“It takes 18 days on average for organizations to recover from a ransomware attack” – IBM Cost of a Data Breach Report 2024.
The clock starts ticking as soon as ransomware hits your network. Attackers no longer rely solely on opportunistic phishing; they now attack weak network defenses, move laterally across systems, and encrypt important data before demanding a ransom. Traditional security solutions sometimes notice breaches too late to adequately detect threats.
This is where network detection and response (NDR) solutions come in handy. NDR offers real-time threat monitoring, behavior-based anomaly detection, and quick response capabilities to combat ransomware before it spreads.
How Does Ransomware Spread Through a Network?
Malicious actors use multiple stages to carry out modern ransomware attacks. Phishing emails, compromised credentials, or software vulnerabilities are used by attackers to infiltrate networks. Once inside, they move laterally, seeking valuable data before launching encryption. Common tactics include:
- Exploiting Remote Desktop Protocol (RDP) & VPN vulnerabilities
- Credential dumping and privilege escalation
- Disabling endpoint security controls
- Deploying malware payloads in network shares
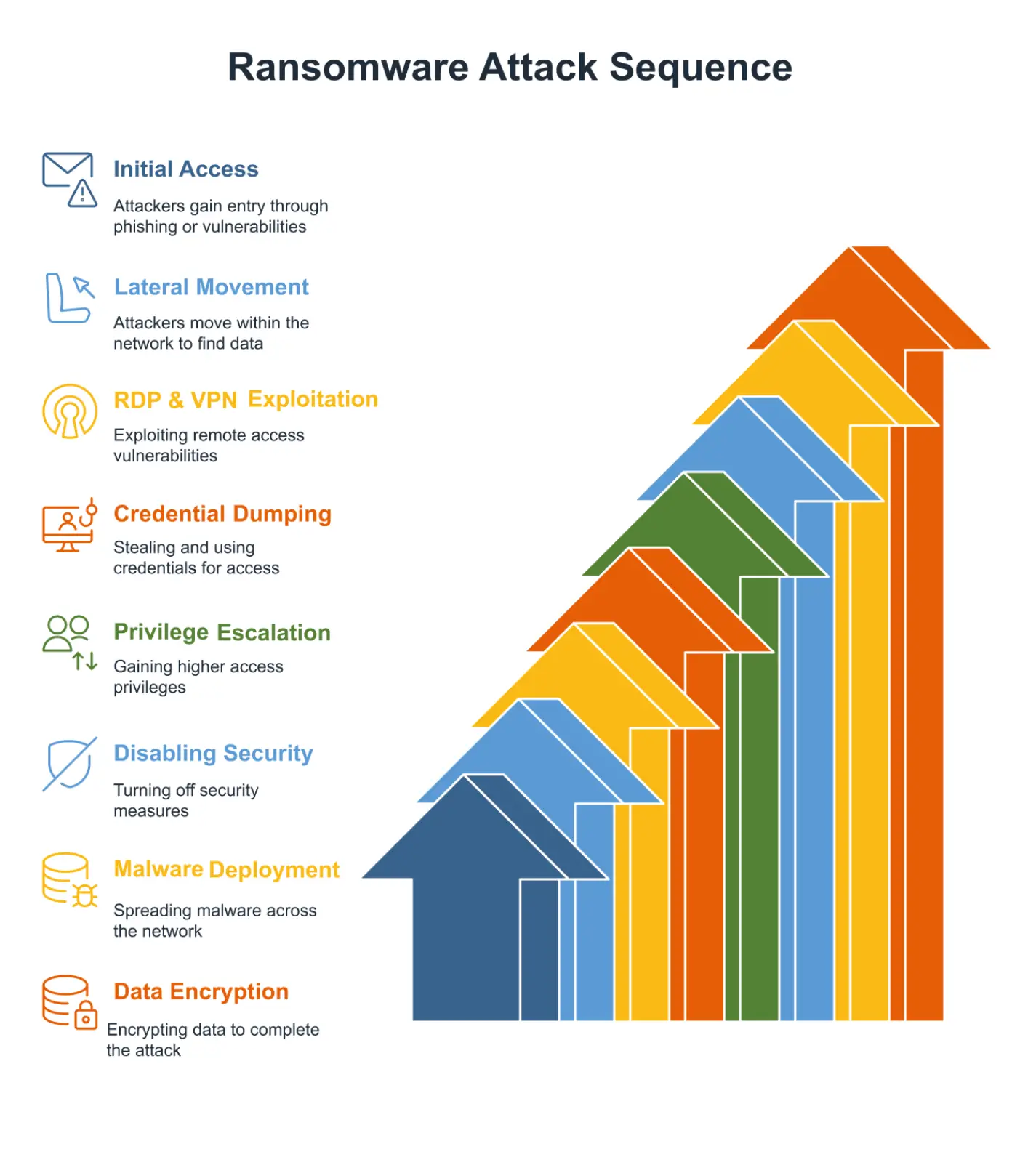
According to ReliaQuest’s 2025 Annual Cyber-Threat Report, cyber attackers can achieve lateral movement within just 27 minutes, quickly gaining deeper access to critical systems and increasing the impact of a ransomware attack.
- Maturing Advanced Threat Defense
- 4 Must-Do's for Advanced Threat Defense
- Automating Detection and Response

Why Traditional Security Fails Against Modern Ransomware
-
Signature-Based Detection is Too Slow
Traditional antivirus and intrusion detection systems rely on known malware signatures. But ransomware variants mutate rapidly—often before security updates are available.
-
Endpoint Security is Easily Bypassed
Ransomware can disable or evade endpoint detection and protection using fileless attacks or stolen administrator credentials.
-
Perimeter Defenses Alone Are Insufficient
Firewalls and Secure Email Gateways can block initial phishing attempts but won’t stop ransomware that gains access through trusted accounts or zero-day vulnerabilities.
How NDR Detects and Stops Ransomware in Real Time
1. Continuous Network Traffic Analysis
NDR enables 24/7 real-time monitoring of all network activity, making sure that even the most complex ransomware threats are caught early. NDR examines both north-south traffic (external communications) and east-west traffic (internal lateral movement) to ensure that threats do not pass unnoticed, in contrast to traditional security solutions, which concentrate on perimeter defenses.
NDR continuously monitors and detects:
- Unusual spikes in data transfer, which could indicate data exfiltration or mass encryption attempts.
- Anomalous changes in file extensions, a hallmark of ransomware encrypting files.
- Unauthorized access attempts, especially from privileged accounts that ransomware often targets.
This is carried out by doing deep packet inspection (DPI), flow data analysis, network telemetry, and network metadata evaluation. Unlike traditional signature-based detection, which requires prior knowledge of threats, NDR detects behavioral irregularities that may suggest ransomware before the payload is executed.
2. Behavior-Based Anomaly Detection
Ransomware constantly evolves to bypass signature-based detection methods, making it crucial to detect sophisticated threats. By establishing a baseline of normal network behavior and flagging deviations in real time, this approach of NDR identifies anomalies prior to an attack. Key anomaly detection mechanisms include:
- User and Entity Behavior Analytics (UEBA): Analyzes typical user and device behaviors. If an endpoint suddenly starts encrypting numerous files or accessing sensitive systems, it sends an alert to the security team.
- Machine Learning Algorithms: Continuously refine detection capabilities by adapting to new ransomware tactics, reducing false positives while ensuring rapid detection of emerging threats.
- Threat Intelligence Integration: NDR solutions ingest and analyze global threat intelligence feeds, allowing them to compare suspicious activity against known ransomware campaigns.
NDR uses multi-dimensional analytics to provide high-fidelity detection, reducing alert fatigue and ensuring that security teams concentrate on genuine threats.
3. Lateral Movement Detection
Ransomware rarely executes its attack immediately upon infiltration. Instead, it moves laterally, escalating privileges and infecting additional devices before deploying its final payload. NDR helps detect and stop this lateral movement in real time by monitoring the entire network infrastructure:
- Monitoring authentication requests to detect unusual login attempts or credential stuffing.
- Identifying abnormal communication patterns between endpoints that do not typically interact.
- Detecting communications with C2 servers, which are often used by ransomware operators to issue orders.
NDR can, for instance, flag the activity, isolate the device, and stop the attack from spreading further if an employee’s machine suddenly starts communicating with multiple servers it has never accessed before.
4. Automated Response & Containment
When ransomware is identified, agility is important for containing the attack and limiting damage. Advanced NDR solutions offer automated responses to prevent the spread of ransomware over the network.
- Immediate Endpoint Isolation: If a compromised endpoint is found, NDR can disable network connectivity to prevent lateral movement.
- Blocking Malicious Traffic in Real-Time: Suspicious connections to ransomware command-and-control servers can be automatically blocked.
- Security Orchestration & Automated Playbooks: By integrating with SIEM and SOAR platforms, NDR can activate pre-configured incident response workflows, alerting security teams and executing automated mitigations right away.
This automatic isolation feature considerably reduces Mean Time to Detect and Mean Time to Respond, reducing operational downtime.
5. Forensic Analysis for Post-Attack Recovery
Even with proactive defenses, organizations must be prepared for incident response and post-attack recovery. NDR provides comprehensive forensic analysis, helping security teams understand how the attack happened and prevent future breaches. Key forensic capabilities include:
- Attack Path Visualization: Displays a full history of how the ransomware entered the network, moved across it, and what measures were taken.
- Incident Logs & Packet Captures: Security teams can analyze endpoint data and network logs to understand which files were accessed, encrypted, or exfiltrated.
- Post-Breach Threat Hunting: Using historical network activity, NDR allows teams to search for Indicators of Compromise (IoCs), ensuring dormant threats are eradicated.
With real-time threat intelligence and historical network activity analysis, organizations can not only recover faster but fortify defenses against future attacks.
- Comprehensive Visibility
- Rich Metadata from NTA and EDR
- Rise of Deception Defense

Case Studies
1. The MGM Resorts Ransomware Attack (2023)
What Happened?
MGM Resorts International, one of the major hospitality businesses, endured a ransomware attack in September 2023, leading to days of operational interruptions. Customers claimed problems with check-ins, gaming machines, and restaurant reservations, which caused millions in lost revenue.
Who Were the Attackers?
The attack was attributed to ALPHV/BlackCat, a renowned ransomware group known for attacking vulnerabilities in large corporations.
Purpose of the Attack
The goal was to disrupt business operations and demand a multi-million-dollar ransom in exchange for decryption keys and preventing data leaks.
How Attackers Exploited Vulnerabilities
- Social engineering via LinkedIn to trick an IT help desk employee into granting access.
- Gaining administrator-level privileges through credential theft.
- Moving laterally across systems, encrypting files, and disrupting key services.
How NDR Could Have Helped
An advanced NDR solution would have:
- Detected abnormal access patterns from the compromised employee’s account.
- Flagged lateral movement across MGM’s network before encryption began.
- Triggered automated responses to isolate affected systems and prevent further spread.
2. The Colonial Pipeline Ransomware Attack (2021)
What Happened?
In May 2021, Colonial Pipeline, a major fuel supplier in the U.S., was hit by a DarkSide ransomware attack, forcing the company to halt fuel distribution across the East Coast for several days.
Who Were the Attackers?
The ransomware was deployed by DarkSide, a cybercriminal group specializing in double extortion tactics—encrypting data and threatening to leak it unless a ransom is paid.
Purpose of the Attack
The attackers demanded approximately $4.4 million in Bitcoin as a ransom. They also planned to exert pressure by cutting crucial gasoline supplies.
How Attackers Exploited Vulnerabilities
- Obtained access by using a VPN account that was compromised and did not have multi-factor authentication (MFA).
- Moved laterally through the network undetected.
- Encrypted key operational systems, forcing Colonial Pipeline to shut down services.
How NDR Could Have Helped
Had Colonial Pipeline used a robust NDR solution, it could have:
- Detected unusual access attempts through its VPN before attackers escalated privileges.
- Identified suspicious data transfers and blocked ransomware execution.
- Automated network segmentation to limit ransomware spread before it reaches critical systems.
Best Practices for Using NDR in a Ransomware Attack Response Plan
-
Deploy NDR for Full Network Visibility
Ensure your NDR solution monitors all traffic, including encrypted traffic, to detect hidden threats.
-
Integrate NDR with Your Security Stack
Combine NDR with SIEM, EDR, and SOAR for comprehensive threat detection and automated response.
-
Implement Proactive Threat Hunting
Use NDR to detect unusual behavior and threats before attackers escalate their operations.
-
Automate Ransomware Containment
Set up NDR-driven response actions, such as:
- Blocking traffic to known ransomware command-and-control servers
- Isolating infected systems automatically
- Alerting SOC teams in real time
-
Train Security Teams on NDR Threat Intelligence
Leverage NDR-generated insights to improve threat response strategies and strengthen network defenses.
How Fidelis Network® Detection and Response Strengthens Ransomware Defense
Fidelis Network® provides an advanced Network Detection and Response (NDR) solution that offers:
- Deep network visibility to detect hidden threats
- Automated threat hunting & anomaly detection
- Real-time attack containment & response
- Lateral movement detection to prevent ransomware spread
- Integration with SIEM and SOAR for rapid incident response
With multi-layered threat detection and automated security workflows, Fidelis Network® empowers organizations to defend against ransomware before it causes damage.
Final Thought
By leveraging NDR for ransomware attack detection and response, organizations can significantly reduce dwell time, stop lateral movement, and protect critical assets from encryption and data theft. In 2025, proactive network defense is no longer optional—it’s essential.
- Deep visibility
- Real-time threat detection
- Automated response

Frequently Ask Questions
How can organizations maximize the effectiveness of NDR in ransomware defense?
- Ensure full network visibility by deploying NDR across all segments.
- Regularly update detection rules and integrate with global threat intelligence.
- Combine NDR with endpoint and cloud security for a multi-layered approach.
- Automate response workflows to contain threats faster.
- Conduct regular incident response drills using NDR insights.
What are the most common indicators of compromise (IoCs) that NDR detects in ransomware attacks?
Some key IoCs that NDR can detect include:
- Unusual data encryption activities across shared network drives.
- Unauthorized access attempts from compromised accounts.
- Communication with known ransomware command-and-control (C2) servers.
- Sudden spikes in outbound traffic, indicating potential data exfiltration.



