Security teams now handle up to two million alerts daily, and the time it takes to resolve threats—MTTR—can directly affect business resilience. Cloud-based Extended Detection and Response (XDR) systems address these challenges by streamlining the entire process—from detection to automated remediation. By harnessing cloud-native architectures and response automation, organizations can detect threats faster and cut resolution times significantly. This blog examines how integrating automated incident response with Cloud XDR reduces MTTR and empowers security teams to manage complex multi-cloud environments effectively.
"XDR de-couples the storage of security-relevant data from the threat detection, investigation, and response functions. XDR is meant to fill the gap where a lot of SIEMs are just too rooted in log collection (for storage), compliance, and traditional correlation rules to be that effective at preventing a successful breach."
Gurucul, Unified security and risk analytics technology provider
Building Faster Cloud XDR Systems with Integration and Data Management
- Integration Points with Cloud Service Providers:
Cloud XDR needs to blend with major cloud service providers. These connections help monitor cloud-specific security events and control planes better. XDR must coordinate responses across AWS, Azure, and GCP for multi-cloud environments. The integrations should also work with cloud-specific security controls while keeping protection policies consistent. - Data Collection and Normalization Pipeline:
Security data comes in many forms, which makes normalization crucial. The data collection pipeline gathers information from multiple security layers and converts this data into a standard format. This process gives consistent labels to usernames, IP addresses, roles, and processes across different control points. - Real-Time Analytics Engine Requirements:
The analytics engine sits at the heart of XDR's success. This engine must use behavioral analysis to set baselines for normal activity and spot changes. It also uses machine learning algorithms that analyze data immediately to find patterns and unusual activities that might signal threats. The engine then links events across different security layers to catch complex attack patterns that basic solutions might miss.
Automated Detection Strategies to Minimize MTTR
Behavioral Analytics for Cloud Workloads
Behavioral analytics aims to grasp what counts as “normal” in a cloud setup and spot differences that might point to a threat. Unlike systems with fixed rules behavioral analytics builds a changing model by always keeping an eye on what users and systems do. These setups catch odd things, like weird login patterns or surprise data moves, which could mean security risks. By finding and dealing with these strange events behavioral analytics helps cut down the odds of big security problems giving cloud operations a way to defend themselves before trouble starts.
Container and Serverless Security Monitoring
Today’s cloud setups often use containers and serverless computing systems, which need special security tools. Security systems that work during runtime keep an eye on things like changes to files, how processes act, and network traffic in real time. These systems can jump into action on their own to stop possible threats when they spot something abnormal. Also, looking for weak spots and fixing them helps deal with known security issues. This is important in serverless setups where old-school security methods that focus on borders don’t work well. That’s why runtime security is key to protecting these systems.
Identity-Based Threat Detection
Identity-based threats, like compromised credentials or privilege escalations, are a common issue in cloud environments. Advanced systems use identity analytics, combined with machine learning and behavioral analysis, to monitor user activities and access patterns. These tools can quickly detect suspicious behaviors, such as login attempts from unusual locations or unauthorized privilege changes. When a potential threat is identified, these systems can automatically revoke access or trigger additional authentication steps. This ensures that threats are mitigated before they escalate, reinforcing the integrity of cloud identity frameworks.
Machine Learning Models for Anomaly Detection
Machine learning has an influence on improving anomaly detection by using methods like supervised, unsupervised, and semi-supervised learning. Unsupervised learning works well in cloud settings because it spots unusual patterns without needing pre-labeled data. Deep learning models such as autoencoders bring a new level of complexity allowing the system to find subtle irregularities in intricate setups. These tools offer a strong way to identify anomalies that might slip through the cracks leading to a more secure and productive cloud setup.
Designing Automated Response Playbooks
Response playbooks form the basis for automated incident response. These well-crafted workflows spell out each action to take during a security event. Playbooks include requirements like necessary logs and detection tools, in-depth response steps, ways to communicate, and expected results. Flexible playbooks prove useful because they adjust to the changing nature of incidents letting security teams modify their actions based on how serious the threat is. This leads to a smooth and effective response process, cutting down resolution times by a lot.
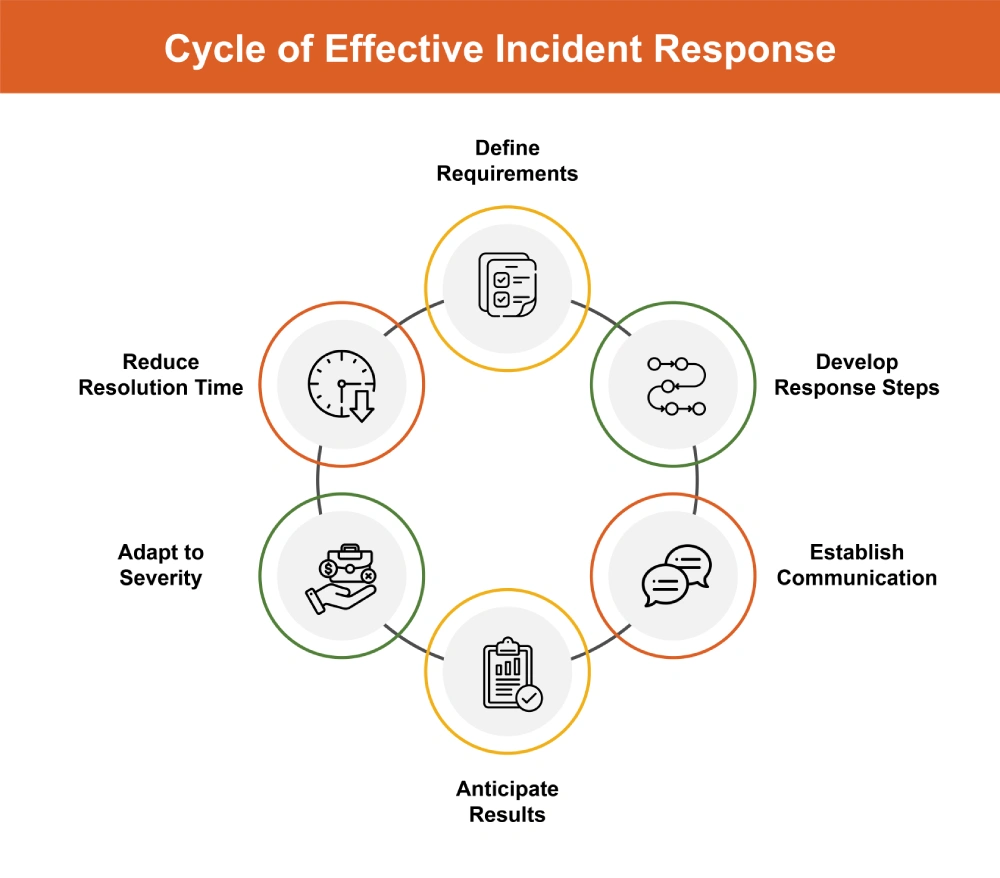
When security incidents occur, every minute counts. Our guide shows you how to:
- Stop threats before they spread
- Handle incidents efficiently to reduce damage
- Build a more resilient response capability
Automated Threat Containment Across Platforms
Effective threat containment involves isolating compromised systems immediately to prevent the spread of attacks. Automated XDR (Extended Detection and Response) systems excel in this by segregating affected network segments and blocking malicious activity as soon as it is detected. These systems also enable consistent threat containment across multiple cloud platforms, such as AWS, Azure, and Google Cloud, despite their differing security configurations. Additionally, automated patching mechanisms address vulnerabilities promptly, improving overall security without the need for human intervention.
Forensic Data Collection in Cloud Environments
Given the dynamic nature of cloud resources, collecting forensic data must be both rapid and comprehensive. Automated forensic tools use cloud-native APIs to gather critical information, such as disk images, memory dumps, and activity logs, at the moment an incident occurs. This ensures that evidence is preserved despite the transient nature of cloud infrastructures. These tools also maintain a secure chain of custody, ensuring the integrity of forensic data for post-incident investigations and regulatory compliance.
Validating and Testing Response Mechanisms
Validation of automated response workflows is essential to ensure they function as intended. Simulated environment testing allows organizations to identify weaknesses or gaps in their security protocols. Regularly scheduled tests and drills can confirm that detection tools are operating correctly and that response mechanisms are effective. This iterative process not only builds confidence in automated security systems but also fosters continuous improvement, making cloud environments more resilient to evolving threats.
Best Practices for Incident Response: Reducing MTTR through Automation
Reducing Mean Time to Resolution (MTTR) is critical for effective incident response in today’s complex IT environments. Here’s how automation can streamline incident response and dramatically decrease resolution times:
Implement Automated Detection Systems
Early detection significantly reduces incident impact. Deploy automated systems that can:
- Continuously monitor infrastructure, applications, and network traffic
- Use anomaly detection to identify unusual patterns
- Correlate events across multiple systems to detect complex incidents
- Generate alerts with meaningful context about the potential issue
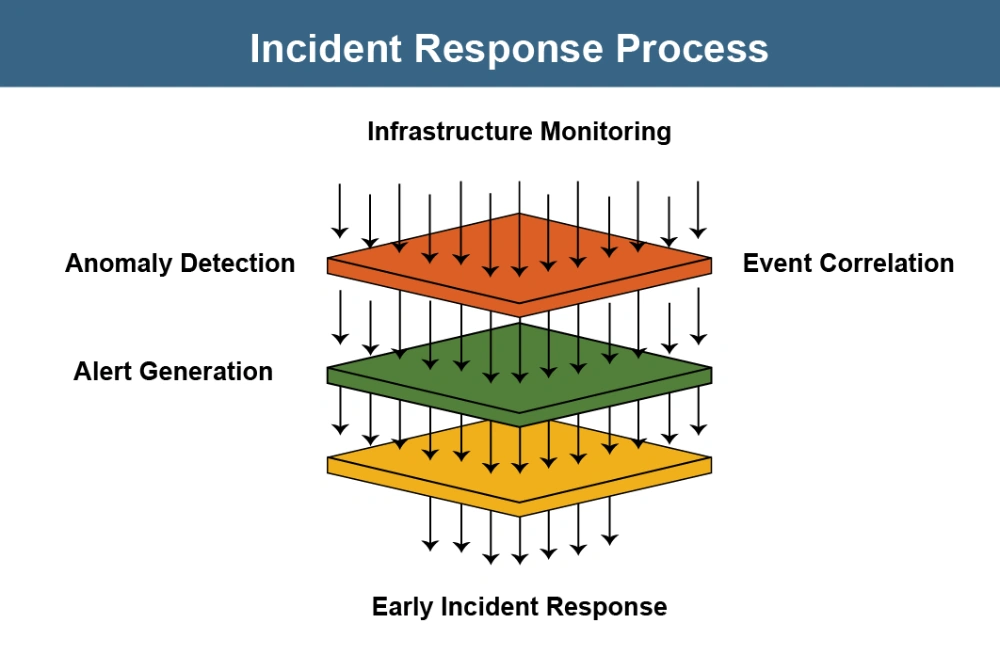
These systems help catch incidents in their earliest stages before they cascade into larger problems.
Create Standardized Incident Classification
Automation works best when incidents are properly categorized. Develop a standardized classification system that:
- Categorizes incidents by type, severity, and affected systems
- Automatically assigns appropriate priority levels
- Routes incidents to the correct response teams
- Applies relevant response playbooks based on classification
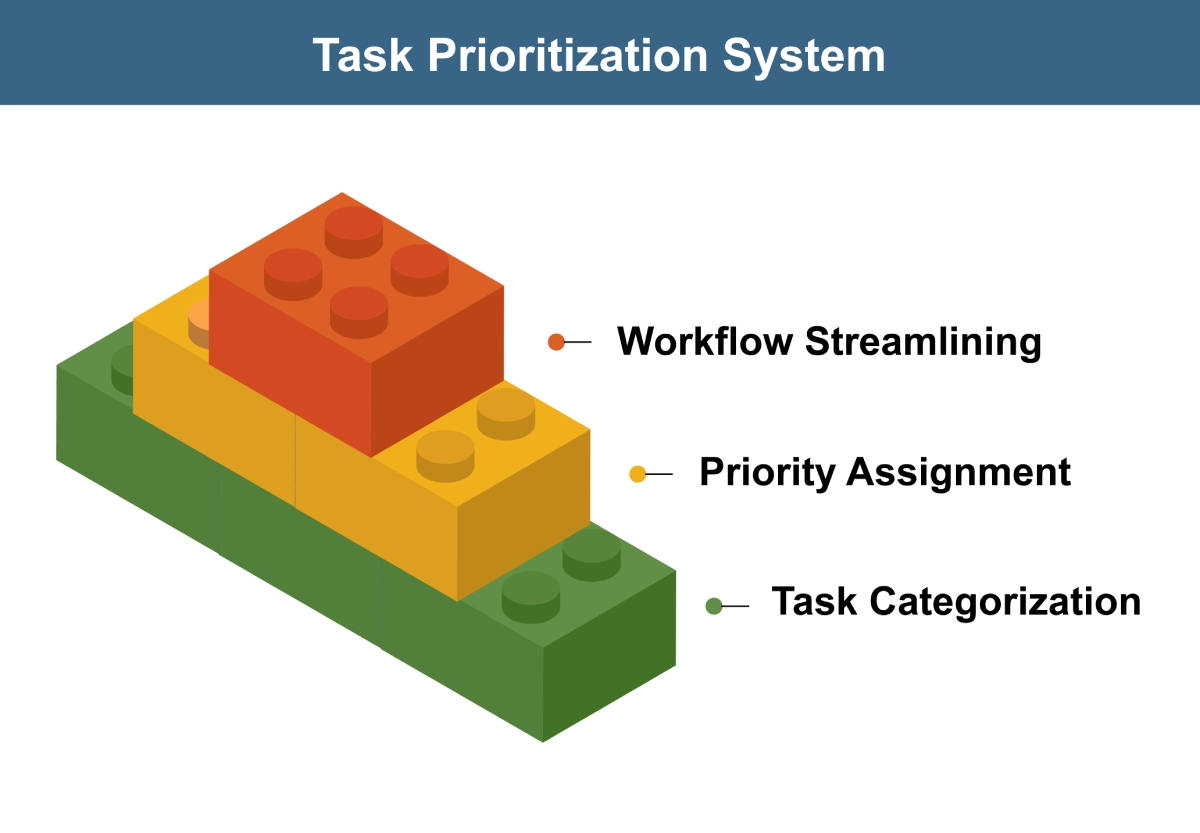
This standardization ensures consistent handling and appropriate resource allocation for each incident.
Develop Automated Response Playbooks
For common incidents, automated playbooks can execute initial response actions without human intervention:
- Build playbooks for recurring incident types with clear resolution paths
- Include automatic diagnostic steps to gather relevant information
- Implement self-healing mechanisms for known issues
- Create decision trees that can escalate complex cases to human responders
These playbooks handle routine issues immediately while letting teams focus on complex problems.
Integrate Tools Across the Response Lifecycle
Tool fragmentation slows response times. Create an integrated ecosystem where:
- Monitoring tools connect directly to incident management systems
- Diagnostic tools automatically feed results into response workflows
- Communication platforms receive real-time incident updates
- Remediation tools can be triggered from within the incident workflow
This integration eliminates manual handoffs that delay resolution.
Leverage Contextual Enrichment
Automated context gathering speeds troubleshooting:
- Automatically collect configuration data for affected systems
- Pull relevant logs and metrics before and during the incident
- Identify recent changes that might have contributed to the issue
- Present historical incident data for similar past problems
This context helps responders understand the issue faster without manual investigation.
Implement Automatic Remediation for Known Issues
For well-understood incidents, implement automated remediation:
- Create scripts that can safely restore service for common failures
- Implement automatic scaling for resource-related incidents
- Develop self-recovery mechanisms for application components
- Build automated fallback procedures for critical services
These mechanisms can resolve issues in seconds rather than minutes or hours.
Use ChatOps for Collaborative Response
Automation-assisted collaboration improves team coordination:
- Create dedicated incident channels that aggregate relevant information
- Implement chatbots that can execute diagnostic commands
- Build dashboards showing real-time incident status
- Develop notification systems that alert the right people at the right time
This approach keeps everyone informed and enables faster coordinated action.
Establish Continuous Improvement through Analytics
Use incident data to continuously improve automated responses:
- Track MTTR metrics for different incident types
- Identify common manual steps that could be automated
- Analyze incidents that bypassed automated detection
- Measure effectiveness of automated remediation actions
This data-driven approach helps refine automation over time for increasingly better results.
Balance Automation with Human Oversight
While automation dramatically improves MTTR, maintain appropriate human oversight:
- Implement approval workflows for high-risk automated actions
- Create clear escalation paths when automation reaches its limits
- Maintain documented procedures for manual intervention
- Schedule regular reviews of automated response effectiveness
This balanced approach ensures automation remains a powerful ally rather than an uncontrolled risk.
Overcoming Cloud Incident Management Challenges
Security teams face numerous challenges when managing incidents in cloud environments. Here are key strategies to overcome these challenges:
Establish Cloud-Specific Incident Response Procedures
Traditional incident response procedures often fall short in cloud environments. Security teams should develop cloud-specific playbooks that address the unique aspects of cloud infrastructure. This includes understanding shared responsibility models with cloud providers, identifying which response actions can be taken independently, and which require provider coordination.
For example, when investigating a potential compromise of a cloud workload, teams need predefined procedures for isolating instances without disrupting the entire application architecture. These procedures should account for auto-scaling groups, load balancers, and other cloud-native components.
Implement Robust Identity and Access Management
Many cloud security incidents stem from identity misconfigurations or credential compromise. Security teams should:
- Implement the principle of least privilege across all cloud resources
- Use just-in-time access provisioning where possible
- Enable multi-factor authentication for all privileged accounts
- Implement comprehensive logging of all identity-related activities
- Create automated alerts for suspicious authentication patterns
This approach significantly reduces the attack surface while providing critical visibility when responding to incidents.
Leverage Cloud-Native Security Tools
Cloud providers offer native security tools that provide deep visibility into the environment. Rather than trying to force traditional security tools to work in the cloud, teams should:
- Use cloud-native security information and event management (SIEM) solutions
- Implement cloud security posture management (CSPM) tools
- Enable cloud workload protection platforms (CWPP) for runtime protection
- Utilize cloud-native API monitoring to detect suspicious activities
These tools are designed specifically for cloud environments and often provide deeper integration than third-party solutions.
Automate Response Actions
The scale and speed of cloud environments make manual incident response challenging. Security teams should:
- Create automated response workflows for common incidents
- Develop infrastructure-as-code templates for rapid deployment of forensic resources
- Use serverless functions to automatically contain compromised resources
- Implement automated rollbacks when suspicious code deployments are detected
Automation ensures faster and more consistent response even when incidents occur at scale.
Develop Cloud Forensic Capabilities
Traditional forensic approaches often don’t work in ephemeral cloud environments. Teams should:
- Create processes for capturing forensic images of cloud instances
- Implement comprehensive logging across all cloud services
- Develop capabilities to analyze cloud-specific artifacts like API calls and configuration changes
- Establish procedures for preserving evidence in dynamic environments
This ensures teams can conduct thorough investigations even when cloud resources are constantly changing.
Practice Continuous Compliance Monitoring
Compliance drift is common in dynamic cloud environments. Teams should:
- Implement continuous compliance scanning tools
- Create automated alerts for non-compliant resources
- Develop remediation workflows for common compliance issues
- Implement policy-as-code to enforce compliance requirements
This proactive approach can prevent incidents caused by misconfigurations and ensure regulatory requirements are consistently met.
Improve Visibility Across Multi-Cloud Environments
Many organizations use multiple cloud providers, creating visibility challenges. Security teams should:
- Implement centralized logging across all cloud environments
- Use cloud-agnostic security tools where appropriate
- Create consistent tagging policies across clouds to improve resource tracking
- Develop normalized alerting frameworks that work across providers
This comprehensive visibility ensures incidents don’t go undetected due to monitoring gaps between cloud environments.
By implementing these strategies, security teams can significantly improve their ability to detect, investigate, and remediate incidents in modern cloud environments.
How Does Fidelis Elevate Cut Down MTTR with Cloud XDR Incident Response?
XDR platforms bring together data from endpoints, networks, and cloud services to automate how threats are spotted and dealt with. A well-built Cloud XDR setup joins security parts that were once separate. It gathers data from many places, puts it all in one spot in a standard format, and links events using smart analysis to find tricky attack patterns. This smooth connection is key to finding threats and cutting down the time to fix them.
Fidelis Elevate shows this approach by:
- Collecting and Normalizing Data: It gathers security info from endpoints, servers, cloud services, networks, and identity providers then standardizes this data into a unified pool. This ensures consistent labels for usernames, IP addresses, and roles across control points.
- Real-Time Analytics: Its analytics engine uses behavior analysis and unsupervised machine learning to establish baselines, spot anomalies, and link events across security layers as they happen. This ability allows for fast threat detection—even in containerized or serverless settings.
- Automated Response Playbooks: The platform lets security teams set up automated playbooks to trigger immediate fix actions. When the system spots a confirmed threat, Fidelis Elevate can cut off affected workloads and grab forensic evidence (like disk images and memory snapshots). This ensures quick containment.
- Multi-Cloud Integration: The solution works with big cloud service providers such as AWS, Azure, and GCP. This gives ongoing visibility and a combined view across different environments. This unity is key to consistent protection and faster incident response in setups that use multiple clouds.
- Identity-Based Threat Detection: Fidelis Elevate has an influence on Identity Threat Detection and Response (ITDR) to keep an eye on what users do and examine how they access things. This helps spot identity-based dangers—like stolen login info or when someone tries to get more power than they should—right away.
- Centralized Logging and Visibility: It works with built-in logging services (like AWS CloudTrail, Azure Monitor, Google Cloud Logging) to give a complete picture of security events. This makes it easier to connect the dots and act across the whole cloud setup.
Together, these features give Fidelis Elevate the power to cut down MTTR. It does this by automating how it finds, stops, and fixes problems across all areas of security.
Frequently Ask Questions
What is Cloud XDR and how is it different from older security tools?
Cloud XDR brings together many security products into one system. Unlike older tools, it combines threat detection and response across cloud setups, endpoints, networks, and apps with automated workflows.
How does automated incident response make security operations better?
Automated incident response boosts operations. It does this by bringing together data from many sources linking security events, and running preset actions when it spots threats. This helps teams handle tricky threats more.
What are the key components of a modern Cloud XDR system?
Modern Cloud XDR systems include data ingestion mechanisms, a central repository, correlation engine, response orchestration capabilities, and visualization interface—all working together to address security threats across cloud environments.



