In Part 1 of our Shared Responsibility blog series, we provided a detailed overview to help you understand security in a public, hybrid or multi-cloud environment. We broke down the infrastructure stack, explained the responsibilities taken by the cloud service provider, and where you retain ownership over security. We also discussed how the shared responsibility model affects members of your team and changes the way you think about security as you move your workloads to the cloud. In this installment, we’ll dive deeper into shared responsibility model automation and the important role cloud security tools play in securing your complex, modern infrastructure at scale.
Meeting the Demands of Shared Responsibility Model Automation
Let’s quickly re-visit the shared responsibility model chart from Part 1. The sum total of your security ownership across each of your connected cloud environments is determined by your provider contract and the services you’ve chosen to use. Your first step is to define a strategy and choose tools that can handle the unique security requirements of each of your server-based and serverless instances, along with securing your on-premises bare-metal servers and virtual environments.
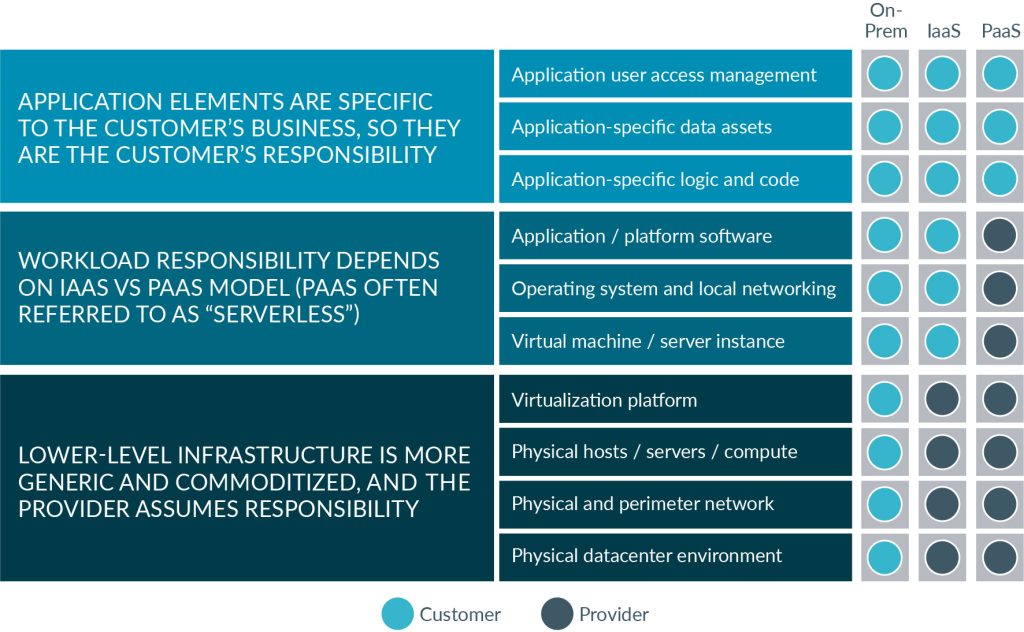
Regardless of where your contract with your provider draws the line, your security posture in a shared responsibility model depends on your ability to standardize and maintain security orchestration, action, and response across your entire infrastructure, including:
- Asset discovery, interrogation, and inventory monitoring
- Continuous inventory updates
- Vulnerability and exposure management, including network and privileged access configuration
- Integrity and drift monitoring
- Indication of compromise, threat detection, and security event management
- Network security configuration and management
- Compliance management and continuous compliance monitoring
Eight key attributes for shared security model automation
Effective cloud management unifies your security responsibilities on a single platform and provides shared responsibility model automation controls and compliance across all of your servers, containers, IaaS, and PaaS in any public, private, hybrid, and multi-cloud environment. Your cloud security solution should encompass the following eight key attributes in order to provide complete, effective, and efficient security:
Unified
Traditional security tools often don’t meet the needs of the various and unique needs of a complex, shared responsibility cloud security environment. Without a unified security solution, you end up tying together several different tools, which can lead to operational complexity, unnecessary redundancy, and potential gaps in coverage. A security platform built specifically for the cloud gives you a comprehensive set of configurable tools and the flexibility you need to close your gaps, improve your security posture, and adapt as your infrastructure grows and changes.
Automated
As your environment grows in size and complexity, it becomes increasingly difficult to keep track of all the various, moving parts. Shared responsibility model automation provides dependable speed and consistency, and frees up staff time to focus on strategic goals rather than repetitive tasks. Your security automation platform should automate asset discovery and monitoring, and should automatically deploy sensors when a new service, environment, or application is created. You’ll also need integration with your DevOps tools to automatically fail builds when new vulnerabilities might be introduced, assign new issues automatically, and monitor the development pipeline for remediation. With comprehensive, shared responsibility model automation in place, you can centralize and simplify your security integration and operations across systems and solutions that have different security concerns. An automated security platform also enables security to shift left into the development process, and empowers the adoption of a true DevSecOps culture.
Portable
With the rate of change we experience in technology, it’s no longer an option to say “no” to a better solution when it comes along. Everything about your application infrastructure, from the code you write to the containers you configure to security, needs to be portable. When moving a workload or application between clouds, your share of the shared responsibilities may change. Your security solution needs to work seamlessly across any public, private, hybrid, and multi-cloud environment while requiring as few changes as possible during lift-and-shift operations.
Comprehensive
Your share of the shared responsibility model includes a wide range of requirements, including asset discovery, inventory, assessment, remediation, threat detection, microsegmentation, traffic discovery, and continuous compliance. If you have separate tools for each of those security domains, you’re setting yourself up for operational headaches and worse–the very real potential for introducing blind spots and gaps. A comprehensive security tool not only covers each of these requirements, but automates as much of the security management as possible to alleviate your operational burdens.
Fast
Everything about the cloud boils down to speed. CI/CD pipelines delivering microservices and features to the cloud in real time increase the demand for fast, integrated security. Your solution cannot slow that process or get in the way of your development team’s ability to deliver. Instead, your solution should provide high-speed deployment, telemetry, and analytics that keep up with the speed of DevOps.
Integrated
The problem with legacy security solutions is that they tend to “bolt on” to cloud environments, rather than working seamlessly within your instances, applications, and workloads. These non-cloud-based solutions increase manual tasks and complicate monitoring. A built-in security solution that integrates directly with cloud infrastructures ensures consistency and compliance with no extra effort. Your security platform should also be built into your application stack, rather than added on after the fact. An API based, embedded security foundation, integrated as part of your DevOps process and workflows, allows you to scale your security implementation up and out as needed and in parallel with your growth without becoming a bottleneck for the CI/CD pipeline.
Scalable
While nothing is truly infinite, cloud resources are about as close as you can get. Unlike a bare-metal data center, when you run up against the limits of your current cloud infrastructure, you simply ask for more, and it’s there. That means your security solution must scale automatically and instantaneously to keep up with fast-breaking, dynamic cloud changes. But you don’t always scale up. Cloud resources also provide a valuable opportunity to use resources as needed, and then release them when demand drops. This elastic scalability should be mirrored in your security platform so that you only use what you need in real time.
Cost-effective
Cloud architectures offer right-sized, pay-as-you go and usage-based pricing, which means you can control your costs while maximizing the value of your investment. Your cloud security solution should follow the same model. Security solutions that are built specifically for the cloud should provide pricing options that mirror those offered by the cloud provider, and that scale with the resources you use.
Download the whitepaper to explore the basics of Shared Responsibility Model
- Who is responsible for what?
- Responsibilities maintained by your provider
- Shared Responsibility Automation
CloudPassage Halo is Shared Responsibility Model Automation That’s Built for the Cloud
Continuous monitoring and visibility across your cloud environments and into your data center, and across every environment is critical for maintaining accountability for your defined and accepted portions of the shared responsibility model. Fidelis CloudPassage Halo provides a broad range of security controls that simplify shared responsibility model automation, with seamless integration between your DevOps pipeline and AWS and Azure cloud services.
Halo provides seamless shared responsibility model automation across every environment
The ability to consolidate security onto a single platform simplifies operational processes and provides a foundation for automation. Halo provides cloud computing security and compliance in any public, private, hybrid, or multi-cloud environment. Rather than managing separate tools, Halo gives you continuous monitoring, automatic indication of compromise in the cloud, visualization of network traffic, and automated compliance management across IaaS services, virtual and bare-metal servers, containers, and Kubernetes environments.
Halo addresses the diversity and flexibility of hybrid cloud
With Halo, you can implement security controls across all your cloud applications, environments, and containers quickly and efficiently. With microagents and registry connectors that monitor and evaluate server and container infrastructure, across your cloud environments and in the data center, Halo is a single, unified platform that centralizes security management while decreasing complexity. Through bi-direction REST APIs, Halo allows you to automate security, settings, and policies. You can also export, import, and manage security policies using version control systems, and automatically enforce security policies throughout your CI/CD workflows based on pre-established rules and standards. These controls allow you to catch and remediate potential vulnerabilities before they become security gaps.
Halo delivers effortless, automatic security scalability
Halo’s distributed architecture offloads processing and automates security configuration controls, which means you can ensure compliance without impacting performance. By design, Halo maintains security coverage through infrastructure and application scaling. Once you’ve defined your security policies, you can also introduce new assets quickly, without additional configuration. And Halo’s on-demand licensing model means your security implementation always matches your application footprint.
Halo automates security policies across DevOps processes and workflows
Shared responsibility model automation allows your DevOps teams a secure path to self-service environment creation and rapid deployment. Whether your DevOps teams are spinning up new servers or your automated workflows are running builds, tests, and deployments, Halo’s developer SDK and toolkit, plugins for Jenkins, and automatic ingest of IaaS metadata help enforce security coverage through automation for your code repositories, build processes, and your DevOps toolkit. At each step in the CI/CD pipeline, Halo assesses changes and provides feedback on automated alerts to address potential vulnerabilities and misconfigurations before they become production security events.
Halo accelerates the path to compliance
Regulatory compliance is a never-ending challenge, requiring a team of knowledgeable professionals who stay up to date with industry changes and how those changes affect your particular company. Shared responsibility model automation is key to helping your compliance team maintain control over your growing cloud environment.
Halo provides over 20,000 pre-configured rules and more than 150 policy templates that cover standards, including PCI, CIS, HIPPA, SOC, and more, and provides automated remediation when deviations are detected. And with a single, easy to navigate dashboard and fully customizable reporting, complete with automated notifications, your team can maintain a pulse on compliance across your dynamic cloud environment in real time. With Halo, you’ll break free from the ad-hoc emails and meetings for vulnerability communications, and you’ll skip the fire drills before audit. Instead, with continuous monitoring and shared responsibility model automation, you’ll know your state of compliance in real time, and will be ready when audit time comes.
Halo: The Only Unified Solution Shared Responsibility Model Automation
Halo is the only battle-tested, unified solution built for addressing the needs of shared responsibility for AWS and Azure. With an emphasis on thorough, effective automation, Halo is especially valuable when it comes to defining, managing, and monitoring security across your multi-cloud environment. Automation reduces operational complexity and the potential for human error while reserving the time, resources, and energy of your team for ongoing product development efforts.
Ready to experience Halo for yourself? Contact us to speak with a cloud security expert.



