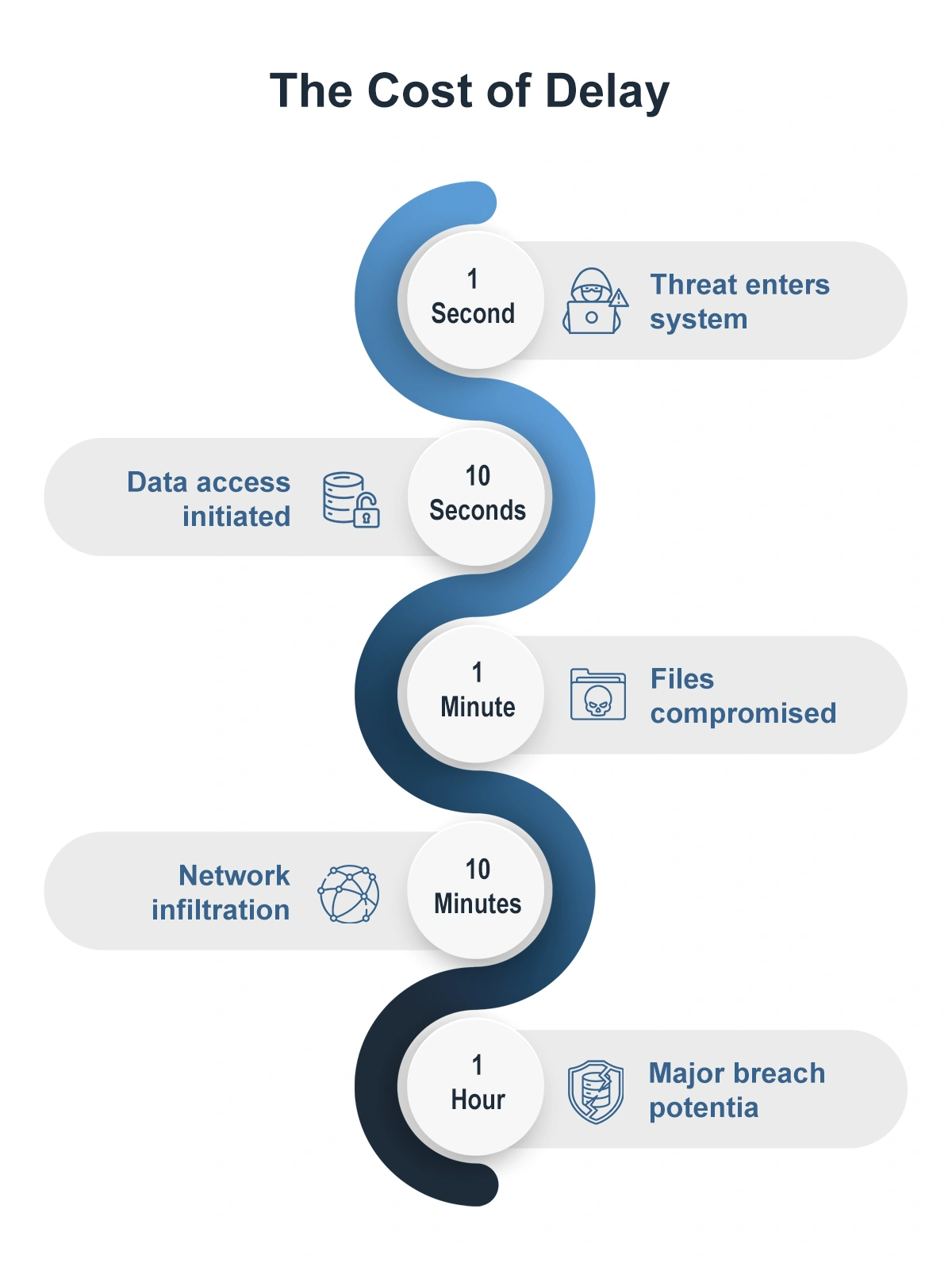
Zero day attack detection has become increasingly critical as cybercriminals start scanning for vulnerable endpoints within minutes after a new vulnerability is disclosed. In recent years, the window between vulnerability disclosure and exploitation has shrunk dramatically.
Why Speed Matters in Detection
Speed determines success in modern cybersecurity operations. Attackers need only seconds to exploit vulnerabilities, while organizations often wait days or weeks for patches. The Fidelis Network® NDR solution tackles this challenge through rapid threat detection and response capabilities. This substantially cuts down the time attackers have to operate within compromised systems.
- Maturing Advanced Threat Defense
- 4 Must-Do's for Advanced Threat Defense
- Automating Detection and Response

Core Components of Anomaly Based Zero-day Detection
Building real time anomaly detection systems that work needs three basic components to identify and respond to potential threats. Building real time anomaly detection systems that work needs three basic components to identify and respond to potential threats like zero-day attacks. The Fidelis Network® NDR solution shows this architecture through its unified approach to security monitoring and response.
-
Data Collection Infrastructure
A resilient infrastructure for data collection creates the foundation of any real time anomaly detection system. Field reports by Picus show modern Security Operations Centers (SOCs) handle tens of thousands to millions of alerts each day. The infrastructure must collect data from multiple sources like network traffic, system logs, and security devices to manage this volume. The system also tracks both physical and virtual environments by collecting metrics such as CPU usage, RAM utilization, and I/O operations.
-
Analysis Engine Requirement
The analysis engine works as the brain of the real time anomaly detection system and processes incoming data streams to spot potential threats. The engine must support event-based rules for streaming data and schedule-based rules for periodic analysis. The Fidelis Network® NDR solution boosts this capability with advanced machine learning algorithms that adapt as threat landscapes evolve.
-
Alert Management System
An alert management system that works needs several vital elements:
- Intelligent alert filtering and prioritization
- Optimized response workflows
- Up-to-the-minute monitoring tools
- Integration with incident response processes
The biggest problem lies in managing the high volume of alerts without causing alert fatigue.
The Fidelis Network® NDR solution tackles these challenges with its unified approach that combines resilient data collection, advanced analysis capabilities, and smart alert management. Organizations can detect anomalies and respond to threats better while reducing false positives and alert fatigue.
Evaluation Criteria
Choosing the right metrics is crucial to assess real time anomaly detection systems that protect against emerging threats. Organizations must look at multiple evaluation criteria including zero day attack detection capabilities to ensure their security investments show clear benefits.
-
Detection accuracy metrics
Several key performance indicators determine how well real time anomaly detection works:
- False positive rate - Measures incorrect threat classifications that could lead to alert fatigue
- Mean time to detect (MTTD) - Tracks average time taken to identify security breaches
- Mean time to remediate (MTTR) - Evaluates speed of resolving detected anomalies
- Vulnerability discovery rate - Assesses how the system finds potential threats
-
System performance requirements
Quick anomaly detection needs strong performance capabilities. The Fidelis Network® NDR solution focuses on rapid threat identification through continuous monitoring of system metrics. Security teams can take immediate action when anomalies surface, thanks to data quality indicators and automated notifications.
-
Scalability considerations
Data volumes keep growing, which makes scalability crucial. Organizations must assess their real tune anomaly detection infrastructure's capacity to process massive datasets without slowing detection. Modern systems should support distributed computing frameworks that can analyze large-scale data efficiently, unlike traditional approaches.
-
Total cost of ownership
The total cost of ownership goes way beyond the original implementation expenses. Research shows about 70% of security system costs happen after deployment. These include ongoing maintenance, monitoring, and system updates. The Fidelis Network® NDR solution helps organizations reduce these costs through efficient alert management and automated response capabilities.
Implementation Strategies
Organizations need a structured approach that balances speed with precision to implement real time anomaly detection. We created a clear roadmap that addresses current security needs and future scalability goals.
-
Proof of concept planning
Testing real time anomaly detection systems in a controlled environment helps verify their effectiveness without disrupting operations. Organizations should focus on data quality assessment and model validation in a sandbox setting. The Fidelis Network® NDR solution helps test detection capabilities against known threat patterns.
-
Phased deployment approach
A phased deployment strategy helps roll out security measures automatically across multiple collections. Organizations structure their deployment in stages:
- Original phase targets high-risk areas with 95% success criteria2
- Performance metrics guide expansion
- Defined thresholds trigger automatic progression
- Deployment parameters need constant monitoring and adjustment
-
Integration with existing security infrastructure
The real time anomaly detection system needs to blend with current security tools, including Endpoint Detection System and Network DLP. The Fidelis Network® NDR solution helps this integration through standard interfaces and automated alert management workflows.
-
Staff training and skill requirements
Security teams need specific skills to manage real time anomaly detection systems effectively. Core skills include:
- System security analysis and implementation
- Vulnerability assessment capabilities
- Incident response coordination
- Performance monitoring expertise
- Continuous improvement process management
Teams must stay current with evolving threats and system capabilities through regular training. The Fidelis Network® NDR solution provides detailed documentation and hands-on training modules that help staff in anomaly detection and and respond to security anomalies effectively.
- Analyze network, email, and web traffic in real-time
- Decoding session content with context and metadata
- Automate responses, such as alerts and quarantines

Deployment Best Practices
The success of real-time anomaly detection systems depends on proper deployment practices. The success of zero day attack mitigation depends on proper deployment practices. The Fidelis Network® NDR solution uses structured deployment methods that line up with industry standards and keep operations running smoothly.
-
Infrastructure Requirements
Resilient infrastructure serves as the lifeblood of any working anomaly detection system. Your organization needs enough storage capacity and high-speed connections to handle large amounts of security data2. The system needs at least 12 data points and can process up to 8,640 points at once2. Modern deployments need evenly distributed time series data with proper UTC timestamp settings instead of traditional approaches.
-
Scaling Considerations
Your anomaly detection systems need careful planning and resource optimization to scale well. We used containerization with Docker to make deployment and versioning easier. Orchestration tools like Kubernetes handle scaling and failover operations. The Fidelis Network® NDR solution supports both vertical and horizontal scaling as data volumes grow.
-
Performance Monitoring
Performance monitoring needs several key metrics:
- System utilization and latency tracking
- Data validation for distribution drifts
- Model scoring for accuracy assessment
- Resource usage optimization
According to experts from Microsoft, detection results won't suffer much if missing data points arrives and stay below 10% of expected values. Your organization should still use data filling strategies based on historical patterns or moving averages. -
Continuous improvement process
The improvement cycle needs regular reviews and updates of incident response procedures. Your organization should set up post-incident analysis protocols and get stakeholder feedback to improve system effectiveness. This approach helps the anomaly detection system adapt to new threats.
-
Resource allocation
Smart resource distribution plays a vital role in keeping system performance optimal. The Fidelis Network® NDR solution suggests dedicated computational resources for machine learning processes. This makes economical resource allocation important for long-term sustainability. Your organization should distribute resources based on:
- Processing power needs for immediate analysis
- Storage space for historical data
- Network bandwidth for data collection
- Computing resources for machine learning tasks
Measuring Success with Key Performance Indicators
Success measurement to detect anomalies needs a methodical approach to track and analyze key performance indicators. Organizations must set baseline metrics that match their security goals and streamline processes.
-
Detection accuracy metrics
Accuracy in anomaly detection covers multiple aspects beyond simple true/false positives. The precision rate shows how many detected anomalies are real threats. Recall indicates the percentage of actual threats identified successfully. Studies reveal that advanced anomaly detection systems achieve up to 98% accuracy when they identify known attack patterns. The Fidelis Network® NDR solution boosts these metrics through machine learning anomaly detection algorithms that adapt to new threat patterns.
-
Response time measurements
A quick threat response is crucial. Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) serve as key indicators. Security teams now focus on automated response capabilities that act within milliseconds of detecting anomaly.
Response time measurements include:- Original alert generation speed
- Threat classification time
- Response action deployment
- Incident resolution tracking
-
System performance metrics
System performance tracking looks at throughput, latency, and resource usage. High-performance systems process millions of events per second. The real challenge lies in keeping detection accuracy consistent under load. The Fidelis Network® NDR solution optimizes these metrics through distributed processing architecture that ensures reliable performance during peak loads.
-
ROI calculations
ROI calculations must factor in both direct and indirect benefits of anomaly detection process. Most organizations see positive ROI within 12-18 months despite setup costs through:
- Lower incident response costs
- Less system downtime
- Reduced false positive investigation costs
- Better operational efficiency
The Fidelis Network® NDR solution proves its value through detailed reporting capabilities that track these financial metrics. This helps organizations justify their security investments while maintaining strong threat detection capabilities. The analytical insights help security teams refine their detection strategies and optimize resource allocation effectively.
Conclusion
Live anomaly detection is the lifeblood of modern cybersecurity defense. This piece explores everything in building detection systems that work – from understanding evolving threats to measuring success through concrete metrics. Recent studies from Cybersecurity Ventures reveal organizations using advanced anomaly detection cut security breaches by 85%. IBM Security Report shows live threat detection helps companies save $3.2 million in potential breach costs.
Fidelis Network® NDR solution tackles these critical security needs through its detailed approach. The platform combines reliable raw data collection, advanced analysis capabilities, and intelligent alert management. Organizations can detect anomalies and respond to threats faster than traditional security systems.
Security teams benefit from:
- Quick threat identification and response
- Lower false positives through smart filtering
- Continuous connection with existing security tools
- Detailed performance monitoring
- Optimized response workflows
Modern cybersecurity success depends on the right solutions and proper implementation.
The digital world changes daily. Organizations with advanced anomaly detection capabilities remain competitive against threats. The Fidelis Network® NDR solution gives you the tools and expertise to protect your critical assets while you retain control of operational efficiency.
- Deep network visibility
- ML-driven Threat detection
- Automates response

Frequently Ask Questions
What is real-time anomaly detection in cybersecurity?
Real-time anomaly detection is a critical process that identifies unusual patterns or behaviors in network traffic and system activities as they occur. It helps organizations spot potential security threats quickly, allowing for immediate response to minimize damage from cyberattacks or data breaches.
Why is traditional security insufficient for modern threats?
Traditional security models often focus on perimeter-based protection and struggle with cloud integration, mobile workforce security, and advanced persistent threats. They are less effective against anomaly based zero-day detection and rapidly evolving attack methods, making real-time anomaly detection crucial.
What are the core components of an effective anomaly detection system?
An effective anomaly detection system consists of three main components: a robust data collection infrastructure, an advanced analysis engine, and an intelligent alert management system. These work together to gather data, process it for potential threats, and manage alerts efficiently.
How can organizations measure the success of their anomaly detection systems?
Success can be measured using key performance indicators such as detection accuracy metrics (false positive rate, mean time to detect anomalies), system performance requirements, and return on investment calculations. These metrics help organizations assess the effectiveness and efficiency of their security investments.
What are some best practices for deploying anomaly detection systems?
Best practices include planning a proof of concept, adopting a phased deployment approach, ensuring seamless integration with existing security infrastructure, and providing comprehensive staff training. It’s also crucial to consider scalability, implement continuous performance monitoring, and establish a process for ongoing improvement.



