Breaking Down the Real Meaning of an XDR Solution
Read More Learn how to protect your organization from the devastating impact of BlackSuit
Exclusive Webinar: Your NDR is not doing enough! Find out what you need to supercharge it!
Man-in-the-Middle (MITM) attacks continue to be one of the most dangerous cybersecurity threats. These attacks often involve intercepting data transfer between two parties, allowing the attacker to capture sensitive information. These attacks exploit vulnerabilities in communication to intercept, alter, or steal important information.
As organizations increasingly use online communication and cloud services, protecting data from being intercepted is essential. This piece investigates how MITM attacks occur, how they can be prevented, and the role of tools like Fidelis Network® DLP in defending against these threats.
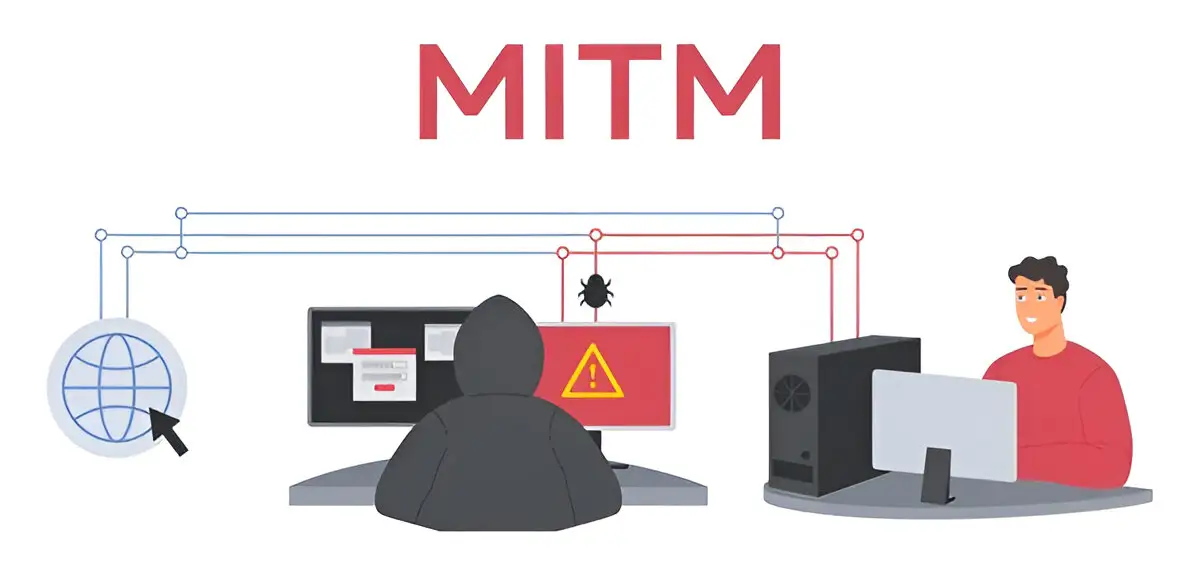
A Man-in-the-Middle (MITM) attack is a complex threat. The attacker intercepts and secretly listens to and alters communication between two parties, without their knowledge. By doing so they access private data like login details, money transfers, and personal info without permission.
An MITM attack works when attackers gain access to vulnerable communication channels. They secretly listen in, decode, and modify sensitive information between two individuals or devices. The attack follows a systematic approach, often involving social engineering and technical manipulation.
MITM attacks can be grouped based on how attackers intercept and alter communication. Understanding the MITM attack types helps organizations find vulnerabilities and mitigate risks better. These attacks are also known as machine in the middle attacks, where the intercepting entity can be a bot, device, or malware.
Attackers set up fake Wi-Fi networks that seem real to trick people into connecting. Once someone connects, the attackers can monitor and collect personal data being transmitted.
Hackers alter DNS records to redirect people to fake websites instead of the real ones. This type of attack often targets the local area network, where DNS records can be manipulated to redirect traffic.
Attackers make people believe they are on a secure website by using fake security certificates. This lets them intercept and decrypt sensitive information through methods like SSL hijacking.
Attackers send falsified ARP messages to associate their media access control (MAC) address with a legitimate IP address. This lets them intercept the data being sent between devices.
Attackers get unauthorized access to email accounts to intercept important messages or modify financial transactions, often capturing login credentials and targeting businesses.
Here hackers take over active session cookies to pretend to be users and get into accounts without needing passwords. This can lead to identity theft, where attackers use stolen session information to impersonate users.
Attackers aim at Voice over IP (VoIP) calls, eavesdropping on conversations or injecting malicious commands.
Each type takes advantage of different vulnerabilities, highlighting the importance of strong security measures and constant monitoring. Attackers may also exploit vulnerabilities in the user’s web browser to intercept data during online transactions.
Early detection of a MITM attack is important for reducing its effects. Here are the ways to recognize an ongoing attack:
Implementing robust endpoint security measures is crucial for early detection and prevention of MITM attacks.
Identifying a Man-in-the-Middle attack involves advanced threat monitoring and immediate alerts, which are key features of Fidelis Network® DLP.

Preventing MITM attacks requires implementing security measures across networks, devices, and user behavior. Here are steps to do so:
Prevention is Better Than Cure
Prevention strategies should be combined with continuous monitoring to ensure that threats are identified before they can cause any damage.
Fidelis Network® DLP is a strong solution designed to fight against complex threats. It does more than just regular DLP tools, providing full protection for sensitive communications. It ensures secure data transfer by monitoring both encrypted and unencrypted communications.
How Fidelis Network® DLP can Help Reduce MITM Risks:
By adding Fidelis Network DLP to their security system, companies can lower the chances of MITM attacks and better protect their sensitive information.
We’ve learned how to spot and stop MITM attacks. Now, let’s see how to clean up if one has already in the system, to reduce the harm. Implementing strong endpoint security measures is essential to prevent future attacks and ensure system integrity.
Steps to Remove a MITM Attack:
Man-in-the-Middle attacks remain a significant issue in cybersecurity. But they can be stopped or at least made less likely by using strong encryption and better security methods.
Fidelis Network DLP provides a complete solution for businesses to detect, prevent, and respond to MITM attacks, keeping sensitive data safe from being interception or altered.
Industries like finance, healthcare, e-commerce, and government sectors are targeted often as they handle sensitive data, making them prime targets for attackers looking to collect personal data. Businesses extensively using online channels for communication and fund transfers are especially at risk.
Domain Name System Security Extensions ensure that DNS records are verified, preventing attackers from redirecting traffic to fake websites through DNS spoofing.
Yes, mobile devices are actually easier to hack because many people connect them to public Wi-Fi, which isn’t very secure.
The time it takes can differ based on how complicated the attack is, and the vulnerabilities exploited. Some attacks can be ready to be executed in just a few minutes, while others can take a lot of preparation and effort for execution.
Sarika, a cybersecurity enthusiast, contributes insightful articles to Fidelis Security, guiding readers through the complexities of digital security with clarity and passion. Beyond her writing, she actively engages in the cybersecurity community, staying informed about emerging trends and technologies to empower individuals and organizations in safeguarding their digital assets.
See Fidelis in action. Learn how our fast and scalable platforms provide full visibility, deep insights, and rapid response to help security teams across the World protect, detect, respond, and neutralize advanced cyber adversaries.