Cybersecurity Solutions to Meet Every Need
Cybersecurity Solutions to Meet Every Need
Cybersecurity Solutions to Meet Every Need
There's a Reason the Most Important Data on Earth is protected by Fidelis
of the 6 US Military Branches Defended
of the 10 Largest US Government Agencies Protected
Year-to-Date High Severity Malware Threats Identified
Year-to-Date Critical Vulnerability Exploitations Attempts Detected

Fidelis Security has been protecting leading enterprises and government agencies worldwide for over 20 years.
-
7 of the 10 largest US government agencies.
-
5 of the 6 branches of the US military
-
#1 largest cellphone manufacturer in the world
-
#1 largest pharmacy chain in the world
-
#1 largest mobile service provider in the US
-
#1 largest defense contractor in the world
-
#1 largest pharmaceutical company in the world
-
#1 largest convenience store chain in the world
Why are Fidelis Cybersecurity solutions winning against its competitors?
The Fidelis Challenge.
No one sees what we see and we'll prove it
Run Fidelis Elevate, our XDR platform, in your enterprise environment for 30 days. We guarantee we will find threats your current provider has never even seen. If we are wrong, we will pay you $50,000 or donate $50,000 to a children’s charity of your choice.
Products
Discover Our Product
The Fidelis Elevate
Built on a Foundation of AI (Before it was Cool)
Our customers rely on our AI-driven Fidelis Elevate to:
Predict future attacks before they happen
Stop phishing attempts in real-time
Conduct rapid forensic analysis to confidently respond to present threats
The Fidelis Halo™
Built on a Foundation of AI (Before it was Cool)
Our customers rely on our AI-driven Fidelis Halo™ to:
Predict future attacks before they happen
Stop phishing attempts in real-time
Conduct rapid forensic analysis to confidently respond to present threats

No one sees what we see and we'll prove it
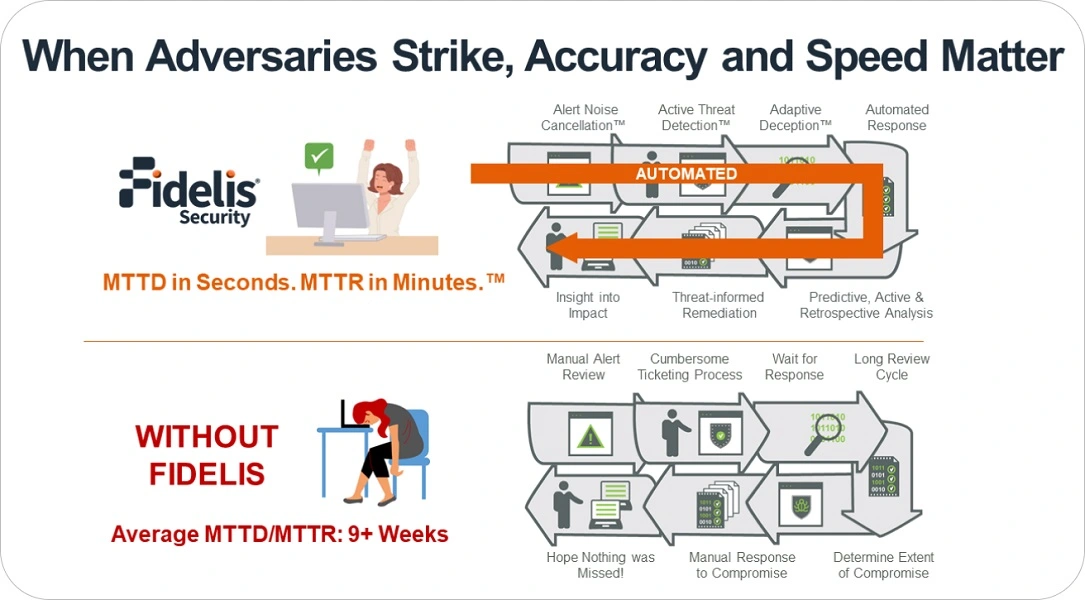
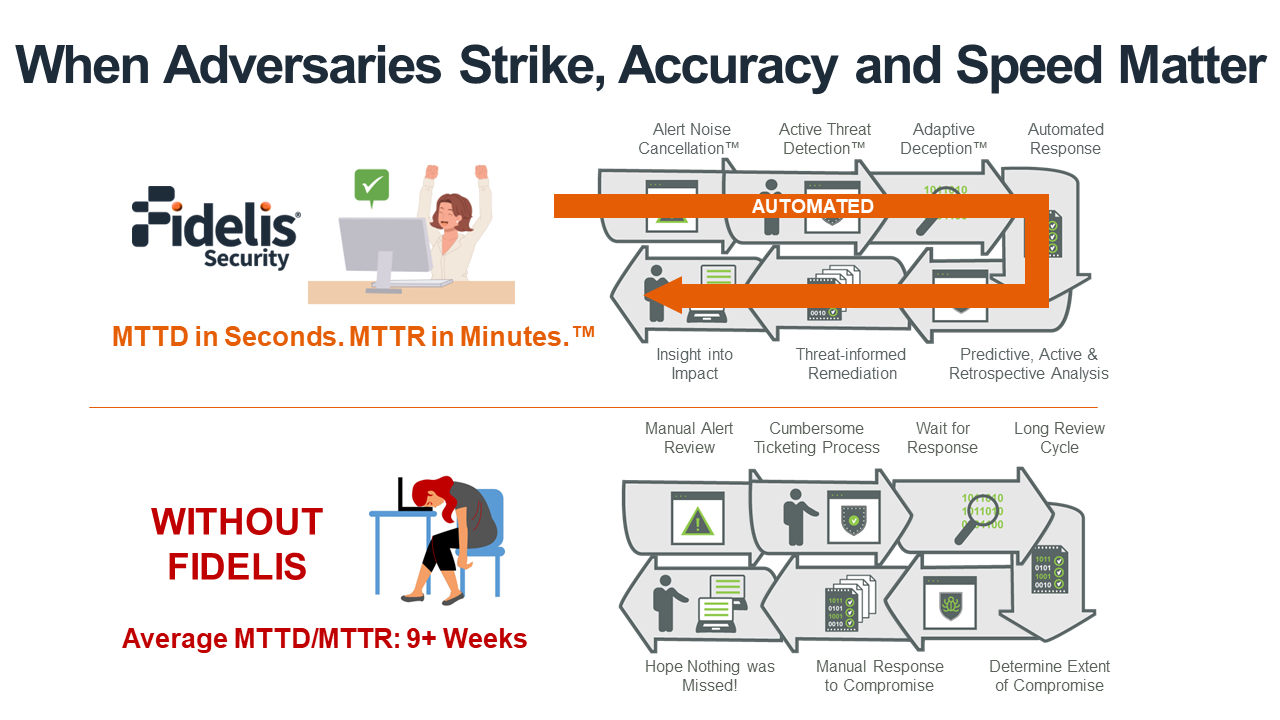
Our customers detect post-breach attacks over 9x faster.
Take the Fidelis Challenge:
Run Fidelis in your environment for 30 days. We guarantee we will find threats your current provider has never even seen. If we are wrong, we will write you a check for $25,000 or donate to a charity of your choice.

Case Study
Global Bank Leaders Reduces Incident Response Time from 10 Days to 5 Hours
This case study discovers how the top 5 global bank leaders reduced incident response time from 10 days to 5 hours. As cyber-attacks continue to rise, the financial industry is on the forefront of the latest methods of detection, remediation, and resolution to threats on their systems. The need for a new cybersecurity solution came […]
....This case study discovers how the top 5 global bank leaders reduced incident response time from 10 days to 5 hours. As cyber-attacks continue to rise, the financial industry is on the forefront of the latest methods of detection, remediation, and resolution to threats on their systems.
The need for a new cybersecurity solution came up when the monitoring of email and internet traffic was of the essence for the organization, but the bank was limited in the volume of traffic that it could process. After careful deliberation the team decided that Fidelis was the only cybersecurity vendor that provided the indexing needed to query Exchange data on the fly.
Read the full case study to know more about how Fidelis protected this Global Bank Leader.
Case Study
Fidelis Deception® fortifies Children’s Hospital with proven ROI
The hospital entrusted Fidelis Security® for their network security and now it works round the clock to maintaining the privacy of PHI and other sensitive data by leveraging advanced offensive deception technology, threat analysis, and visibility.....
Children’s Hospital upgrades network security with Fidelis Deception®
“Fidelis Deception® takes our network security to the next level,” the Hospital’s, IT Security Architect says.
This North American Hospital Children’s Hospital has nearly 5,000 staff members and volunteers and handles over 500,000 patient visits a year. The hospital’s information systems comprise of approximately 7,000 endpoints and servers used daily by thousands of users.
The hospital was no stranger to high profile cyber-attacks, breaches, and the rigid network security and data security requirements dictated by HIPAA and other regulations. The hospital needed a solution that would not impact the network’s performance and burden the security staff with masses of false positives or data logs.
They entrusted Fidelis Deception® to do the job. Today it works round the clock to maintaining the privacy of PHI and other sensitive data by leveraging advanced offensive deception technology, threat analysis, and visibility.
Read the case study to know more about how Fidelis was able to achieve this.
Case Study
Leading Tech Company Increases Network Visibility with Fidelis
says the company’s Information Protection Principal....
Fidelis Deception enables Tech Company to get wider Visibility
A leading technology solutions manufacturer with over 5,000 employees needed a solution that would keep up with their growing needs as it was becoming increasingly difficult to control access and protect data.
The company needed a solution that would allow deep and wide visibility into and across their network, enabling them to understand the way traffic flows within the organization and to the Internet.
In this case study we dive into how Fidelis Deception protected their environment and helped them avert Zero-day and APT attacks. Fidelis Deception seamlessly maps all the communication channels across and beyond the organization, tracking the flows of internal and external network traffic to expose shadow IT tools, home-grown apps, unqualified IoT devices and more.
“If you don’t see bad stuff in your network, you’re not using the right tools. Attackers are already inside. Fidelis Deception* knows where to look and how to show you the right way to eradicate threats.” -The company’s Information Protection Principal
Read the full case study to know how Team Fidelis achieved this protection.
What Our Client Say About Our Cybersecurity Solutions
I know it’s unlikely to ever be 100% secure, but QGroup and Fidelis give me confidence that our security is at the highest possible level.
Fidelis achieves Gold in Cybersecurity from Merit Awards: “...a reflection of the innovations and technology advancements the industry has made over the last year.”
Check Out Our Recent Reports

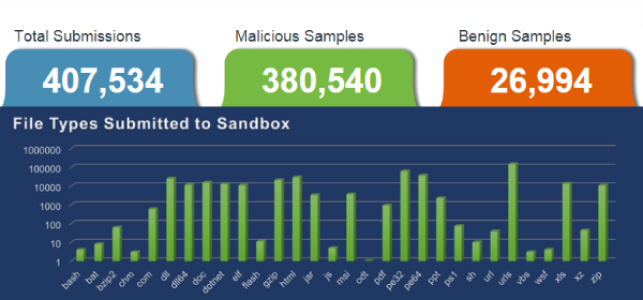
Cyber Threat Intelligence Report – June 2023
Uncovering Critical Vulnerabilities and Malicious Tactics The Fidelis Security Threat Intelligence Summary highlights the most critical emerging vulnerabilities and malware.

Cyber Threat Intelligence Report – May 2023
Stay informed on May 2023 cybersecurity incidents with Fidelis Security’s Threat Intelligence Report. Explore ransomware, critical flaws, and malware attacks.

Cyber Threat Intelligence Report – April 2023
Explore the major cybersecurity threats of April 2023 including state-sponsored threats, ransomware attacks, and more with Fidelis Security TRT.
Recent Posts

Multi-layered Defense: Enhancing Security with Fidelis Active Directory Intercept™
Discover the power of Fidelis Active Directory Intercept for a robust multi-layered defense. Safeguard your AD infrastructure against evolving cyber threats…

New MOVEit Vulnerability: What to Do NOW to Protect Your Organization
On May 31, 2023 Progress Software disclosed a SQL injection vulnerability (CVE-2023-34362) in the MOVEit Transfer that could lead to escalated privileges
How to Spot and Stop Active Directory Attacks Faster – Part 2
In the previous blog, we described how to catch attackers targeting Active Directory (AD) in the reconnaissance stage, which is

Beyond Cybersecurity: The Role of Cyber Resiliency in Network Defense
Is your organization’s security strategy prepared to face modern cyber threats? Cyber threats are evolving at an unprecedented pace, demanding
Blog
Our Recent Blog

Buy Smart: Your Guide for Buying a Network Traffic Analysis Solution
Gartner recently released its Market Guide for Network Traffic Analysis (NTA), an invaluable tool for organizations looking to assess and

What is Extended Detection and Response?
Discover the power of Extended Detection and Response (XDR) in modern cybersecurity. Learn how Fidelis XDR proactively defend your enterprise against threats!

June 2023 Threat Intelligence Summary
When threats emerge, the Fidelis Security Threat Research team (TRT) is ready. Each month, the Threat Intelligence Summary examines the
Policy assignments work surprisingly well. I can just set policies for our assets and servers, and those policies apply to any new instances that we spin up.