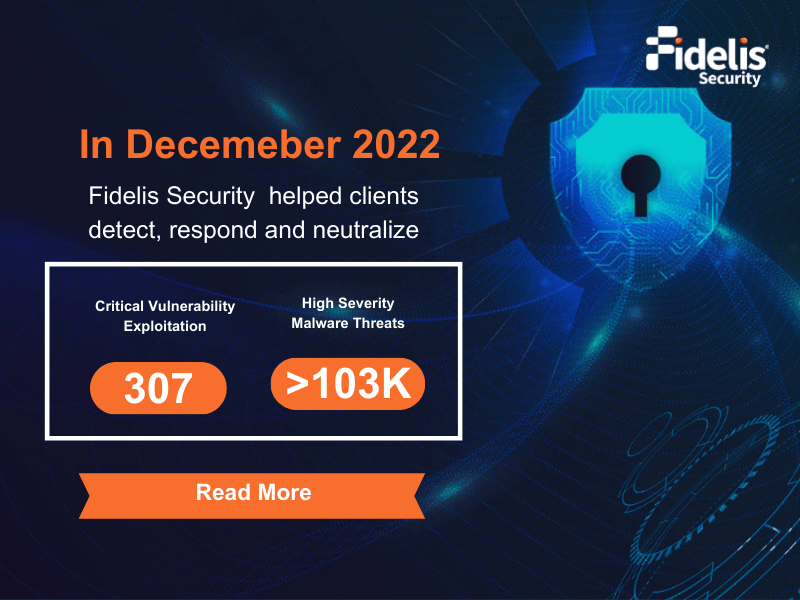
Beyond Cybersecurity: The Role of Cyber Resiliency in Network Defense
Is your organization’s security strategy prepared to face modern cyber threats? Cyber threats are evolving at an unprecedented pace, demanding organizations to align their security strategies accordingly. Traditional security methods