Breaking Down the Real Meaning of an XDR Solution
Read More Discover enterprise data loss prevention best practices to protect sensitive data, reduce
Want to stay ahead of threats in 2025? This research report is all you need to stay updated.
A denial of service attack, commonly known as DoS, floods a system with too many requests, making it unavailable to users. This raises the question, what is denial of service, and how can it disrupt services and cause significant damage? By overwhelming the system, attackers aim to exploit weaknesses and create chaos.
Denial of service attacks are a formidable weapon in the arsenal of cybercriminals. These attacks aim to make a machine or network resource unavailable by flooding it with excessive requests, ultimately disrupting services. The primary goal is to overwhelm the target’s finite resources, rendering it unresponsive to legitimate users.
Denial of service attacks are versatile and adaptable, often used in modern cyber operations to blind, delay, or coerce targets in a teardrop attacks cyber attack.
They can target a targeted system, including:
These attacks are noisy by nature, making them an effective tool for distracting, delaying, or degrading responses during amplification attack adversary campaigns.
Grasping the concept of denial of service attacks involves understanding the definitions and differences between DoS and DDoS attacks, the motivations behind them, and their key distinctions.
A Denial of Service (DoS) attack is an attempt to overwhelm a system or process with excessive requests, exhausting its resources and leading to service unavailability.
On the other hand, a Distributed Denial of Service (DDoS) attack utilizes multiple compromised systems or botnets to launch an attack from several sources simultaneously, making it more complex and harder to trace.
DoS attacks can be driven by various motivations. Some aim for disruption, while others serve as diversions to mask other malicious activities. Modern DoS attacks often prioritize economic and operational disruption, targeting industries such as gaming and finance, which rely heavily on perceived reliability.
Financial gain, extortion, and blackmail are common motivations behind DDoS attacks. Some perpetrators launch these attacks as a form of revenge or to inflict additional harm after data exfiltration. Understanding these motivations helps organizations anticipate and prepare for potential threats.
The main difference between DoS and DDoS attacks lies in scale and execution. DoS attacks are executed from a single source, while DDoS attacks originate from multiple sources, making them more complex and harder to mitigate.
Both types of attacks can exhaust system resources by sending http requests that exploit vulnerabilities in the target system’s handling of connections.
Denial of service attacks can be categorized into three main types: volumetric attacks, protocol-based attacks, and application layer attacks. Each type targets different layers of the network, employing unique techniques to disrupt services.
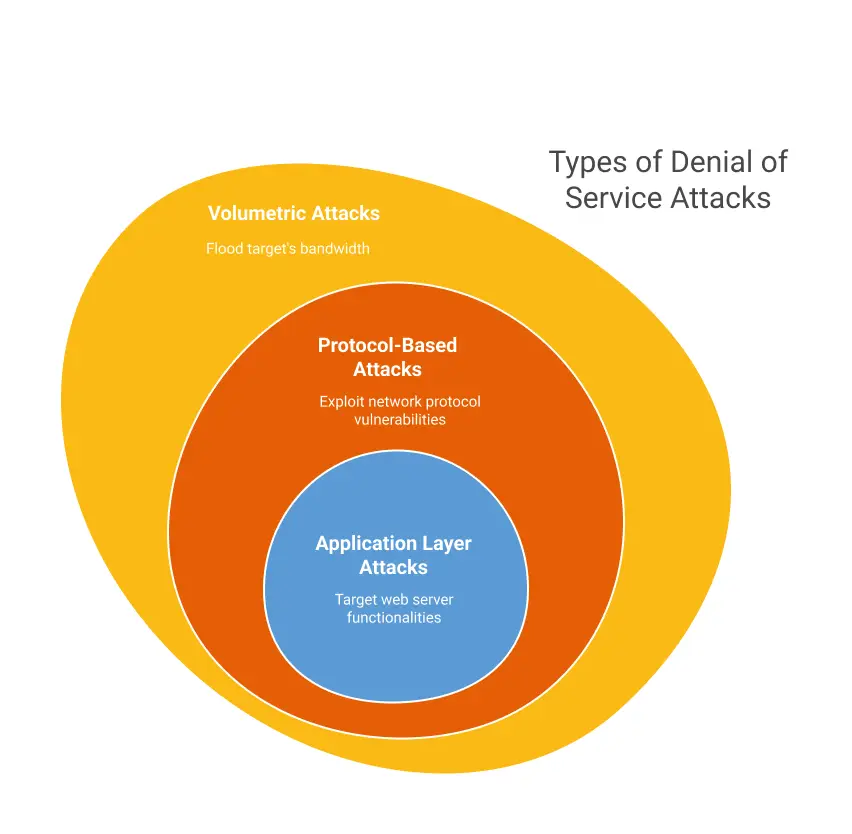
Volumetric attacks flood the target’s bandwidth, utilizing techniques such as DNS amplification and UDP floods. Protocol-based attacks exploit weaknesses in network protocols, with examples like SYN floods and ICMP floods. Application layer attacks specifically target web server functionalities, including HTTP floods and SQL injections.
Volumetric attacks are the most common type of DDoS attack, aimed at overwhelming the target’s bandwidth. These attacks often utilize amplification techniques to create high traffic volumes, such as DNS amplification attacks and UDP floods.
The Mirai botnet is a notable example of a volumetric attack, leveraging unsecured IoT devices to execute large-scale assaults.
Protocol attacks aim to disrupt services by exploiting vulnerabilities in internet protocol, which can exhaust server resources. Common examples include SYN floods, which flood a target with TCP/SYN packets, and transmission control protocol ping of death attacks, which send malformed ping packets to crash vulnerable systems. When a protocol attack occurs, it can significantly impact the performance of targeted systems.
Application layer attacks specifically target web server functionalities, with examples including SQL injections and HTTP floods. These attacks can manipulate API queries to exploit security vulnerabilities in REST and GraphQL APIs, leading to an application layer attack.
Key sectors targeted by application layer DDoS attacks include banking, SaaS, e-commerce, healthcare, and critical infrastructure.
Denial of Service (DoS) attacks aim to make a service unavailable by overwhelming it with requests or exploiting weaknesses in protocols to disrupt services. Attackers typically use flooding techniques, generating excessive traffic, or they exploit vulnerabilities in the target system’s handling of connections.
Factors influencing the selection of targets in DoS attacks include the organization’s technical exposure, operational dependability on uptime, and its public reputation. Exploring resource exhaustion techniques, network traffic manipulation, and reconnaissance reveals how these attacks work.
Resource exhaustion techniques aim to overwhelm server and network resources, disrupting services. Attackers conduct detailed assessments of a target’s infrastructure to identify vulnerabilities for resource exhaustion.
For instance, during a SYN flood attack, servers become flooded with connection requests, exhausting their resources during flood attacks.
Traffic flooding is a common technique in DoS attacks, where attackers generate excessive packet traffic to overwhelm target systems. Spoofed packets, which are commonly used in these attacks, mislead the target server, making it difficult to differentiate legitimate traffic from malicious requests.
This significantly complicates the detection and mitigation of DoS attacks, posing serious risks to network security.
Target reconnaissance is the first step attackers take when planning a DoS attack to identify vulnerabilities. By identifying weak points in the target’s infrastructure, attackers can successfully execute a DoS attack.
Denial-of-service attacks can lead to significant financial, operational, and reputational damage to organizations. These attacks can render services inaccessible to legitimate users by overwhelming the target with illegitimate traffic. A successful DoS attack results in degraded or halted availability of the target service.
Industries with high availability requirements are most targeted by denial-of-service attacks, leading to reputational damage due to service unavailability. Exploring operational disruption, reputational damage, and financial costs helps in understanding the full impact.
An hour of downtime for critical business applications can cost organizations over $67,000 in lost productivity. Resource exhaustion attacks aim to consume all available resources on a target, leading to performance degradation or complete service shutdown.
For example, the DDoS attack on HSBC in November 2023 led to mobile banking and web access downtime, causing significant disruption to their business operations.
The reputation of organizations can suffer significantly if they are unable to ensure consistent service availability during an attack. Customer churn can occur as individuals seek more reliable service providers during and after a DDoS incident.
The DDoS attack on HSBC highlighted customer churn due to perceived unreliability.
In the US, denial-of-service attacks are considered a federal crime and can result in severe legal repercussions, including prison time. Around 80% of countries have enacted laws addressing cybercrime, including denial-of-service attacks, which could involve administrative and legal costs for organizations.
The operational costs of mitigating a DoS attack may include issues such as failed autoscaling, exhausted thread pools, and overloaded load balancers, which can disrupt service delivery.
Effective detection of DoS attacks relies on correlating traffic data with behavioral patterns and system performance metrics. Continuous monitoring helps in early detection of DoS attacks, potentially preventing escalation. Recognizing unusual network activity, such as spikes in traffic or multiple IP addresses, can indicate a DDoS attack.
Application layer attacks are often harder to detect because they mimic normal user behavior, making them blend into legitimate traffic. Continuous monitoring of network traffic is essential for identifying and mitigating potential DDoS attacks.
Indicators of volumetric attacks at the network level include sudden traffic spikes from various IPs, low connection completion rates, excessive small-packet floods, and malformed headers in DNS, NTP, or HTTP network packets. Tools like NetFlow, sFlow, or VPC Flow Logs can reveal surges in inbound packets during DoS attacks.
Attackers often use statistical methods to analyze incoming requests, allowing them to detect anomalies that indicate a potential DDoS attack.
Indicators of a DoS attack can include elevated CPU usage, dropped packets, and increased error rates across services. Common system-level effects of a DoS attack include high CPU usage, memory allocation failures, thread pool starvation, connection limits, queue backlogs, and timeout thresholds.
High CPU usage and increased error rates may signal an ongoing Denial of Service attack.
DDoS mitigation systems utilize entropy analysis of source IPs and TTL values. This method helps in identifying spoofed traffic. Monitoring tools and techniques are crucial for early detection and prevention of DoS attacks.
Early detection through monitoring enables organizations to respond swiftly to mitigate the impact of DoS attacks.
Uncover how modern network detection empowers faster response to DDoS threats.
While volumetric attacks often dominate the headlines, today’s DDoS campaigns are increasingly multi-layered—mixing protocol abuse with lateral movement or acting as smokescreens for deeper intrusions. Solutions like Fidelis Network provide the advanced visibility needed to detect such complex attack patterns by correlating behaviors across encrypted traffic, cloud assets, and internal systems. At the same time, Fidelis Deception helps expose adversaries who attempt to move laterally or recon the environment post-flood—by leading them into decoys and fake credentials that reveal their tactics early. Together, these tools help defenders detect, divert, and dissect DDoS operations before they escalate.

A layered defense strategy is essential to effectively counteract DDoS attacks. Implement scalable and resilient multilayered DDoS protection solutions to strengthen defenses. Managed security services can adapt to evolving attack vectors, enhancing the overall resilience of an organization’s network.
Integrating third-party DDoS protection can provide an additional layer of defense and complement existing security measures.
Rate limiting refers to restrictions on the number of requests from a specific IP address within a timeframe. Adaptive throttling can lower limits in real time during an attack based on IP reputation, enhancing DoS mitigation.
Effective rate limiting techniques include burst ceilings and token-bucket algorithms tuned against production baselines.
Web Application Firewalls (WAFs) are essential for filtering out malicious traffic and defending against application layer attacks. WAFs act as a reverse proxy to manage and filter incoming traffic.
Blackhole routing is a last-resort technique that discards all incoming traffic directed at a targeted IP. The purpose of blackhole routing is to prevent further network congestion caused by overwhelming traffic during a DDoS attack.
Blackhole routing should be used as a last resort when other mitigation techniques have failed.
Organizations should treat Denial-of-Service incidents as an engineering and coordination problem. A response plan must include steps to confirm an attack, understand its nature, deploy mitigations, monitor the situation, and recover. Effective communication and coordination among response teams are critical during the incident response process.
Post-attack recovery plans should include analyzing the effectiveness of the response and improving future defenses.
The first task in response to a DoS attack is to isolate the source and reduce impact. If extortion is involved in a DoS attack, engage executive and legal counsel and consider notifying law enforcement.
In case the attack is directed at a specific IP or service, reroute the traffic. Additionally, you can activate upstream scrubbing services through a mitigation provider. Quickly apply rate limits and geo-blocking. Make adjustments to ACLs to filter out malicious traffic during an attack.
See how active deception changes the DDoS playbook in your favor.
Stakeholder communication should include establishing clear contacts, intervention thresholds, and understanding available support before a DoS emergency. DoS events should be treated by incident teams as active intrusions, emphasizing the need for urgent and efficient responses.
Communication with stakeholders is crucial in minimizing confusion and ensuring that everyone is informed during a DoS attack, highlighting the importance of efficient communication.
Conducting a thorough analysis after a DDoS attack helps in understanding vulnerabilities and improving future defenses. Debriefing all involved teams and updating the runbook is essential for better preparedness in future incidents.
Activating predefined communication protocols and providing status updates to customer-facing services during a DDoS attack is recommended.
Utilizing professional DDoS protection services can significantly enhance an organization’s resilience against cyber threats. Organizations should assess their specific needs and threat exposure before selecting DDoS protection services.
Engaging with managed security service providers can provide continuous monitoring, rapid incident response, and access to specialized expertise in DDoS mitigation.
When selecting a DDoS protection provider, consider their experience with similar industries and specific compliance requirements.
Providers that offer comprehensive service level agreements (SLAs) can ensure accountability and performance benchmarks.
Managed security providers offer expertise, advanced technologies, and 24/7 monitoring to defend against DDoS attacks. Cloud-based DDoS mitigation solutions facilitate quicker response times and can manage high network bandwidth effectively.
Outsourcing to managed security service providers allows organizations to leverage advanced security tools without the overhead of maintaining an in-house team.
Integrating third-party DDoS protection solutions enhances the security posture of organizations, providing layered defense against attacks. When selecting a DDoS protection service provider, it is essential to consider factors like service reliability, scalability, and customer support.
Managed security services offer benefits such as continuous monitoring, rapid incident response, and access to specialized expertise in DDoS mitigation.
Denial of Service attacks pose a significant threat to organizations, causing financial, operational, and reputational damage. Understanding the types of attacks, how they work, and their impact is crucial for effective mitigation. By implementing robust detection and response strategies, engaging with professional DDoS protection services, and continuously improving defenses, organizations can enhance their resilience against these cyber threats. Stay vigilant, stay prepared, and fortify your defenses against the ever-evolving landscape of denial of service attacks.
The primary goal of a denial of service attack is to make a target inaccessible to legitimate users by overwhelming it with excessive requests. This effectively disrupts its normal functioning.
DoS attacks originate from a single source, whereas DDoS attacks leverage multiple compromised systems or botnets, increasing their complexity and making them more difficult to mitigate.
Common types of denial of service attacks include volumetric attacks, protocol-based attacks, and application layer attacks. Understanding these categories is crucial for effective cybersecurity measures.
Organizations can effectively detect a denial of service attack by closely monitoring for unusual network activity, including traffic spikes, elevated CPU usage, and increased error rates. This vigilance allows for timely responses to mitigate the impact.
To effectively counter denial of service attacks, implementing rate limiting, utilizing web application firewalls, and considering blackhole routing as a last resort are recommended strategies. These measures can significantly enhance your network’s resilience against such threats.
Sarika, a cybersecurity enthusiast, contributes insightful articles to Fidelis Security, guiding readers through the complexities of digital security with clarity and passion. Beyond her writing, she actively engages in the cybersecurity community, staying informed about emerging trends and technologies to empower individuals and organizations in safeguarding their digital assets.
See Fidelis in action. Learn how our fast and scalable platforms provide full visibility, deep insights, and rapid response to help security teams across the World protect, detect, respond, and neutralize advanced cyber adversaries.