Breaking Down the Real Meaning of an XDR Solution
Read More Explore how XDR boosts threat detection and incident response with enhanced visibility,
Want to stay ahead of threats in 2025? This research report is all you need to stay updated.
Security teams struggle to detect and respond to attacks across expanding environments. Cloud systems, digital initiatives, and IoT devices have created complexities where standard security fails. Meanwhile, attackers remain hidden while security staff drown in alerts without adequate visibility.
Fidelis Elevate® solves this problem through active extended detection, offering a proactive and comprehensive cybersecurity solution with comprehensive visibility across networks, endpoints, cloud systems, and email, changing how teams detect, investigate, and counter sophisticated threats.
Prevention-only security strategies no longer suffice. Gartner analysts recommend shifting focus to post-breach detection and response, requiring deeper visibility with richer context than most organizations possess. Advanced cybersecurity solutions like XDR provide this deeper visibility and detection capabilities by integrating multiple security layers, offering comprehensive insights and proactive defenses against cyber threats.
Security teams typically face:
These problems create advantages for attackers. When compromise-to-lateral-movement times often measure under two hours, security teams need rapid detection capabilities. Yet most breach investigations reveal significant delays between initial compromise and eventual discovery.
The impact of these visibility gaps extends beyond just delayed detection. Organizations frequently discover breaches only after data exfiltration has occurred, customer information has been compromised, or ransomware has encrypted critical systems. By then, the damage, both financial and reputational, has already been done.

Most organizations have built security programs around prevention tools:
While these remain essential, they consistently fail against determined attackers who bypass perimeter defenses. Even SIEM platforms, despite their strengths in log aggregation and compliance reporting, lack the content-level data needed for effective post-breach detection.
Traditional security tools focus on known threats and signatures, leaving organizations vulnerable to zero-day exploits and novel attack techniques. They generate logs showing that something happened but rarely provide detailed content showing exactly what occurred during an attack sequence. Without this granular visibility, security analysts must piece together fragments from multiple systems—a time-consuming process that delays response when minutes matter.
To address these challenges, extended detection and response (XDR) solutions have emerged as crucial integrated cybersecurity solutions. XDR combines endpoint and network detection capabilities, providing comprehensive visibility and proactive defenses against advanced cyber threats. By enhancing organizations’ ability to analyze risks and respond effectively to attacks, XDR platforms help maintain operational continuity.

Fidelis Elevate® takes a fundamentally different approach by providing contextual visibility across the entire environment through network detection and response, ensuring robust defense mechanisms and comprehensive analysis across various environments:
Fidelis Network® doesn’t just capture basic traffic data. Its Deep Session Inspection (DSI) technology scans traffic bi-directionally across all ports and protocols, revealing:
This advanced network detection capability goes far beyond knowing a connection occurred; it shows exactly what happened during each session, even on non-standard ports where attackers often hide.
The technology inspects traffic at wire speed, decoding and analyzing over 300 protocols and applications. Unlike typical network monitoring that samples traffic or focuses only on standard ports, DSI examines everything, including encrypted traffic patterns, to identify potential threats regardless of where or how they manifest.
The platform captures over 300 metadata attributes, giving security teams exceptional investigative context:
Unlike costly packet capture solutions requiring complex decoding, Fidelis metadata enables organizations to keep 30-90 days of searchable history using 80% less storage. This approach delivers 90% of relevant security data while eliminating storage constraints that typically limit investigation timeframes.
The metadata repository supports both immediate threat detection and backward-looking historical analysis when new intelligence emerges, helping uncover previously undiscovered compromises.
This historical capability proves particularly valuable when new threat intelligence emerges. Security teams can immediately search months of historical data to determine if similar attack patterns previously went undetected. This retrospective analysis often uncovers dormant threats that bypassed existing controls but left traceable evidence in the metadata.
Fidelis Endpoint® captures critical system activities:
This visibility persists whether devices operate on corporate networks or remotely. Security researchers consistently recommend EDR capabilities as the cornerstone of threat hunting programs since they reveal definitive evidence of attacker activities that network monitoring might miss.
The endpoint component doesn’t just record events—it analyzes them in real-time for suspicious patterns. By integrating endpoint security with other advanced detection methodologies, it enhances visibility and defense capabilities across various environments. It captures the relationships between processes, showing the complete lineage of how an attack unfolds. This visibility extends to fileless malware techniques that operate primarily in memory, leaving minimal traces on disk where traditional antivirus would detect them.
Raw data doesn’t help analysts without proper context. Fidelis Security, through its advanced cybersecurity solutions provided by the Fidelis Elevate® platform, converts visibility into actionable intelligence through several mechanisms:
The platform continuously maps the entire environment, providing:
This mapping helps analysts quickly spot behavioral anomalies and understand normal vs. abnormal communication patterns without manual baseline creation.
The automated discovery capabilities identify and categorize assets without requiring manual inventory processes. This ensures security teams work with complete and current information about their environment. The system continuously updates this map as new devices join the network, applications are installed, or communication patterns change, ensuring security decisions reflect the current reality rather than outdated assumptions.
Fidelis Deception® deploys realistic decoys, breadcrumbs, and credentials throughout the environment, providing:
This approach fundamentally changes security dynamics; attackers must avoid every trap while defenders need only catch them once. The deception components automatically adapt to network changes, preventing attackers from identifying them through environmental analysis.
Unlike static honeypots of the past, Fidelis Deception® creates highly authentic decoys based on actual production systems. These decoys include realistic content, convincing configurations, and plausible user activity patterns. When attackers interact with these deception elements, they trigger high-confidence alerts that require immediate investigation, effectively eliminating the false positive problem that plagues many security tools.
Fidelis Network® sensors monitor five critical areas:
This placement strategy eliminates blind spots where attackers traditionally hide and enables tracking throughout the entire attack lifecycle.
The strategic positioning ensures visibility across the modern distributed enterprise. Gateway sensors monitor north-south traffic between internal networks and external destinations. Internal sensors track east-west movement that would otherwise go undetected by perimeter tools. Cloud sensors extend visibility into virtual environments where traditional network monitoring cannot reach. Email and web sensors focus on the primary attack vectors used in most breaches.

This visibility approach delivers measurable security operations improvements:
The XDR platform reduces detection and response timeframes by:
This addresses the experience gap many security teams face. Rather than requiring analysts to manually piece together evidence, the system presents validated conclusions with supporting evidence, allowing less-experienced team members to make appropriate response decisions.
The platform’s unified approach connects seemingly disparate alerts into coherent attack stories. It automatically enriches detections with relevant context from across the environment, prioritizing them based on potential impact. This correlation reduces the mean time to detect (MTTD) and mean time to respond (MTTR) metrics that security leaders focus on improving.
For proactive security operations, Fidelis Elevate® transforms threat hunting from art to science:
These capabilities help security teams find hidden compromises before they cause damage, addressing the reality that determined attackers eventually bypass preventive controls.
The platform supports both structured and unstructured hunting approaches. Analysts can follow hypothesis-driven methodologies, starting with a specific assumption about possible attacker behavior and testing it against the data. Alternatively, they can perform exploratory hunting, looking for anomalies and suspicious patterns without preconceived notions. The rich metadata makes both approaches more efficient than traditional hunting techniques.
Beyond threat detection, the platform provides data protection through:
This comprehensive approach protects sensitive information even when traditional controls fail.
The content-aware monitoring capabilities identify potential data exfiltration regardless of the channel used. Whether attackers attempt to steal data through encrypted web sessions, cloud storage uploads, email attachments, or other means, the platform flags suspicious transfers based on content analysis rather than just destination or volume triggers that generate excessive false positives in most DLP solutions.
The cybersecurity industry faces a critical talent shortage. Fidelis addresses this challenge through:
Fidelis Elevate® amplifies security team effectiveness by:
These capabilities help organizations maximize existing security staff while building advanced detection skills.
The platform’s workflow automation capabilities handle repeatable tasks that typically consume analyst time. For example, it automatically enriches alerts with relevant context, performs reputation lookups, identifies affected assets, and provides risk assessments. This automation frees experienced analysts to focus on complex threats while enabling junior team members to handle routine investigations more confidently.
For organizations needing additional expertise, Fidelis MDR services provide:
Unlike basic managed security monitoring, Fidelis MDR leverages analysts who have worked over 4,000 incident response cases and testified in more than 100 court proceedings for commercial and government clients.
The MDR team doesn’t just monitor alerts; they actively hunt for threats within customer environments. They apply lessons learned across the entire customer base, ensuring that techniques seen in one organization inform the protection of all clients. This collective defense approach provides economies of scale that individual organizations cannot achieve independently.
Organizations can implement Fidelis Elevate® through:
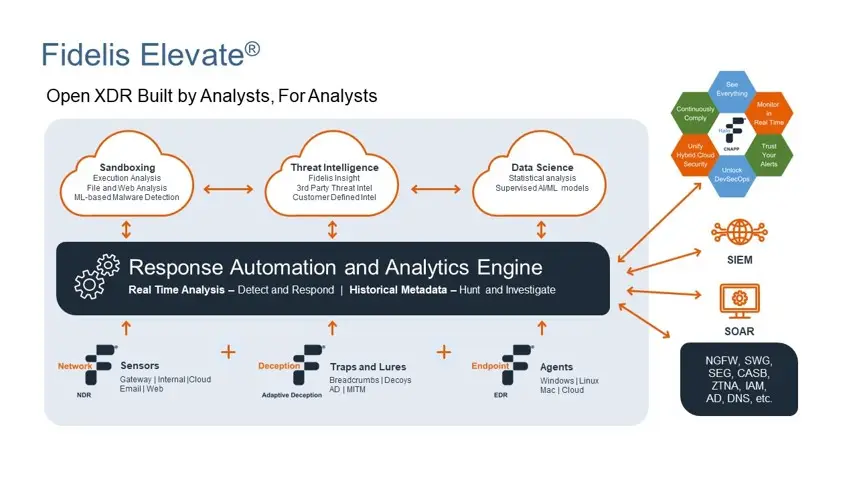
The complete platform provides visibility across:
By integrating network security with these measures, the platform enhances overall visibility and defense mechanisms against cyber threats. This approach eliminates security gaps that attackers exploit during complex campaigns.
The unified deployment provides a single management console for all security operations, eliminating the need to pivot between multiple tools during investigations. This integration reduces training requirements, streamlines workflows, and ensures consistent security policies across all environments.
Organizations can also adopt components incrementally:
This staged approach delivers immediate security improvements while building toward comprehensive coverage.
Each phase provides standalone value while creating a foundation for subsequent capabilities. Organizations typically begin with their most critical security gaps, often focusing on network visibility or endpoint protection before expanding to more advanced capabilities. This approach allows security teams to develop expertise with each component before adding complexity.
Security effectiveness ultimately depends on visibility and understanding. Organizations that see more, comprehend faster, and respond quicker successfully counter sophisticated attacks.
Fidelis Elevate® provides the contextual visibility modern security operations require. By combining network, endpoint, cloud, and email monitoring with advanced analytics and deception, the platform transforms threat detection and response capabilities.
As attack complexity increases, organizations must focus equally on prevention and rapid post-breach response. With comprehensive visibility and rich context, Fidelis Elevate® enables security teams to:
For organizations moving beyond traditional security models toward robust detection and response capabilities, Fidelis Elevate® provides the essential foundation. By expanding visibility across the entire environment and aligning it for effective threat detection, organizations significantly improve their defense against sophisticated attacks.
As organizations transform digitally and threat actors advance their techniques, comprehensive visibility has become essential rather than optional. Fidelis Elevate® delivers this critical capability, empowering security teams to detect, investigate, and counter threats faster and more effectively than ever before.
Sarika, a cybersecurity enthusiast, contributes insightful articles to Fidelis Security, guiding readers through the complexities of digital security with clarity and passion. Beyond her writing, she actively engages in the cybersecurity community, staying informed about emerging trends and technologies to empower individuals and organizations in safeguarding their digital assets.
See Fidelis in action. Learn how our fast and scalable platforms provide full visibility, deep insights, and rapid response to help security teams across the World protect, detect, respond, and neutralize advanced cyber adversaries.