Is your security team stopping threats before they enter, or just reacting after damage happens?
Because in the current era of advanced cyber threats, a reactive approach isn’t enough.
There must be a proactive defense strategy, fueled by threat intelligence!
Extended Detection and Response (XDR) solutions help organizations stop attackers, spot weaknesses, and stay protected with cyber threat intelligence data.
- Suggested Reading: Top 5 Proactive Threat Intelligence Use Cases for Enhanced Cyber Defense
What Is Threat Intelligence Management and Why Does It Matter Today?
Threat Intelligence Management is the process of:
- Collecting
- Analyzing
- Applying information about cyber threats.
Purpose:
It transforms,
Raw data -> Meaningful insights
These useful insights help the security team create strong security strategies and make better decisions.
It helps organizations go beyond simple data gathering to enable:
- Proactive detection
- Anticipation, and
- Response to cyber-attacks
Why Is Threat Intelligence Management Critical in Today’s Cybersecurity Landscape?
- Cyber threats are getting more advanced and complex, and are able to bypass traditional solutions.
- Organizations face prolonged issues like operational disruption, data theft, and reputation damage.
Proactive operational threat intelligence management helps organizations:
- Detect threats earlier
- Respond faster and more effectively
- Make informed security decisions
It shifts security from reactive to proactive and strategic, improving overall resilience against evolving attacks.
How Does XDR Enhance Threat Intelligence Capabilities?
XDR (Extended Detection and Response) is a modern cybersecurity approach that gives clear, complete visibility across different security areas in the complex cyber threat landscape, including:
- Endpoints
- Networks
- Cloud environments
Unlike traditional tools that work separately, XDR:
- Integrates data from various sources to support the threat intelligence lifecycle
- Offers a coordinated and stronger defense against emerging threats
How Fidelis Elevate® XDR Boosts Threat Intelligence
Fidelis Elevate® is a powerful XDR platform that improves threat detection and visibility. It brings together:
—all in one solution. This gives organizations a holistic view of their security, including attacker tactics, techniques, and procedures.
- Do you have the insight needed to stop attacks early?
- Can you detect threats at the earliest stage?
- Is your solution integrating network, endpoint, and sandbox data?

Building a strong threat intelligence management strategy means planning ahead and acting quickly. XDR platforms like Fidelis Elevate® help by offering smart, proactive solutions that keep up with changing threats through:
- Strategic Alignment: Helps organizations predict attacker moves and adjust their security. By always analyzing threat data, teams can focus on key risks and plan for the future.
- Advanced Technology Use:
| Feature | What It Does |
|---|---|
| MITRE ATT&CK Mapping | Map attacker tactics and techniques to show how adversaries act. |
| AI-driven Sandboxing | Automatically analyzes suspicious files safely to find hidden threats. |
| Deception Technology | Uses decoys to lure attackers and reveal their methods and goals. |
These features help build a strong strategic threat intelligence program that reduces risks and gives security teams a proactive advantage.
The Impact on Threat Intelligence Management
XDR platforms like Fidelis Elevate help security teams focus on real threats by improving detection and reducing false alarms. This ongoing approach to managing threats makes cyber defense stronger by:
- Gives clear, useful threat info to help make faster decisions
- Automatically connects and ranks threats to speed up response
- Gives clear data and context to support investigation and cleanup
This solution simplifies threat intelligence, helping organizations stop attacks by providing actionable intelligence to protect key assets.
Why Choose a Unified Threat Management Platform Over Standalone Tools?
Managing security with multiple disconnected tools often creates complexity and gaps, undermining an organization’s cyber defense efforts. This challenge is why unified threat management platforms are becoming the preferred choice.
Challenges of Tool Sprawl:
- Fragmented alerts and inconsistent data reduce visibility.
- Increased complexity leads to slower response and higher operational costs.
Fidelis Elevate® as a Complete Solution:
- Comprehensive Coverage:
Combines Endpoint, Network, Deception, and Active Directory protection in one platform. - Alert Noise Cancellation™:
Cuts false alarms by better integrating threat intelligence for threat accuracy. - Integrated Threat Hunting and Forensics:
Provides clear views and expert threat intelligence tools for fast investigation and fixing.
Fidelis Elevate® simplifies threat management with better detection and faster response.
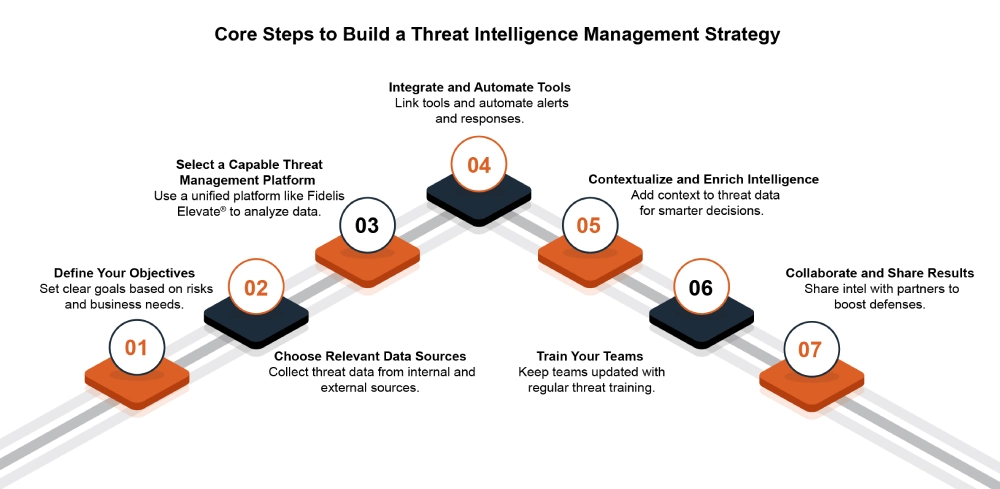
What Are the Core Steps to Build a Threat Intelligence Management Strategy?
-
Step 1: Define Your Objectives
Set clear goals, like improving your organization’s security posture, to focus on what matters most.
- Align your goals with your organization’s risks and key needs
- Set clear targets, like faster response or better threat detection
-
Step 2: Choose Relevant Data Sources
Threat intelligence works best with good data. Use a variety of sources that cover all parts of your environment.
- Collect data from networks, devices, cloud logs, and outside threat feeds
- Choose sources that fit your needs and provide timely, helpful information about relevant cyber threats
-
Step 3: Select a Capable Threat Management Platform
A complete threat management platform is key to bringing together and analyzing all the data well.
- Choose solutions like Fidelis Elevate® that combine endpoint, network, and deception tech
- Pick platforms with AI analytics, risk mapping, and Active Directory protection for smart threat management
-
Step 4: Integrate and Automate Tools
Linking security tools helps information move smoothly, and automation lowers manual work and speeds up responses.
- Connect your threat intelligence platform to SIEMs, firewalls, and endpoint tools
- Automate alert sorting, threat matching, and responses for faster, smarter work
-
Step 5: Contextualize and Enrich Intelligence
Raw data must be enriched with context to be useful.
- Match threat info with asset value, network layout, and business impact
- Use metadata and forensic details to understand attacker methods and weaknesses better
-
Step 6: Train Your Teams
Even the best tools need skilled analysts to understand and use the information.
- Give ongoing training on new threats, XDR tools, and response skills
- Encourage teams to share knowledge to build stronger skills
-
Step 7: Collaborate and Share Results
Threat intelligence is more powerful when shared.
- Share information with trusted partners, industry groups, and government agencies
- Use shared information to strengthen your defenses and help broader cybersecurity efforts
Following these steps helps your organization build a flexible, proactive threat strategy.
How Can You Operationalize Managed Threat Intelligence with XDR?
Managed threat intelligence paired with XDR turns raw data into effective, everyday cybersecurity defense through smart management and seamless integration.
1. Using Managed Threat Intelligence Services
Many organizations use managed threat intelligence providers to constantly collect, analyze, and share the latest threat information. These services help by:
- Give clear, helpful intelligence that highlights real risks and ignores distractions
- Offer expert analysis and context that internal teams might miss
- Help smaller security teams access advanced threat insights without needing lots of resources
Managed services work like an extra security team, always watching for new threats to keep your organization safe.
2. Enriching Internal Data and Integrating into XDR Workflows
To work best, actionable threat intelligence should be part of your security operations and decisions. With an XDR platform like Fidelis Elevate®, this integration is easy:
- Combine internal data from endpoints, networks, and cloud with external threat intelligence feeds
- Automatically link and prioritize threat data based on attacker methods
- Use automated workflows to speed up alert handling, investigation, and response while reducing manual work
This integration keeps your cybersecurity threat management ongoing, connected, and flexible, turning raw data into an effective defense.
3. Supporting Continuous Threat Exposure Management
Operationalizing managed threat intelligence within XDR also supports ongoing risk reduction through continuous threat exposure management:
- It shows you what’s happening across your whole digital environment in real-time, spotting weak points and risky actions before threat actors can take advantage.
- Built-in deception and Active Directory protection in the XDR platform trick attackers and uncover hidden dangers.
- By regularly updating threat info and defenses, your organization stays protected against new and changing threats.
Managed threat intelligence with XDR turns data into a strong tool to find, stop, and prevent cyber threats before damage happens.
What Is the Role of Threat and Vulnerability Management in This Strategy?
An effective and tactical threat intelligence management strategy isn’t complete without addressing vulnerabilities. XDR platforms provide powerful tools to help security teams pinpoint and manage weaknesses before they are exploited.
| Aspect | Description |
|---|---|
| Identification and Correlation | XDR watches data from endpoints, networks, and Active Directory to find real threats and vulnerabilities. |
| Prioritization with Context | Uses smart info to rank risks by real danger and attacker actions, so teams focus on the most important. |
| Support for IT and Cybersecurity Management | Helps improve IT security and response by closing gaps and speeding up actions. |
By combining threat Intelligence and vulnerability management, XDR helps organizations handle risks quickly and effectively.
What’s the Best Way to Get Started with an XDR-Based Strategy?
Building a good threat intelligence strategy with XDR requires careful steps. Here’s how organizations can succeed:
-
Start with a Clear Assessment and Goals
- Look at your current security setup
- Know your risks, rules, and business goals
- Set clear, measurable goals to keep your strategy focused and aligned with cybersecurity needs
-
Map Your Cyber Terrain and Spot Weaknesses
- Get a complete view of your digital environment
- Find vulnerabilities and hidden threat areas
-
Bring Teams Together and Use a Unified Platform
- Work together across IT, security, and management teams
- Pick a platform like Fidelis Elevate® that covers endpoints, networks, deception, and Active Directory
- One integrated solution makes detecting and responding to threats simpler and better
-
Keep Improving with Continuous Feedback
- Review and update your defenses regularly
- Train your team with the latest threat insights to stay prepared
Starting with these steps helps organizations build a strong, proactive threat intelligence strategy using XDR.
A strong threat intelligence strategy powered by XDR helps organizations move from reactive defense to proactive protection. With unified tools like Fidelis Elevate®, security teams can detect threats earlier, respond faster, and stay ahead of evolving cyber risks.
Frequently Ask Questions
What is a Threat Intelligence Management Strategy, and why is it important?
It’s a way to collect and use information about cyber threats to stop attacks early. It helps teams find and fix problems before damage happens.
How does XDR improve Threat Intelligence Management?
XDR gathers data from different places, like endpoints, cloud, and networks, into one system. This helps spot threats faster and makes it easier to respond.
What are the key steps to build a Threat Intelligence Management Strategy with XDR?
Set clear goals, gather data, pick the right security platform, connect your tools, add context to data, train your team, and share info with partners.
Why choose a unified threat management platform over separate security tools?
Using one platform is simpler and faster. It helps catch real threats better and reduces confusion from too many different tools.



