Breaking Down the Real Meaning of an XDR Solution
Read More See how Fidelis NDR enhances network security with proactive defense capabilities, offering
Want to stay ahead of threats in 2025? This research report is all you need to stay updated.
The traditional methods of detecting and mitigating cyberattacks will no longer be adequate as these attacks become sophisticated and frequent. These days, risk-based alerting and network detection and response (NDR) are regarded as essential tools for safeguarding enterprises. By avoiding false positives or low-priority warnings, risk-based alerting allows security teams to concentrate on the high-risk threats, saving time and resources.
This blog post will discuss NDR’s role in enhancing cybersecurity, how it supports risk-based threat assessments, and the significance of cutting-edge tools like Fidelis Network® Detection and Response for efficient threat detection and response.
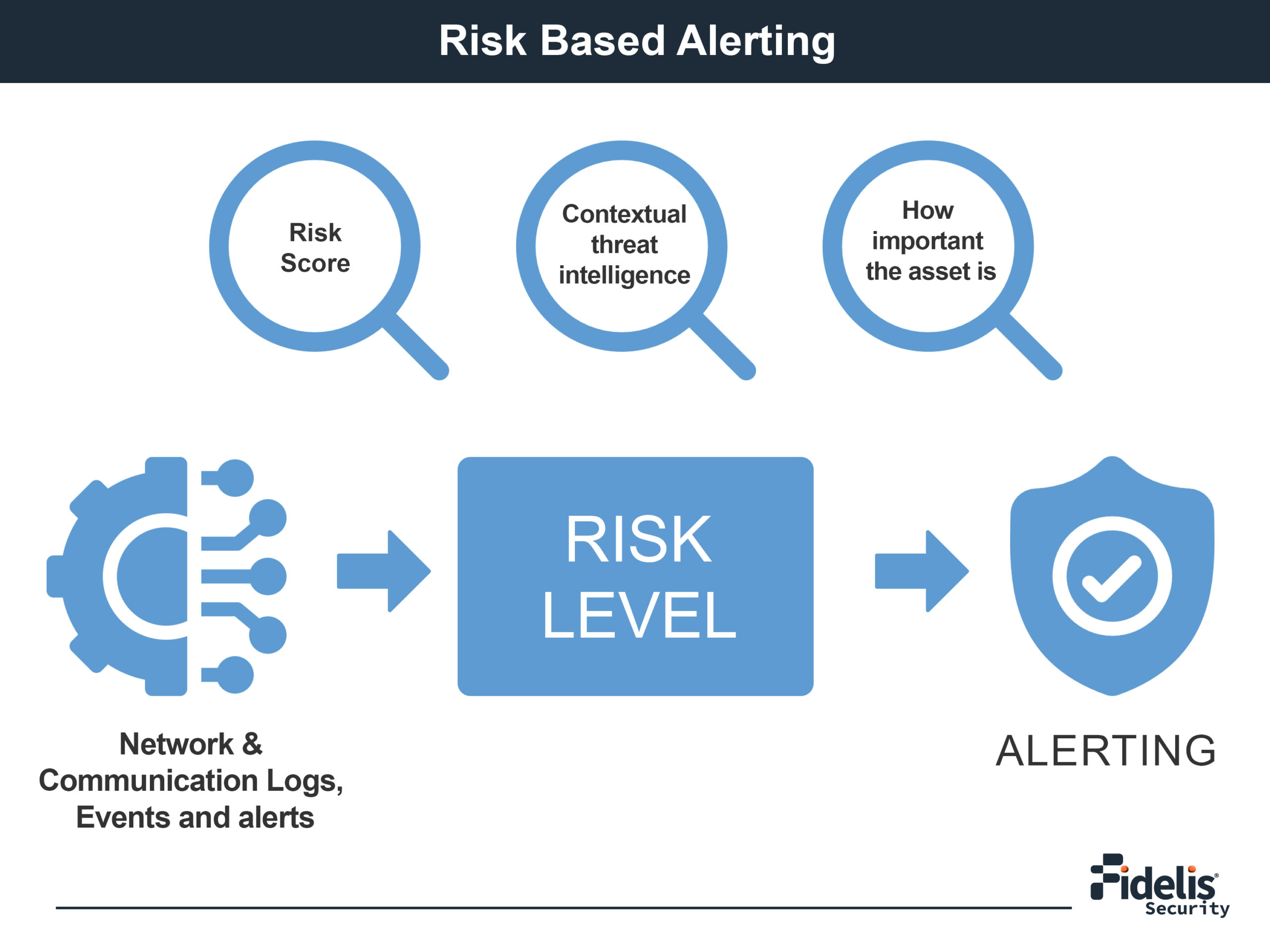
Risk-based alerting means prioritizing security alerts based on the potential risk they pose. Instead of dealing with all alerts the same, this method gives each event a risk score. This score considers things like how severe the activity is, how important the affected asset is, and contextual threat intelligence. This helps security teams decide which threats need immediate attention and which ones can be monitored or deprioritized.
Using risk-based assessments, security personnel can focus on high-risk alerts and avoid being overloaded by low-risk ones. This helps reduce alert fatigue, a frequent issue in today’s security environment.
NDR excels in real-time monitoring. It constantly analyzes network traffic and detects anomalies using behavioral analytics. Unlike traditional security tools that depend on known signatures, NDR looks for changes in network behavior. By looking into traffic, NDR can find threats that signature-based systems might miss, like APTs or insider threats.
This capability is very important for identifying suspicious activity such as lateral movement within the network or unauthorized access attempts. With the help of NDR, security teams can respond to incidents faster, which helps reduce potential damage.
Machine learning plays a vital role in enhancing the performance of NDR solutions. By analyzing network data, machine learning algorithms can pick on unusual activities that don’t follow the usual patterns. This updates the system with its risk assessments as new information comes in, giving a more accurate picture of potential threats.
By combining machine learning with behavioral analytics, NDR systems can better identify emerging and previously unknown threats. Unlike traditional systems that often give false positives, these newer systems improve their detection accuracy over time. The ongoing learning capability enables NDR solutions to adapt to new attack techniques and ensure reliable risk-based alerting.
NDR solutions can work with external threat intelligence sources to improve the data used for risk evaluations. By comparing current threats with known patterns or trends, security teams can better understand the severity of each alert. For example, using frameworks like MITRE ATT&CK allows NDR to map detected activities to specific tactics and techniques, giving teams a deeper insight about the threat.
Risk-based alerting considers both the importance of the affected system and the behavior of the threat. This helps in giving accurate risk scores that show not only the immediate anomaly but also its possible impact on the organization.
A big advantage of using risk-based alerting is that it greatly reduces alert fatigue. Security teams usually get a lot of alerts, many of which are not very important or false positives. Alert fatigue happens when the number of alerts is so high that it makes it hard for security teams to notice real threats.
By showing alerts that pose the highest risk and filtering out low-risk alerts, NDR helps security teams focus on what really matters. This means that important alerts get the attention they need, while low-risk events are saved for later review.
Automated responses are another important advantage of NDR solutions. When NDR systems find high-risk threats, they can start actions like isolating infected devices, blocking malicious traffic, or sending alerts to the right security experts. This helps speed up the incident response process and makes sure that serious issues are dealt with quickly.
NDR also helps with investigating what happened after an incident, letting security teams follow the attacker’s steps and understand the extent of the damage. This complete view of network activity is very useful for stopping current attacks and preventing future ones.
Harness Intelligent Threat Detection and Prioritized Risk Visibility.
In this datasheet, you’ll learn how to:
With times things need to advance. This advancement in network security resulted in the development of NDR. And it became an essential part of a cybersecurity plan. Earlier tools such as firewalls and antivirus software were enough to handle threats, but today’s attacks demand more advanced methods. Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) added that layer of protection by identifying and blocking known threats.
However, as attackers started using more advanced techniques, traditional tools couldn’t keep up. Signature-based detection wasn’t enough to protect against new and emerging threats. NDR addresses this issue by using a behavioral analysis approach, which can detect small anomalies in network traffic and user actions that might suggest a security breach.
Modern NDR solutions combine machine learning, threat intelligence, and automated response mechanisms, making them better at detecting and mitigating threats in real-time. This advanced ability makes NDR crucial for any organization looking to stay ahead in the fight against cyber threats.
Fidelis Network® offers a comprehensive system for risk-based alerting, helping security teams focus on the most important threats quickly. Here’s why it’s special:
Companies using NDR for risk-based alerting get several benefits:
In a world where cyber threats are becoming more complicated, using NDR for alerting based on risks is crucial. NDR gives real-time information about activities in network, uses behavioral analysis and machine learning to find and mitigate both familiar and new threats.
Companies seeking a solution to lower alert fatigue and enhance incident response and precision threat detection should explore Fidelis Network® Detection and Response. With Fidelis, security personals can proactively handle high-risk threats. This will keep their network safe from emerging cyber threats.
Yes, NDR is meant to work alongside other security tools, such as Security Information and Event Management (SIEM). While SIEM deals with managing logs and looking at past events, NDR offers real-time monitoring and behavior analysis. This makes NDR great for detecting threats that SIEM might overlook.
Traditional SIEM systems mainly depend on managing logs and using predefined rules. In contrast, Fidelis Network® Detection and Response provides real-time monitoring and analyzes behavior, making it better at detecting new and changing threats. It can give dynamic risk scores and automatically respond, offering a more efficient and accurate way to handle risk-based alerts.
Sarika, a cybersecurity enthusiast, contributes insightful articles to Fidelis Security, guiding readers through the complexities of digital security with clarity and passion. Beyond her writing, she actively engages in the cybersecurity community, staying informed about emerging trends and technologies to empower individuals and organizations in safeguarding their digital assets.
See Fidelis in action. Learn how our fast and scalable platforms provide full visibility, deep insights, and rapid response to help security teams across the World protect, detect, respond, and neutralize advanced cyber adversaries.