Breaking Down the Real Meaning of an XDR Solution
Read More Discover the five critical components of XDR integration—from data ingestion and filtering
Want to stay ahead of threats in 2025? This research report is all you need to stay updated.
Social engineering involves manipulating people into revealing confidential information or taking risky actions. It’s crucial to understand because it preys on human psychology rather than technical. In this article, we will explain what social engineering is, the tactics attackers use, and how you can protect yourself using advanced solutions like Fidelis Elevate® that provide layered threat detection to counter social engineering attacks before they cause damage.
Social engineering is the manipulation of humans to gain access to sensitive information. Cybercriminals utilize complex methods, including psychological manipulation and exploiting trust, to carry out social engineering attacks. Unlike traditional hacking, which targets software vulnerabilities, social engineering exploits human behavior to achieve its goals.
At its core, social engineering attacks play on emotions and instincts. Attackers may create a sense of urgency or fear, compelling victims to act rashly and divulge confidential information or perform actions they would normally avoid. Most social engineering attacks target the computer user by exploiting trust and psychological triggers. This manipulation to trick users is what makes social engineering particularly dangerous and effective.
There are various types of social engineering, each employing different tactics to achieve the same end: gaining private information or access. Attackers often aim to compromise a computer system or gain access to sensitive data. Recognizing this type of social engineering helps to identify potential threats and take necessary precautions to safeguard yourself. Most social engineering attacks follow recognizable patterns, making it important to understand their common traits.
Note: Fidelis Network® detects unusual user behavior and anomalies that signal social engineering attempts.

Social engineering is one of the most effective tools used by cyber attackers because it targets human behavior rather than technical flaws. Instead of hacking into systems directly, attackers manipulate people into revealing sensitive information or bypassing security measures.
These attacks often use tactics such as phishing emails, spear phishing, and pretexting. They typically start with research: attackers gather background information about their targets to craft convincing messages or scenarios. This preparation makes victims more likely to fall for the trap.
The main goal of social engineering is to trick individuals into:
Because these attacks exploit human error, they are often unpredictable and hard to detect with traditional security tools. Attackers use psychological tricks to gain trust, pushing victims to break security rules without realizing it.
Social engineering is often paired with other types of cyber attacks for greater impact. For instance, a phishing email might steal login credentials that are later used to compromise an entire network.
The best defense? Security awareness training. Teaching employees how to spot suspicious emails, requests, or links greatly reduces the chances of falling victim to these attacks. Strengthening the human element is one of the most effective ways to protect sensitive information.
But the training is not foolproof, hence experts recommend Fidelis Elevate® as it helps close gaps left by traditional security tools by correlating signals across endpoints, network, and cloud.
Many cyber-attacks begin with social engineering—tactics that exploit human emotions and trust rather than technical flaws. Techniques like phishing, baiting, and pretexting are designed to manipulate individuals into revealing sensitive information, granting access to systems, or downloading malicious software.
These attacks are effective because they tap into powerful emotions like fear, urgency, curiosity, or the promise of reward, prompting victims to act quickly and without thinking. Attackers often conduct thorough background research on their targets, using personal and organizational details to make their schemes more believable.
Below are some of the most common social engineering techniques:
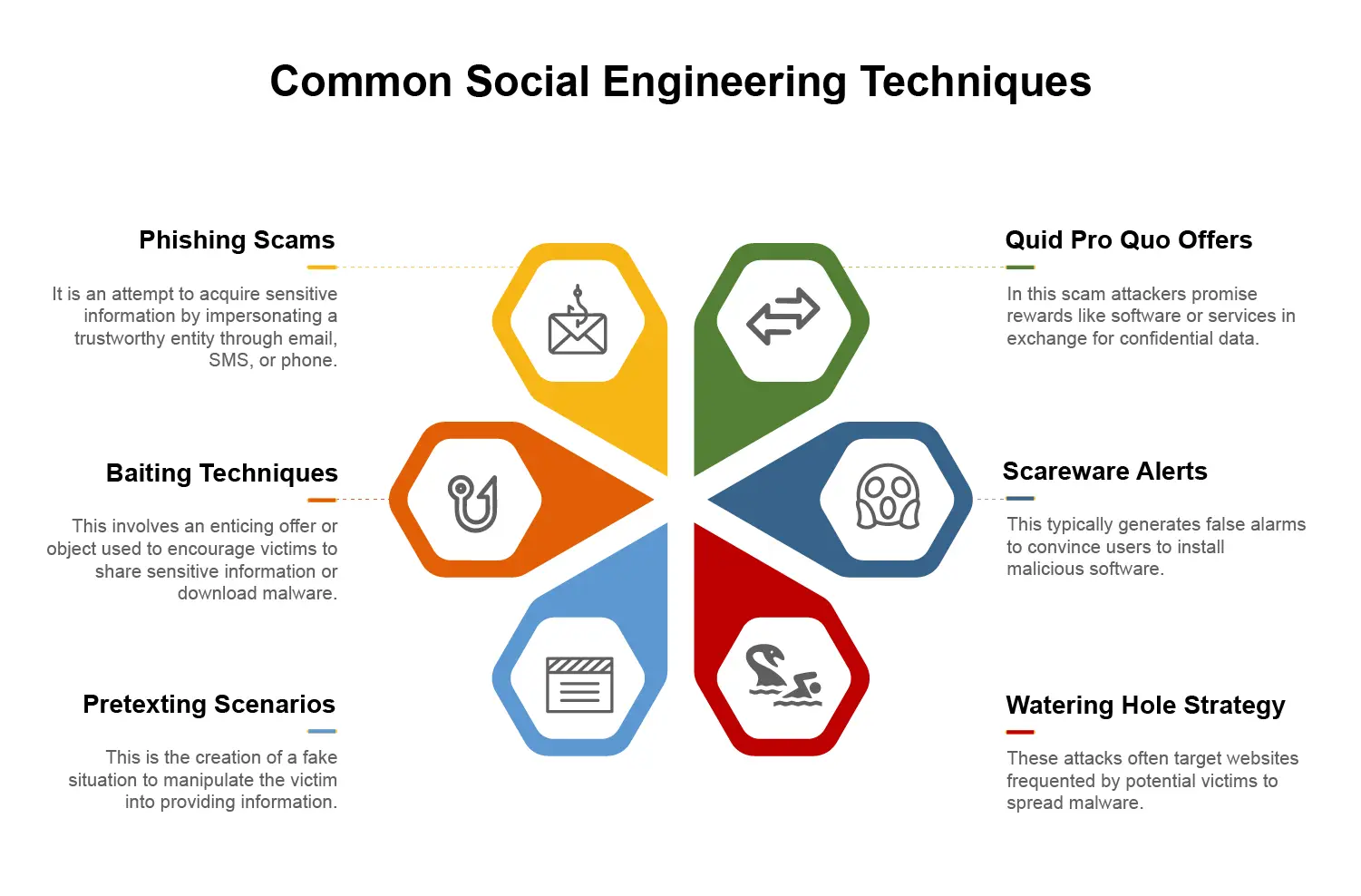
Phishing involves impersonating a trusted entity through email, SMS, or phone to steal sensitive data like credentials or financial details.
These scams can lead to identity theft, account compromise, and major financial loss. Fidelis Email Security and Fidelis Network® can identify and stop phishing emails in real time, even highly targeted ones.
Baiting lures victims with an enticing offer—free software, exclusive content, or a “must-have” item—leading them to download malware or share confidential information.
Curiosity and the allure of “free” are the hooks that make baiting effective.
Pretexting involves creating a fake scenario or false identity to manipulate victims into divulging information.
This tactic is frequently a stepping stone to larger attacks. But there is a catch, Fidelis Deception® can trick attackers into revealing themselves before they reach critical systems.
In quid pro quo scams, attackers offer a service or benefit—such as free software or tech support—in exchange for sensitive data. Victims believe they’re getting help or a reward but end up handing over valuable information.
Scareware uses fake security alerts to create panic. Victims are prompted to install “urgent updates” or “antivirus tools” that are actually malware.
Attackers compromise websites frequently visited by their targets, infecting them with malware.
Regular patching and monitoring are essential to reduce the risk.
Each of these techniques preys on human trust, fear, curiosity, or complacency. By bypassing technical defenses and targeting people directly, social engineering attacks remain one of the most challenging cyber threats to stop.
Pro Tip: Security awareness training, multi-factor authentication, and automated threat detection solutions are essential to identifying and stopping social engineering attacks before they succeed.

Human emotions are at the heart of social engineering attacks, as threat actors rely on psychological manipulation to convince victims to take actions that compromise security. Social engineers are adept at creating a sense of urgency, fear, or curiosity, prompting individuals to reveal sensitive information or perform a critical task without fully considering the consequences. For instance, a phishing attack might warn that a victim’s account has been compromised, urging them to provide their login credentials immediately to regain access. Similarly, a quid pro quo attack may offer a tempting reward in exchange for confidential data, such as credit card details or phone records.
Attackers often target individuals who are more susceptible to emotional manipulation, such as those under stress or facing tight deadlines. Social engineers may also use social proof—like fake testimonials or endorsements—to build trust and credibility, making their scams even more convincing. By exploiting these human emotions, social engineering attacks can lead to the exposure of sensitive information, unauthorized access to computer systems, and significant financial loss.
These tactics are not limited to the digital world; in the physical world, social engineers may use pretexting or tailgating to gain access to secure facilities or computer systems. In the digital realm, phishing emails and malicious websites are common tools used to trick victims into revealing sensitive information. Recognizing how human emotions are manipulated in social engineering attacks is crucial for developing effective security awareness training. By educating users to identify fictitious threats, false promises, and other psychological ploys, organizations can empower their teams to resist manipulation and protect confidential data from cyber threats.
Social engineering involves deceptive tactics to manipulate individuals into divulging confidential information. These attacks rely on human interaction rather than exploiting software vulnerabilities. One warning sign of a social engineering attack is an email originating from a spoofed or incorrect domain. Threat actors often conduct targeted attacks against specific individuals or organizations, carefully planning their approach to maximize the chances of success.
Heightened emotions like fear, urgency, and curiosity are exploited by attackers in social engineering attacks. Trust is essential as attackers create believable narratives to deceive victims. A targeted victim may be chosen based on their likelihood to respond to manipulation. By building rapport and establishing trust, they prompt security breaches that would not occur under normal circumstances.
Awareness of social engineering tactics is crucial for effective prevention. Identifying common traits like requests for sensitive information through insecure channels helps in swiftly recognizing potential targets. Weak security protocols are often exploited by social engineers to bypass defenses.
| Aspect | Social Engineering | Phishing |
|---|---|---|
| Definition | A broad category of attacks that manipulate people into revealing information or breaking security rules. | A specific type of social engineering attack where attackers use fake emails, messages, or websites to steal data. |
| Scope | It encompasses multiple techniques such as pretexting, baiting, quid pro quo, and phishing. | One technique under the larger umbrella of social engineering. |
| Method | Uses various psychological tactics and scenarios, including face-to-face or digital interactions. | Primarily conducted through digital communications like email, SMS, or fake websites. |
| Goal | To manipulate the victim into disclosing sensitive information or performing an action that compromises security. | To trick victims into clicking malicious links, entering credentials, or downloading malware. |
| Examples | Pretexting, baiting with infected USBs, scareware, tailgating. | Email scams, SMS phishing (smishing), voice phishing (vishing), spear phishing. |
Different social engineering techniques can include impersonation or creating false scenarios to elicit desired actions from victims. For instance, watering hole attacks infect popular webpages, targeting visitors to those sites. The consequences can include stolen credentials and drive-by ransomware downloads.
Understanding these examples highlights the diverse methods social engineers use to exploit human error. Let’s take a closer look at two specific types of social engineering attacks: malware delivery channels and in-person deception.
Read related blog: Leading Reasons for Data Loss: Social Engineering and Insider Threats
Phishing scams include several types such as bulk phishing, spear phishing, and business email compromise, often leading to malware infections. Baiting techniques commonly deliver malware using physical media like infected flash drives or enticing online advertisements. Scareware is commonly distributed through spam emails and popup banners featuring eye-catching or intriguing wording to manipulate users. Delivery methods, such as emails and P2P networks, can allow malware to bypass antivirus filters, representing key general vulnerabilities.
Physical breach attacks are assaults where perpetrators pose as legitimate individuals to gain unauthorized access. Attackers aim for a highly valuable reward if successful in conducting physical breach attacks. During access tailgating, attackers use social courtesy or pretend to be authorized to manipulate people. Perpetrators may pose as representatives of trusted vendors or recently fired employees. These tactics exploit human interaction and social norms to gain entry into secure areas. Recognizing these traits helps prevent unauthorized access and security breaches.
To effectively protect yourself from social engineering attacks, adopt safe communication practices, secure your networks and devices, and remain vigilant by recognizing common tactics and warning signs. This proactive approach is essential for your safety.
Proactive privacy and security practices are essential in preventing social engineering attacks. Raising user awareness and regularly monitoring for unusual activity can encourage users to detect potential breaches early.
Proactive privacy and security measures are essential in preventing social engineering attacks. Raising user awareness and monitoring for unusual activity can help identify threats early and reduce the risk of breaches.
Using firewalls and advanced detection tools helps block unauthorized access and create stronger security across networks and systems.
Always verify identities using a secondary channel, avoid using public Wi-Fi for sensitive communications, and manually type URLs into your browser instead of clicking on links. These habits reduce the chances of falling victim to phishing and other social engineering tactics.
Use guest Wi-Fi to isolate devices, enable VPNs for secure data transmission, encrypt sensitive information, and regularly update all network-connected devices to close vulnerabilities.
Fidelis Network® can help secure your network from social engineering attempts and other threats. It enables faster detection, complete contextual visibility, and reduces alert fatigue for security teams.
Keeping software updated provides essential security fixes and closes vulnerabilities. Without comprehensive security software, users are likely exposing themselves to malware infections. Comprehensive security software helps detect and remove threats before they can compromise devices. Using unique and complex passwords is crucial for securing online accounts. Always lock devices and keep them with you to prevent unauthorized access. Multi-factor authentication adds an additional layer of security to online accounts.

Self-awareness helps in recognizing manipulation tactics and defending against social engineering. Slowing down and thinking critically before acting, along with regular employee testing through simulated attacks, enhances vigilance.
Combining self-awareness and critical thinking effectively equips individuals to identify and resist social engineering attempts. By staying alert and cautious, you can prevent falling victim to these deceptive tactics.
Social engineering attacks rely on psychological manipulation to trick individuals into revealing sensitive information. Understanding the various tactics such as phishing, baiting, pretexting, quid pro quo, scareware, and watering hole strategies is critical to recognizing and preventing these attacks.
While user awareness and safe communication practices are essential, relying on manual defenses alone isn’t enough. Fidelis Elevate® strengthens your security posture by unifying NDR, EDR, and deception technologies, giving you the contextual visibility and automated detection you need to stop social engineering attempts before they succeed.
By combining employee training with the advanced capabilities of Fidelis Network® and Fidelis Elevate®, organizations can close security gaps, accelerate response, and reduce the risk of costly breaches.
Social engineering involves manipulating individuals to obtain sensitive information by exploiting psychological tactics. It emphasizes the human element in security breaches, rather than relying solely on technical vulnerabilities.
Reverse social engineering is a tactic where attackers position themselves as trusted helpers. They create a problem for the victim and then offer a solution, tricking the victim into revealing sensitive information or granting access.
To recognize a social engineering attack, watch for warning signs like emails from unfamiliar domains, requests for sensitive information via insecure methods, and communications that instill a sense of urgency or fear. Being vigilant about these indicators is crucial for your online security.
Common types of social engineering attacks include phishing, baiting, pretexting, quid pro quo, scareware, and watering hole attacks. Being aware of these tactics is essential for protecting yourself and your organization from potential threats.
Some advanced attacks target biometric authentication by using forged fingerprints, facial recognition spoofs, or voice recordings. These attacks bypass security systems that rely solely on biometric data.
To effectively protect yourself from social engineering attacks, adopt safe communication practices, secure your networks and devices, and remain vigilant by recognizing common tactics and warning signs. This proactive approach is essential for your safety.
If you suspect a social engineering attempt, take immediate action by verifying the sender’s identity through a secondary channel and refraining from clicking on any suspicious links or sharing sensitive information. Trust your instincts and prioritize your security.
Effective training includes simulated phishing exercises, awareness workshops, and regular refresher to teach employees how to spot suspicious requests and prevent breaches.
See why security teams trust Fidelis to:
Neeraja, a journalist turned tech writer, creates compelling cybersecurity articles for Fidelis Security to help readers stay ahead in the world of cyber threats and defences. Her curiosity & ability to capture the pulse of any space has landed her in the world of cybersecurity.
See Fidelis in action. Learn how our fast and scalable platforms provide full visibility, deep insights, and rapid response to help security teams across the World protect, detect, respond, and neutralize advanced cyber adversaries.