Breaking Down the Real Meaning of an XDR Solution
Read More Fidelis’ deception capabilities enable you to deceive attackers and lure them into
Is your XDR solution truly comprehensive? Find Out Now!
Deception technology is the cornerstone of proactive cyber defense. It works by employing active defense, a proactive approach that focuses on understanding and managing threats. Advanced cyber deception plays a crucial role in enhancing the security posture against sophisticated attacks, particularly in real-time detection and containment of ransomware. It allows organizations to mislead, detect, and defeat cyber-attacks, and then quickly return to normal IT operations. The primary purpose of cyber deception is to divert the attacker’s attention away from the actual crowned jewels of your organization. Most importantly, deception technology provides insight into malicious activities that could otherwise evade detection within IT networks.
Deception technology is a sophisticated cybersecurity solution that employs decoys, lures, and other deceptive tactics to detect and thwart cyber threats. By creating a network of fake assets that mimic real ones, this technology misleads attackers, diverting their attention away from genuine targets. This approach enhances threat detection and provides invaluable insights into attacker behavior. As part of a comprehensive cyber defense strategy, deception technology empowers security teams to identify and respond to advanced threats that might otherwise slip through traditional security measures.
Today’s digital adversaries are more sophisticated, and they do significantly more damage to the businesses they impact. Modern cyberattackers also hide deep within digital environments for longer periods of time. This typically gives them plenty of time to study vulnerabilities, and ultimately wreak extreme havoc for unwary organizations.
In Active Deception technology decoys mimic legitimate elements of your IT environment – such as endpoints, network, active directory and IoT – so the intruder believes he is interacting with the real thing. This gives your IT security team the near real-time ability to study an adversary’s behavior and detect, analyze, or defend against zero-day and advanced cyberattacks.
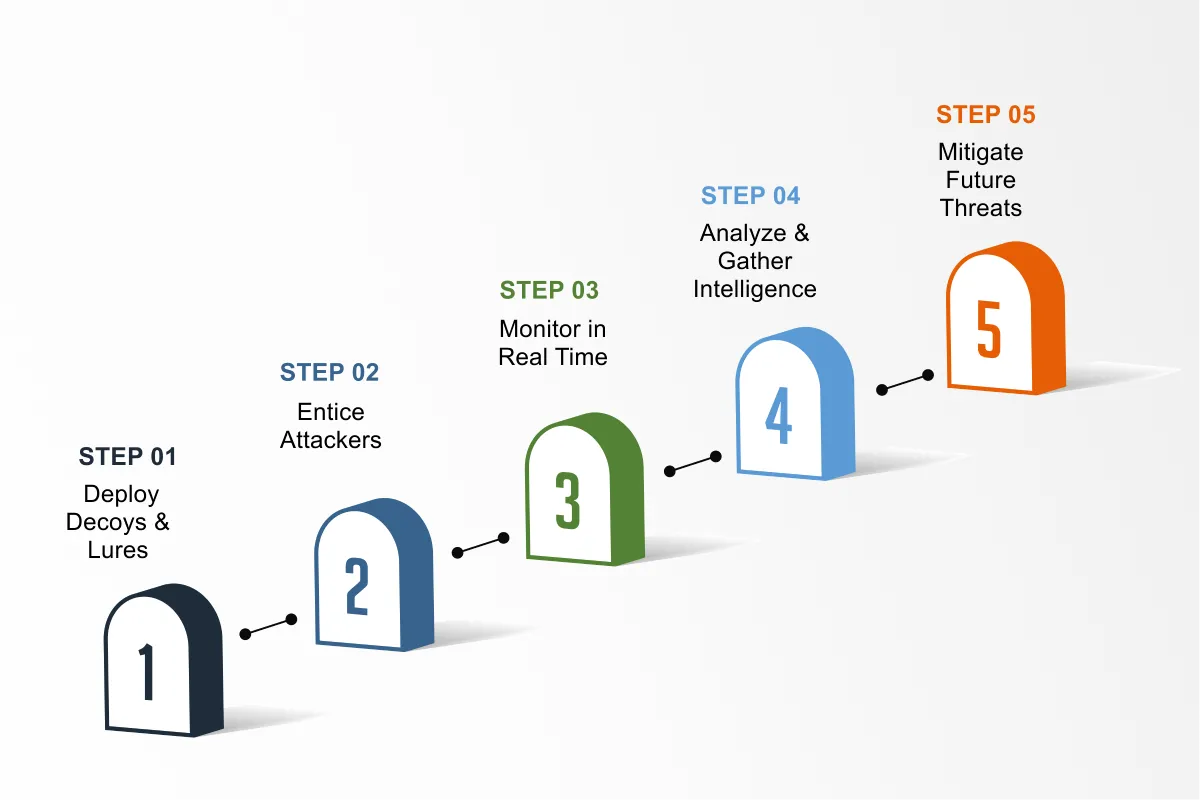
Threat intelligence is a cornerstone of effective deception technology. By leveraging cyber deception technology, security teams gain a deeper understanding of the tactics, techniques, and procedures (TTPs) employed by attackers. This technology provides a wealth of information on attacker behavior, enabling security teams to enhance their threat intelligence and anticipate future threats. The insights gathered from deception technology allow for the creation of internal threat intelligence tailored to the specific needs and threat landscape of the organization. This proactive approach ensures that security teams are not only reacting to threats but are also prepared to counteract new and evolving cyber threats.
Deception technology helps you identify, and block sophisticated digital adversaries before they can damage critical infrastructure and exfiltrate sensitive data.
Your deception platform must:

Deception technology is one of the most powerful add-on cyber defense layers which helps detect threats and anomalous behaviour at various stages of cyber-attacks. The threats that it can help defend include:
Fidelis Deception® enables you to easily reshape the attack surface and lure, detect and defend earlier in the attack lifecycle through active defense.
With Fidelis Deception®, you can automatically deploy traps and lures to slow down, confuse, and stop attackers in their tracks.
With Fidelis Deception® natively integrated into Fidelis Elevate®, the XDR platform, SOC teams can shift to a proactive cyber defense and easily find, deceive, and neutralize advanced cyber threats.
Download the solution brief now to reclaim control and change the rules of engagement by re-shaping the attack surface.
Fidelis Deception® has been combined with EDR and NDR solutions to create Fidelis Elevate, an open active XDR platform.
Our Active XDR platform brings together three powerful cybersecurity technologies to help organizations change the game to their advantage. Fidelis customers can seamlessly create clones of their subnets and assets that can be populated with fake user accounts and directories and then lay down breadcrumbs for anyone who is trying to discover the network and give a warning when an adversary is on the network.
Integrated advanced cyber deception capabilities make it easier to detect, respond, and neutralize sophisticated cyber-attacks while adding cost and complexity to the attacker – making it harder for them to cause damage. Not only can organizations counter current cyberattacks, but they can learn more about their digital adversaries and be prepared for new attacks in the future. Regardless of the tactics or technology adversaries use, Fidelis Deception will always be there to detect threats at various stages of cyber-attacks and lead them away from your assets.
Sometimes cybersecurity hackers use deception. Using IP addresses a malware attack can also recycle IP addresses from other low-profile attacks such as this example. The danger is seen in the form of less frequent attacks.
A cyber deception extension provides compensation to you, for any loss of any money that has occurred as a result of cyber deception committed by your company. This sponsorship may cover losses resulting from the telecommunication fraud.
The main difference between honeypot architectural designs and next-generation methods is that they are more effective at mimicking real-world scenarios compared to other approaches to deceptive practices. Cybercriminals have discovered that honeypots do things differently because their behavior doesn’t match a true regulated environment.
Doron held executive and management roles in cyber security and software development for over 25 years. He serves now as the CTO for the Deception at Fidelis Security. Doron founded TopSpin Security in 2013 building an enhanced architecture providing accurate detection with minimal overhead; he was the CEO of TopSpin Security until the company was acquired by Fidelis Security. Previously he served as Vice President of Products and Engineering at Breach Security acquired by Trustwave defining and developing advanced Web Application Firewall. Before that he had several roles in Motorola Semiconductor Israel including leading the software development for the company.
See Fidelis in action. Learn how our fast and scalable platforms provide full visibility, deep insights, and rapid response to help security teams across the World protect, detect, respond, and neutralize advanced cyber adversaries.