Looking to tighten your organization’s security?
Start with an attack surface assessment! This process identifies all the potential entry points that attackers might exploit. By understanding and mitigating these vulnerabilities, you can significantly bolster your defenses.
In this article, we’ll explore what an attack surface assessment involves and how to effectively conduct one.
Understanding Attack Surface Assessment
An attack surface assessment identifies potential vulnerabilities within an organization and enhances security measures by evaluating all possible entry points that an attacker could exploit, including known vulnerabilities targeted by cybercriminals.
Effective attack surface management (ASM) involves identifying, monitoring, and mitigating risks across an organization’s assets, improving the ability to respond to cyber threats.
The attack surface includes digital, physical, and human-related aspects, and a broader surface means more attack vectors for attackers. Conducting a thorough attack surface analysis helps identify overlooked vulnerabilities, reduce the risk of cyberattacks, and prioritize vulnerabilities in both cloud-based and on-premises assets to implement effective security measures.
Suggested Reading: What Should a Company Do After a Data Breach? The First 5 Steps to Take
Attack surfaces can be classified into three main categories. These categories are:
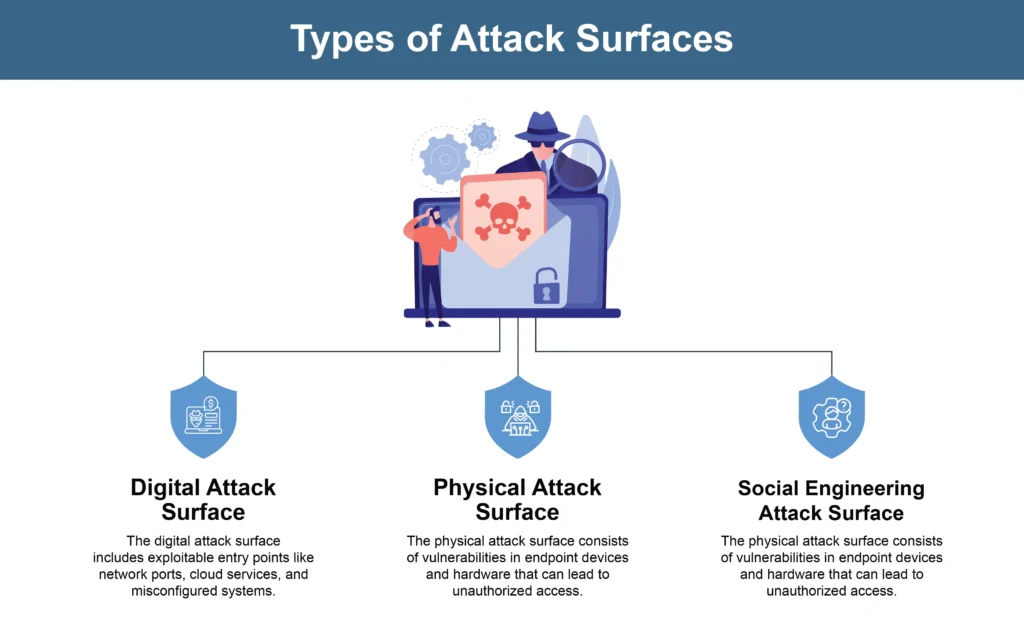
Each category requires distinct security measures to mitigate risks effectively.
Recognizing these different attack surfaces helps organizations implement targeted security strategies to protect their assets.
Check this table for more clarity:
| Attack Surface Type | Description | Key Vulnerabilities | Common Attack Vectors | Mitigation Strategies |
|---|---|---|---|---|
| Digital Attack Surface | Includes all digital entry points that can be exploited, such as network ports, cloud services, and third-party interfaces. |
|
|
|
| Physical Attack Surface | Involves vulnerabilities in endpoint devices and hardware, which can lead to unauthorized access. |
|
|
|
| Social Engineering Attack Surface | Focuses on vulnerabilities related to human behavior, where individuals can be manipulated into compromising security. |
|
|
|
Steps in Conducting an Attack Surface Assessment
An attack surface assessment involves asset discovery and classification, vulnerability identification and prioritization, and continuous monitoring and threat intelligence.
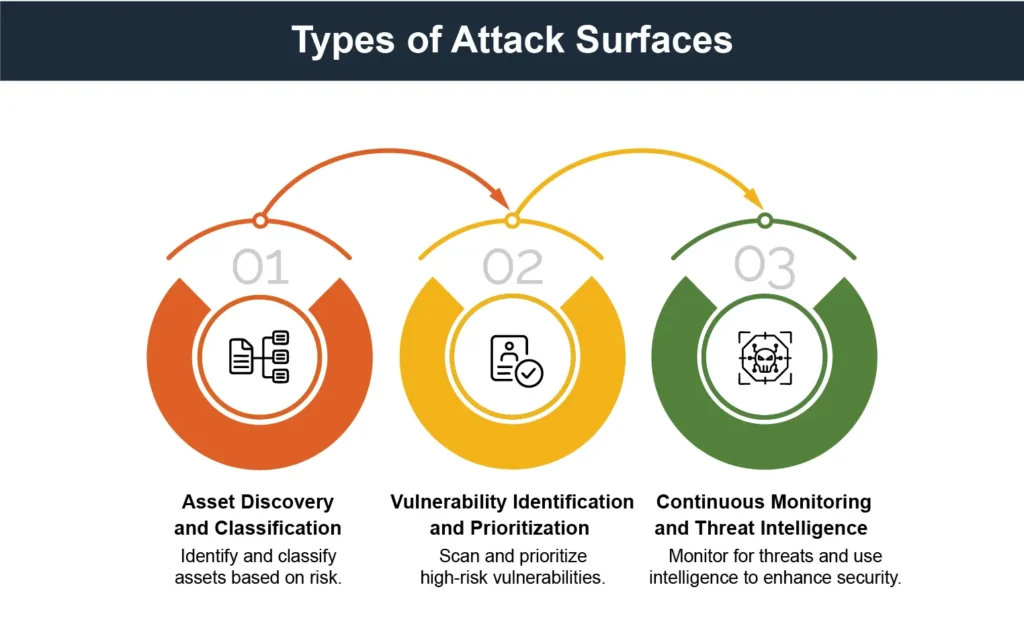
Each of these steps plays a critical role in identifying, analyzing, and mitigating potential vulnerabilities within an organization’s attack surface.
-
Asset Discovery and Classification
Asset discovery involves identifying all digital assets and maintaining an updated inventory of internet-facing IT resources. Automated tools continuously detect network-connected devices, applications, and shadow IT, classifying them by risk level to prioritize security measures, especially for high-risk cloud services.
-
Vulnerability Identification and Prioritization
Vulnerability identification scans for unpatched software and other exploitable weaknesses. High-risk assets are prioritized based on their vulnerabilities and security risks, enabling efficient remediation efforts using insights from cybersecurity data to compare asset risk to organizational risk tolerance.
-
Continuous Monitoring and Threat Intelligence
Continuous attack surface monitoring detects new vulnerabilities and threats in real-time, while cyber threat intelligence improves visibility into the threat landscape, enhancing preparedness and response strategies to protect IT infrastructure from potential cyber-attacks.
Tools and Techniques for Attack Surface Assessment
Attack surface analysis involves identifying, assessing, and reducing points of entry for attackers.
The tools and techniques for attack surface assessment include:
- Red Teaming and Penetration Testing: Simulate attacks to identify security weaknesses. Penetration testing specifically simulates real-world cyberattacks to uncover vulnerabilities.
- Automated Attack Surface Discovery Tools: Continuously scan the infrastructure for external assets, vulnerabilities, and misconfigurations.
- Vulnerability Scanners: Assess known weaknesses in software, networks, and applications. Provide risk reports to help prioritize remediation efforts.
Organizations using attack surface risk management tools report improved security postures through continuous asset discovery and vulnerability testing.
Reducing Your Attack Surface
Reducing the attack surface requires implementing various strategies and security controls to mitigate potential vulnerabilities. This includes measures such as network segmentation, enforcing access controls, and conducting regular security testing and audits.
-
Implementing Network Segmentation
Network segmentation divides a network into smaller, isolated segments to enhance security and control. It creates barriers that prevent attackers from moving laterally within the network, reducing the risk of widespread compromise. Even if an attacker gains access to one segment, they are unable to freely access the entire network.
-
Enforcing Access Controls
The principle of least privilege (PoLP) limits user access to only what is necessary for their role, minimizing the risk of unauthorized access. In cloud environments, enforcing strict access controls is especially crucial to prevent vulnerabilities from over-privileged access. Techniques like encryption, role-based access controls, and regular backups further protect sensitive data.
-
Regular Security Testing and Audits
Regular security testing, such as penetration testing and audits, helps organizations proactively identify and fix vulnerabilities. Continuous penetration testing, for example, allows real-time detection of security weaknesses. Additionally, manual triaging of security alerts helps prioritize critical vulnerabilities, reducing alert fatigue and improving response efforts.
Employing these strategies significantly enhances an organization’s security posture and reduces the risk of cyberattacks.
How Fidelis Elevate® Enhances Attack Surface Management
Fidelis Elevate® is a unified Extended Detection and Response (XDR) Platform offering multi-layered security. It covers endpoint, network, active directory, DLP (Data Loss Prevention), and deception technology, providing comprehensive security across all digital assets.
The main features of Fidelis Elevate® for effective attack surface management are:
- Deception Technology: The platform uses deception technology to create false pathways, helping security teams gather intelligence and respond quickly to attacks. This proactive approach allows organizations to stay ahead of threats and mitigate risks effectively.
- Proactive Threat Hunting: Fidelis XDR supports proactive threat hunting, enabling security teams to identify and neutralize advanced threats that may exploit blind spots within the network or on endpoints.
- Comprehensive Protection Across Layers: By integrating multiple security layers such as endpoint, network, and cloud security, Fidelis Elevate® enhances attack surface management, ensuring comprehensive protection for all digital assets.
- Real-Time Intelligence: With continuous monitoring and the ability to deploy risk-aware deception, Fidelis actively detects and mitigates threats across your attack surface, ensuring that potential entry points are managed effectively.
Overall, Fidelis Elevate® empowers organizations with a proactive, multi-layered security approach, enhancing attack surface management and ensuring robust protection against evolving threats across all digital environments.
Conclusion
In today’s complex threat landscape, organizations must employ systematic strategies to safeguard their digital assets through risk assessment and attack surface assessment. Regular assessments enable organizations to address vulnerabilities before attackers can exploit them. Frequent attack surface evaluations enhance compliance efforts, resource allocation, and overall security strategy. The increasing complexity of IT environments necessitates tools that provide ongoing visibility and actionable insights. A structured approach to attack surface management transforms an organization’s security posture from reactive to proactive.
See how Fidelis Elevate® empowers your organization:
- Real-time cyber terrain mapping for full visibility
- Prioritize critical assets and detect threats faster
- Proactive defense with deception networks and risk analysis
Frequently Ask Questions
What is an attack surface assessment?
An attack surface assessment is a systematic evaluation aimed at identifying potential vulnerabilities within an organization to enhance its security measures. This process focuses on identifying, monitoring, and mitigating risks associated with the organization’s assets to minimize the likelihood of cyberattacks.
What are the different types of attack surfaces?
The different types of attack surfaces include digital, physical, and social engineering. Understanding these categories is essential for implementing appropriate security measures to mitigate risks.
How can organizations reduce their attack surface?
Organizations will be able to effectively reduce attack surfaces by implementing network segmentation, enforcing strict access controls, and conducting regular security testing and audits. These strategies significantly minimize vulnerabilities and strengthen overall security.
What role does continuous monitoring play in attack surface management?
Continuous monitoring plays a vital role in attack surface management by enabling real-time detection of vulnerabilities and threats. This proactive approach ensures organizations can swiftly adapt to evolving risks and maintain ongoing visibility into their IT infrastructure.
How does Fidelis Elevate® enhance attack surface management?
Fidelis Elevate® enhances attack surface management by providing multi-layered security across endpoints, networks, active directories, and more while leveraging deception technology, proactive threat hunting, and real-time intelligence to detect, mitigate, and manage risks effectively across all digital assets.



