Healthcare networks are facing increased pressure to not only secure patient data but also sustain critical patient services. Unfortunately, this industry has become a major target for cybercriminals.
In one breach, healthcare facilities face costly ransom demands, regulatory fines, and an enormous hit to patient trust.
As you can see from the graph below, the number of healthcare data breaches has been steadily on the rise for ten years. In fact, in 2015, 112 million records were compromised primarily by giant breaches at 3 major companies. Such an astounding year, however, has been outdone even by the recent ransomware attack in 2024 on a well-known healthcare company, compromising the sensitive health information of 100 million individuals.
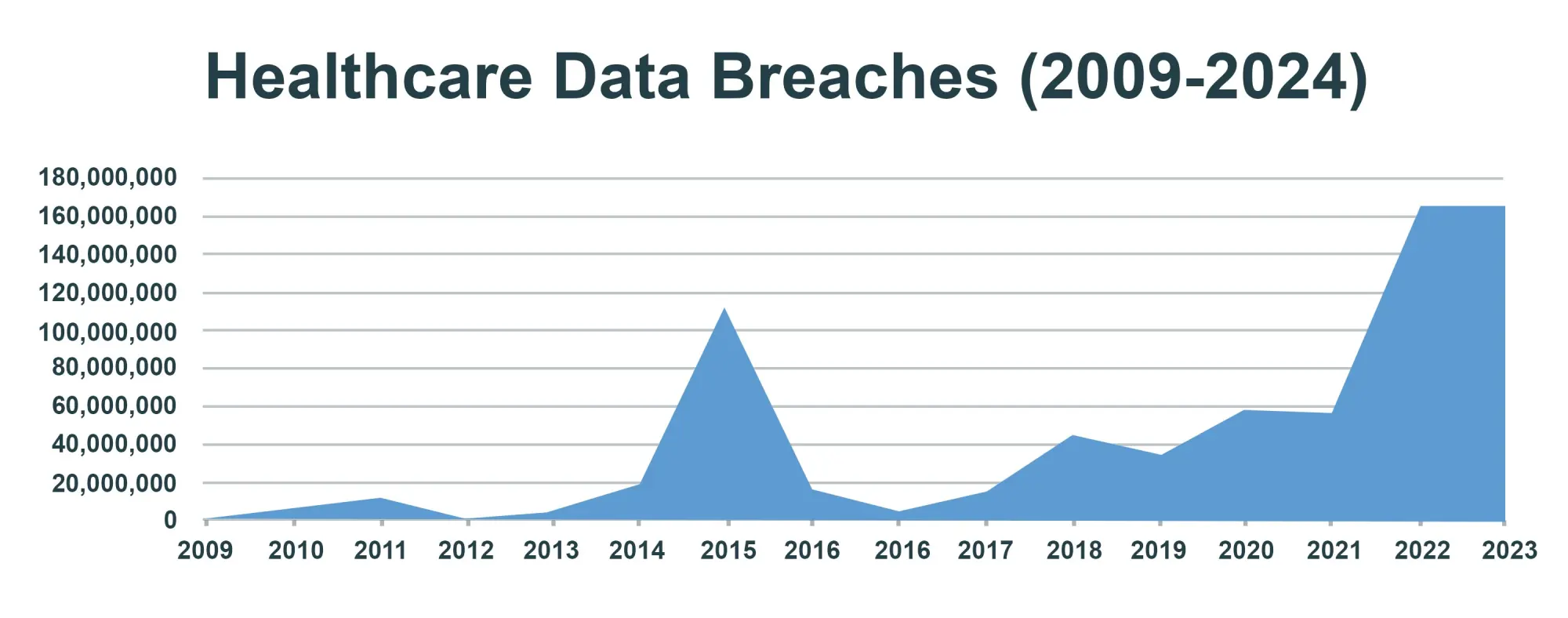
This is particularly disconcerting, thus requiring even more robust cybersecurity measures to secure our most sensitive data.
Why Healthcare is a Top Target for Cybercriminals?
Healthcare facilities are some of the most attractive because they possess extremely valuable information. Hackers have taken advantage of patients’ protected health information, financial accounts, and even intellectual properties that have to do with research on medicines.
The cyber attackers make away with this information that usually fetches up to 10 times as much as stolen credit card numbers in the dark web. And the economic costs of healthcare breaches are not restricted to ransom demands; resolving health-care breaches is expensive.
The 2023 IBM Cost of a Data Breach report says that in healthcare, the average cost to fix a breach is about $10.1 million. This amount is nearly three times higher than the average cost in other sectors.
Why is cybersecurity important in healthcare?
- Because 79% of healthcare organizations experienced a cyber incident during 2023, which was mostly ransomware according to Sophos.
- One in four data breaches in healthcare causes immediate harm. This harm can include delayed treatments, complications, and even death.
This shows how important it is for healthcare providers to strengthen their security. This security should focus on data and ensure continuous patient safety.
Is Cybersecurity the Same as Patient Safety?
Healthcare environments need to be “cyber-healthy.” This is just as important as having infection control and safety protocols.
A strong use of healthcare cybersecurity best practices will keep data safe. It will also help protect patients from the serious effects of a cyberattack.
A recent study by the Ponemon Institute found that nearly 25% of health care organizations reported more deaths. This increase is due to ransomware and other attacks that delay patient care.
There are some well-known examples of breaches that show how cybersecurity incidents can affect sensitive patient healthcare data. These breaches violate the Health Insurance Portability and Accountability Act (HIPAA) rules that protect patient confidentiality.
These incidents led to major financial losses, costing millions of dollars. They can harm reputations, disrupt business operations, and create lasting effects for individuals and healthcare organizations.
Why aren’t healthcare organizations prioritizing cybersecurity?
There are several reasons why cybersecurity is often overlooked in healthcare:

Scarce resources: Often, healthcare organizations don’t have the funding and staff to allocate for cybersecurity, so they prioritize patient care and operation expenditures.
- Lack of understanding: It is common for healthcare companies to underestimate the importance of cybersecurity, or the risks involved with cyberattacks. They might think their IT systems are safe. They could also hire a third party for security, which needs fewer resources.
- Data intricacy: Healthcare organizations deal with large amounts of sensitive patient data, spread across several locations and parties. Plus, systems are often a mix of legacy and modern, on-premises and cloud. The inherent complexity makes it challenging to identify and address potential vulnerabilities.
- Multiple disparate stakeholders: The Healthcare industry involves many different stakeholders, from medical providers in hospitals and clinics to insurance providers, pharmacies, and government agencies. PII is often shared among this disparate network, but it is nearly impossible to ensure all stakeholders have taken consistent and appropriate measures to protect the data.
- Compliance and regulations: While there are regulations in place to protect patient data (e.g., HIPAA in the United States), they are not designed to address the full scope of potential cybersecurity risks.
4 Major Cybersecurity Strategies to Secure Patients
Dedicated Cybersecurity Teams
Dedicated cybersecurity teams monitor the health systems day and night, with constant observation of health systems that violate any threats of cybersecurity threats in healthcare. These teams scrutinize the entire impacts on the attack surface and take immediate responses to any cyber risks that might endanger the safety of patients and protected health information (PHI).
Education on Cyber Hygiene for the Staff
Cyber hygiene education empowers the staff to be aware of health information threats such as phishing and ransomware attacks among others. Regular training cuts security breaches in healthcare organizations by 40%. It helps staff know who the threat actors are. Training makes them aware of these threats and teaches best practices to reduce risks. For example, using multi-factor authentication and reporting incidents can help.
Scanning for vulnerabilities
Regular scans of IoMT and all health-related devices help find and fix weaknesses quickly. That way, all cyber risk is covered. It tries to protect hackers from known vulnerabilities in systems and on medical devices from being breached within the sector.
Network Segmentation
The critical systems within the network are separated. If a cyber-criminal gets into one part of the health network, they cannot access patient-critical devices. They also cannot reach sensitive protected health information (PHI). This helps reduce the impact on healthcare institutions.
How Fidelis Security Supports Cyber-Healthy Networks?
Fidelis Security delivers tailor-made healthcare cybersecurity solutions that help hospitals identify and counter cyber threats before they compromise patient safety. With Fidelis, healthcare providers will see the full security picture. This helps them stop threats to important systems. Their dedicated technology identifies weaknesses in a network and medical devices, so they give real-time alerts, ensuring continuous patient safety and operational integrity.
Key strengths of Fidelis:
- Real-time Threat Detection: Fidelis monitoring identifies threats even before they disrupt medical services.
- Network Segmentation Tools: Fidelis enables health care providers to break down the networks to avert major damage in the event of a breach.
- Automated Security Protocols: AI-enabled threat detection and response capabilities of Fidelis ensure action in no time, giving less time for attackers to stay on board.
Fidelis ensures that health care teams work on their core competencies-that is providing quality patient care without ever having the specter of a network breach or system down.
What Cybersecurity Measures You Can Take for a Safer Health Network?
It is not easy building a cyber-healthy network, but healthcare organizations can do so through a few well-directed actions. The following is how healthcare institutions can strengthen their cyber defenses so as to protect the patient’s safety:
1. Track IoMT Devices, Prevent Breaches
Keep an updated list of all connected IoMT devices. This helps quickly detect cyber risks. This protects healthcare institutions from breaches.
2. Automate Updates
Regularly update your systems and devices. Use automated tools to install the latest security patches for operating systems and IoMT devices. Upgrades on systems reduce the probability of cyber-attacks and improve the best practices of healthcare cybersecurity.
3. Engage in Training and Education
Ongoing training on cybersecurity helps staff recognize risks of identity theft. It also covers trends in healthcare cybersecurity and real-time threats to patient data. It is established that regular training significantly reduces cyber risks within the health system.
4. Implement Network Segmentation and Access Controls
Limit access to the network based on user role and device importance. The segmentation of critical areas with strict access controls helps to limit the reach of a potential breach in healthcare networks.
5. Real-time Monitoring
Specialized tools will track healthcare cyber-attacks as they happen. This helps identify suspicious activity and improve the organization’s response plan. This approach can contain the threat landscape and minimize cybersecurity threats in the healthcare sector.
Cybersecurity in Health Care Is More Than Protection of Data—It Is Patient Care
Beyond the protection of data, healthcare cybersecurity is fundamentally linked with patient care. Every cybersecurity best practice helps maintain health and human services by assuring data integrity, maintaining patient privacy, and delivering uninterrupted medical care. Advanced technologies like Fidelis Security can be used for robust healthcare cybersecurity solutions by healthcare providers to shield patients from cyber risks while maintaining their operations.
Health cybersecurity is not just an IT issue anymore. It can affect people’s lives, so it is very important in healthcare. In today’s world, no part of patient care is more important than health-care cybersecurity. Cyber-healthy strategies protect PHI and bolster the sustained effort to better care for patients in today’s ever more complex threat landscape.
Partner with Cybersecurity Experts
Healthcare institutions must continue their digital transformations to electronic records and expand network access to patients through telemedicine, health records, patient portals, and other services. As they do, it’s important to build proactive cyber defense and cyber resilience into their IT environments.
Fidelis Security protects the world’s most sensitive data, assets, and critical business operations. Our Fidelis Elevate® and Fidelis Halo® platforms provide comprehensive cybersecurity for healthcare organizations worldwide.
We protect our customers’ data, assets, and business operations. We do this by offering full visibility from device to cloud. Our approach includes detailed mapping of the IT environment, various contexts, and risk assessments.
These features reduce areas that can be attacked. They automate prevention of exposure, threats, detection, and response to incidents.
They provide security professionals with important information. This includes context, accuracy, speed, and portability. These tools help them identify and stop threats earlier in the attack process.
By partnering with cybersecurity experts like Fidelis Security, you can proactively detect, deceive, and neutralize threats inside your network, protecting your organization from potential damage. With our expertise and tools, your security teams can stay ahead of cyber threats and safeguard your valuable patient data.
Don’t wait until it’s too late – let us show you what threats are lurking on your network so we can help safeguard your data and IT assets.



